- Community Home
- >
- Servers and Operating Systems
- >
- Servers & Systems: The Right Compute
- >
- Securing your data-at-rest with HPE ProLiant Secur...
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Receive email notifications
- Printer Friendly Page
- Report Inappropriate Content
Securing your data-at-rest with HPE ProLiant Security and Utimaco ESKM
Cyberattacks are on the rise, and organizations must look to minimize potential impact of a security incident or compromised data protection. Encryption has emerged as a best practice and in many cases a requirement for protecting sensitive and critical data for many enterprises, but without proper management, encryption can quickly become complex and costly.

In my recent blog, A secure supply chain: the foundation to zero trust, I discuss the importance of having a secure supply chain to ensure authentic and tamper free servers—and how any disruptions and risk to the integrity of an enterprise data center can lead to breach or data-loss, resulting in long lasting and damaging operational, financial, and brand consequences. The same is true for a data-breach and loss of any sensitive data-at-rest within your databases, file systems and storage infrastructure.
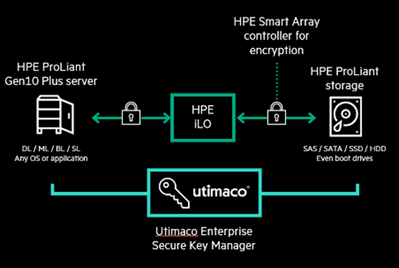
Hewlett Packard Enterprise (HPE) delivers the world’s most secure industry-standard server portfolio with an enhanced 360-degree view to security that begins in the manufacturing supply chain and concludes with a safeguarded, end-of-life decommissioning.
While zero trust is a lifecycle effort, the key principles are built into everything HPE designs, and is why HPE is best suited to be your trusted security partner, helping you navigate and implement a cyber resilient infrastructure for data protection. HPE servers with Utimaco ESKM[1] provide a complete solution, unifying and automating an organization’s encryption controls by securely creating, protecting, serving, controlling, and auditing access to business-and compliance-critical encryption keys.
The HPE data-at-rest solution provides security by an encryption technique so that – even in the case of a breach – your sensitive data is always protected. HPE servers with Utimaco ESKM deliver outstanding performance, efficient TCO while protecting your sensitive data from intrusion.
To learn more visit www.hpe.com/security/compute
[1] Enterprise Secure Key Manager (ESKM) is a complete solution for generating, storing, serving, controlling, and auditing access to data encryption keys.
Ruben_Ramirez
Ruben Ramirez is a WW Product Marketing Manager for Hewlett Packard Enterprise. As an experienced product marketing professional serving enterprise technology companies, Ruben excels at bringing new technologies to market, and helping to create compelling value propositions for customer business needs. Currently Ruben is responsible for bringing to market HPE composable infrastructure, and the world’s most secure industry standard server technologies.
- Back to Blog
- Newer Article
- Older Article
- Dale Brown on: Going beyond large language models with smart appl...
- alimohammadi on: How to choose the right HPE ProLiant Gen11 AMD ser...
- Jams_C_Servers on: If you’re not using Compute Ops Management yet, yo...
- AmitSharmaAPJ on: HPE servers and AMD EPYC™ 9004X CPUs accelerate te...
- AmandaC1 on: HPE Superdome Flex family earns highest availabili...
- ComputeExperts on: New release: What you need to know about HPE OneVi...
- JimLoi on: 5 things to consider before moving mission-critica...
- Jim Loiacono on: Confused with RISE with SAP S/4HANA options? Let m...
- kambizhakimi23 on: HPE extends supply chain security by adding AMD EP...
- pavement on: Tech Tip: Why you really don’t need VLANs and why ...
-
COMPOSABLE
77 -
CORE AND EDGE COMPUTE
146 -
CORE COMPUTE
131 -
HPC & SUPERCOMPUTING
132 -
Mission Critical
86 -
SMB
169



