- Community Home
- >
- Servers and Operating Systems
- >
- HPE BladeSystem
- >
- BladeSystem - General
- >
- Re: VC + ESXi with transparent Firewall = package ...
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2012 02:52 AM - edited 04-24-2012 02:56 AM
04-24-2012 02:52 AM - edited 04-24-2012 02:56 AM
VC + ESXi with transparent Firewall = package storm?
Hi there,
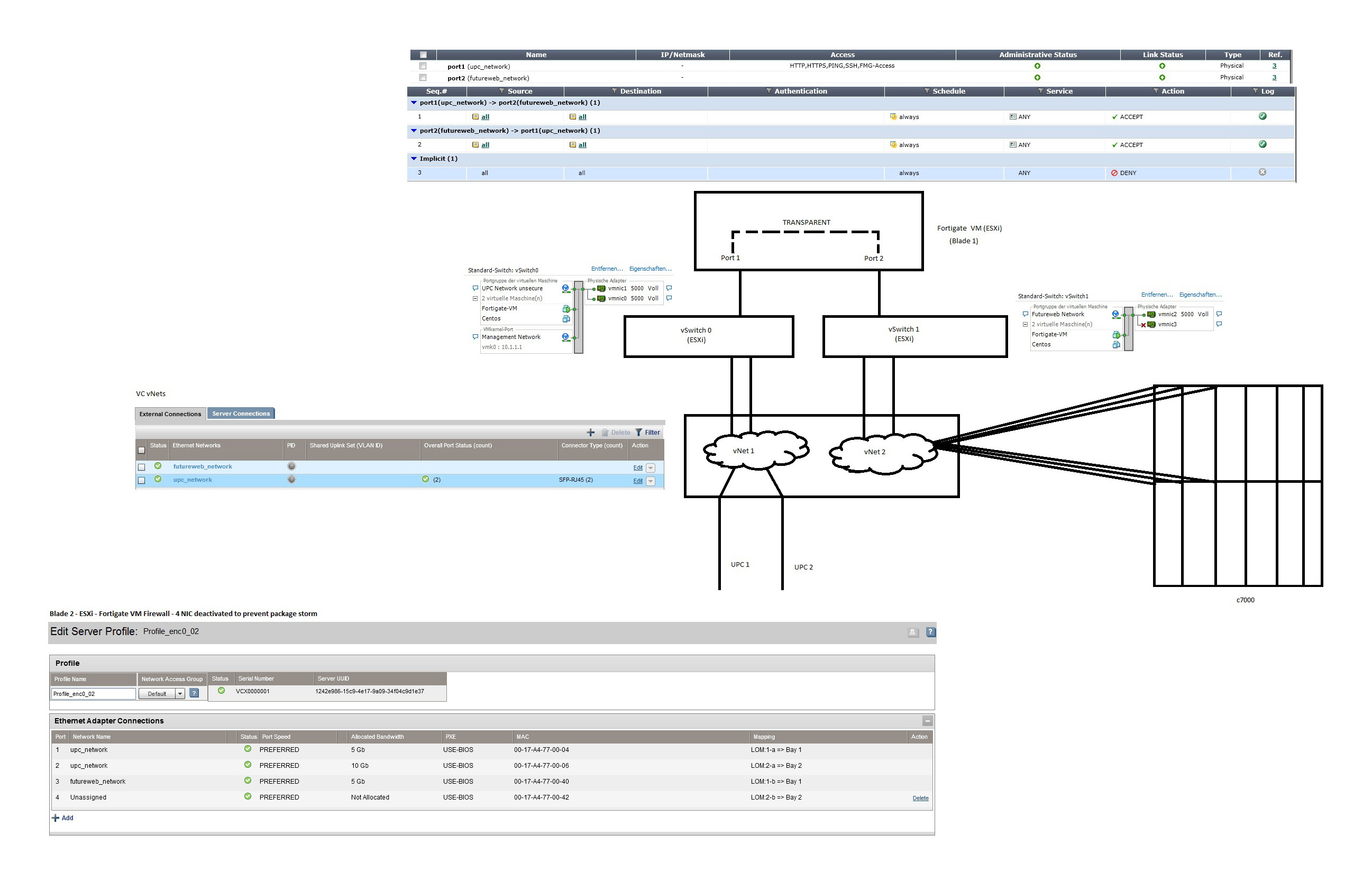
we are just in the process of migrating our stuff to a new C7000 + Virtual Connect (3.51).
What we try to do:
We got 2 uplinks (to the internet) from our DC.
UPL1 goes to VC1, UPL 2 goes to VC2. Booth assigned to vNet "upc_network", connection mode Failover. - this is the "outer" vNet
Also there is a second vNet "futureweb_network" - which should be behind the firewall server for our internal net
On Blade 1 we got a VMWARE ESXi 5 with an virtualized Fortigate Firewall VM in transparent mode.
