- Community Home
- >
- Networking
- >
- Switching and Routing
- >
- Comware Based
- >
- Re: 5130 Comware packet-filter with PBR not work.
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2018 02:03 AM
06-07-2018 02:03 AM
5130 Comware packet-filter with PBR not work.
Dear,
I want to apply filtering and policy-based routing with the following device.
HPE 5130-24G-4SFP+ EI (JG932A) HPE Comware Software, Version 7.1.045, Release 3109P14
I want to do the things are as follows.
if ( src 192.168.199.0/24 and dst 192.168.0.0/24 ) {
drop packet
} else {
next hop 192.168.251.1
}
I tried below config, but not work. Any packets are passed from 192.168.199.0/24 to 192.168.0.0/24.
acl number 3000
rule 10 permit ip destination 192.168.0.0 0.0.0.255
policy-based-route pbr1 deny node 10
if-match acl 3000
policy-based-route pbr1 permit node 20
apply next-hop 192.168.251.1
acl number 3199
rule 100 deny ip destination 192.168.0.0 0.0.0.255
rule 900 permit ip
interface Vlan-interface199 ip address 192.168.199.1 255.255.255.0 packet-filter 3199 inbound ip policy-based-route pbr1
Are there any good ideas?
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2018 01:06 AM
06-08-2018 01:06 AM
Re: 5130 Comware packet-filter with PBR not work.
You need "if-match" and "apply" to be in one node. Also if you have deny mode in your node the apply clause is not executed, if I understand your requirement correctly you want traffic towards 192.168.0.0 to go via 192.168.251.1 therefore permit should be used
acl number 3000 rule 10 permit ip destination 192.168.0.0 0.0.0.255 # policy-based-route pbr1 permit node 10 if-match acl 3000 apply next-hop 192.168.251.1
#
interface Vlan-interface199
ip address 192.168.199.1 255.255.255.0
ip policy-based-route pbr1
I'm not sure about ACL, it looks ok
check this out:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2018 02:37 AM - edited 06-08-2018 02:53 AM
06-08-2018 02:37 AM - edited 06-08-2018 02:53 AM
Re: 5130 Comware packet-filter with PBR not work.
Thank you, but that is not my requirement. More details are as follows.
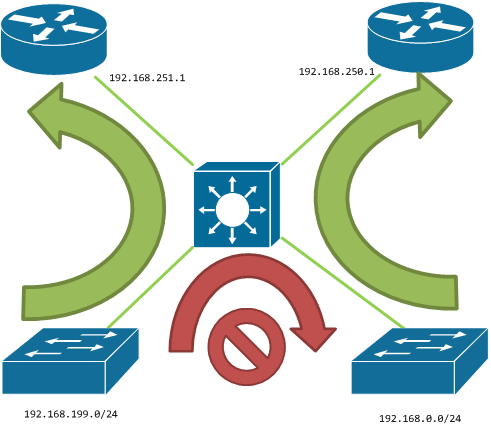
if ( src 192.168.199.0/24 ) {
if ( dst 192.168.0.0/24 ) {
drop packet and not routing
} else {
default gateway 192.168.251.1
}
} else {
default gateway 192.168.250.1
}
However, the following config will not work.
acl number 3000 rule 10 permit ip destination 192.168.0.0 0.0.0.255 policy-based-route pbr1 deny node 10 if-match acl 3000 policy-based-route pbr1 permit node 20 apply next-hop 192.168.251.1 acl number 3199 rule 100 deny ip destination 192.168.0.0 0.0.0.255 rule 900 permit ip interface Vlan-interface199 ip address 192.168.199.1 255.255.255.0 packet-filter 3199 inbound ip policy-based-route pbr1 interface Vlan-interface1 ip address 192.168.0.1 255.255.255.0 interface Vlan-interface250 ip address 192.168.250.2 255.255.255.0 interface Vlan-interface251 ip address 192.168.251.2 255.255.255.0 ip route-static 0.0.0.0 0 192.168.250.1
It works only with "apply" in one node. This "pbr1 deny node 10" suggests "not apply next-hop".
In addition, it is confirmed that "packet-filter filter route" and "all (default)" do not work either way.
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2018 03:30 AM
06-08-2018 03:30 AM
Re: 5130 Comware packet-filter with PBR not work.
Thank you, but that is not my requirement. More details are as follows.
if ( src 192.168.199.0/24 ) {
if ( dst 192.168.0.0/24 ) {
drop packet and not routing
} else {
default gateway 192.168.251.1
}
} else {
default gateway 192.168.250.1
}
However, the following config will not work.
acl number 3000 rule 10 permit ip destination 192.168.0.0 0.0.0.255 policy-based-route pbr1 deny node 10 if-match acl 3000 policy-based-route pbr1 permit node 20 apply next-hop 192.168.251.1 acl number 3199 rule 100 deny ip destination 192.168.0.0 0.0.0.255 rule 900 permit ip interface Vlan-interface199 ip address 192.168.199.1 255.255.255.0 packet-filter 3199 inbound ip policy-based-route pbr1 interface Vlan-interface1 ip address 192.168.0.1 255.255.255.0 interface Vlan-interface250 ip address 192.168.250.2 255.255.255.0 interface Vlan-interface251 ip address 192.168.251.2 255.255.255.0 ip route-static 0.0.0.0 0 192.168.250.1
This "pbr1 deny node 10" suggests "not apply next-hop". So, it works only with "apply" in one node.
In addition, it is confirmed that "packet-filter filter route" and "all (default)" do not work either way.
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2018 06:52 AM - edited 06-08-2018 06:57 AM
06-08-2018 06:52 AM - edited 06-08-2018 06:57 AM
Re: 5130 Comware packet-filter with PBR not work.
are all the vlan interfaces that you listed configured on bottom left switch labeled as 192.168.199.0/24?
and is it the same switch on which you are trying to configure PBR?
acl number 3000 rule 10 permit ip destination 192.168.0.0 0.0.0.255 policy-based-route pbr1 deny node 10 if-match acl 3000 policy-based-route pbr1 permit node 20 if-match acl <whatever traffic you want to push via 192.168.251.1> apply next-hop 192.168.251.1
deny mode 10 will behave as follows:
The apply clause is not executed, the
packets will not go to the next policy
node for a match, and will be
forwarded according to the routing
table.
I think PBR might not be the best match for what you are trying to achieve in node 10 you probably should figure how to use ACL to block that traffic
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2018 09:49 PM - edited 06-10-2018 09:53 PM
06-10-2018 09:49 PM - edited 06-10-2018 09:53 PM
Re: 5130 Comware packet-filter with PBR not work.
Thank you,
are all the vlan interfaces that you listed configured on bottom left switch labeled as 192.168.199.0/24?
The interface gi1/0/7 connected bottom left switch.
interface GigabitEthernet1/0/7 port access vlan 199
and is it the same switch on which you are trying to configure PBR?
The switch on the bottom left and the switch that is trying to configure PBR are different devices.

deny mode 10 will behave as follows:
The apply clause is not executed, the
packets will not go to the next policy
node for a match, and will be
forwarded according to the routing
table.
That is exactly what I want. If I forcefully write acl to node 20, it will look like this.
acl number 2000 rule 0 permit policy-based-route pbr1 permit node 20 if-match acl 2000 apply next-hop 192.168.251.1
But I think the problem is not that PBR does not work, ACL does not work properly.
I think PBR might not be the best match for what you are trying to achieve in node 10 you probably should figure how to use ACL to block that traffic
I so think too of course, but ACL will not work if set with PBR.
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2018 01:06 AM
06-11-2018 01:06 AM
Re: 5130 Comware packet-filter with PBR not work.
for example of ping 192.168.199.0/24 to 192.168.0.0/24.
Client-199>ping 192.168.1.11
Pinging 192.168.1.11 with 32 bytes of data:
Reply from 192.168.1.11: bytes=32 time=2ms TTL=62
Reply from 192.168.1.11: bytes=32 time=1ms TTL=62
Reply from 192.168.1.11: bytes=32 time=3ms TTL=62
Reply from 192.168.1.11: bytes=32 time=3ms TTL=62
Ping statistics for 192.168.1.11:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 3ms, Average = 2ms<hpe5130>reset packet-filter stat int vlan199 in
<hpe5130>display packet-filter stat int vlan199 in Interface: Vlan-interface199 In-bound policy: ACL 3199, Hardware-count From 2018-06-11 16:24:55 to 2018-06-11 16:25:04 rule 100 deny ip destination 192.168.0.0 0.0.0.255 counting (4 packets) rule 900 permit ip logging counting Totally 0 packets permitted, 4 packets denied Totally 0% permitted, 100% denied
counting "denied" by packet-filter, but ping passed and packet-filter not working. what's goin on I wonder.
confirm routing to external network by next-hop 192.168.251.1, there are no problem.
Client-199>ping 8.8.8.8
Pinging 8.8.8.8 with 32 bytes of data:
Reply from 8.8.8.8: bytes=32 time=4ms TTL=54
Reply from 8.8.8.8: bytes=32 time=3ms TTL=54
Reply from 8.8.8.8: bytes=32 time=3ms TTL=54
Reply from 8.8.8.8: bytes=32 time=2ms TTL=54
Ping statistics for 8.8.8.8:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 2ms, Maximum = 4ms, Average = 3msRouter2# sh ip napt trans icmp Prot Inside Address:Port Outside Address:Port Dest Address:Port Time icmp 192.168.199.198:1 nnn.nnn.nnn.nnn:1 8.8.8.8:0 60
Regards,