That's how VC connects to this Server (I explain the deactivated Port 4 later):
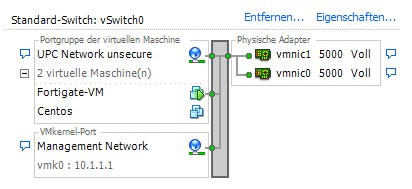
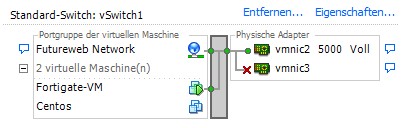
UPC network connects to our first virtual ESXi switch:
Our Fortigate VM Firewall Port 1 connects to this switch and transparent filter/forward/scan all the traffic from this Port to Port 2 - which is connected to our vNet "futureweb_network"
All other Blades are connected to the vNet "futureweb_network"
I made a quick drawing of this Topo in MS Paint:
Everything works quite good - except when I activate PORT 4 for our Firwall Server. As soon as I activate the Port (within "futureweb_network" vNet the whole net goes crazy - loose all pings / everything is dead ... I guess it's causing a package storm. But I can't find WHERE we made the failure in this topo?!? Just want to bring every traffic from the outside through our Firewall into the inner net ...
I hope someone of you can help me on this! :)
Thank you, bye from Austria
Andreas
- Tags:
- firewall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2012 01:33 AM
04-26-2012 01:33 AM
Re: VC + ESXi with transparent Firewall = package storm?
when you assign futureweb vnet to Port 4, you potentially create this loop if it's broadcast/multicast traffic.
VC-1 ---> vswitch0---->Fortigate vm port 1---> Fortigate vm port 2--->vswitch1 vmnic3-->VC-2--->inernal stacking link between VC modules on port X7 and X8----> VC-1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2012 02:23 AM - edited 04-26-2012 05:05 AM
04-26-2012 02:23 AM - edited 04-26-2012 05:05 AM
Re: VC + ESXi with transparent Firewall = package storm?
mhm - alright - I thought those VC vNet are completely seperated and won't exchange any packets?
But I always saw booth VC Controllers "as one"
What would you suggest to get this topo working? (with connection to booth VC for redundancy)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2012 07:39 AM
04-26-2012 07:39 AM
Re: VC + ESXi with transparent Firewall = package storm?
actually what I said last night may not be right. It was very late into night and I didn't have enough time to think over.
I'd like to get more info in order for me to analyze
1) what's your centos blade server profile config? Do they only have one vnet future-web assigned?
2) I see there is a centos vm have two NICs, one to vswitch0 and one to vswitch1. what's the reason for this?
3) what's your vswitch0 and vswitch1 teaming method? are you using vswitch default based on original port ID?
i won't have time to reply today and likely tomorrow and may have to wait to weekend for some time
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2012 08:26 AM
04-26-2012 08:26 AM
Re: VC + ESXi with transparent Firewall = package storm?
hehe - alright - no prob! ;-)
1) the centos blade (real server - no VM) is only connected to "futureweb" vNet. (But the storm also happens when this Server is not linked to "Futureweb" (not assigned anywhere) - so there is only the Firewall linked to the Futureweb vNet and nothing other present in the futureweb vNet.
2) centos VM - this was only a test - we replaced the Firewall with a Centos and made a simple bridge there ... tried if the Fortigate is the problem ... but storm also happened there ... this VM is normally DOWN
3) tried it with "original port id", "source mac" and also failover - happened with all three configurations
thx, bye from Austria
Andreas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2012 12:43 AM
05-01-2012 12:43 AM
Re: VC + ESXi with transparent Firewall = package storm?
i haven't been able to see the loop as well. are you saying that for vswitch 1, even if you set NIC team and active/standby, you still have the same problem? if so, it's sort of weird. may want to open a support case to track down.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2012 04:52 AM
05-02-2012 04:52 AM
Re: VC + ESXi with transparent Firewall = package storm?
- port ID
- IP hash
- source MAC
- failover
also we had the second NIC in standby adapter und "not used" adapters ...
in all those constellations the broadcast storm happens.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-15-2012 09:02 AM
08-15-2012 09:02 AM
Re: VC + ESXi with transparent Firewall = package storm?
Just as a follow up, it seems to be an issue with the VMWare VSwitch and Promisious mode that can't as of now really be changed or won't or can't be corrected by VMware. I read at another forum post about a similar problem, that the Cisco VSwitch would be able to handle it, but we never tried that. Unfortunatly I don't have the link handy.
So no real possible solution with out of the box VMWare here when working with a VM Firewall and trying to have HA handled by VMware. All works fine when using one in/one out LAN connection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-15-2012 04:18 PM
08-15-2012 04:18 PM
Re: VC + ESXi with transparent Firewall = package storm?
thanks for the update. Great to know the result of this behavior.