- Community Home
- >
- Networking
- >
- Switching and Routing
- >
- Comware Based
- >
- Re: configure ipsec vpn cisco881 and msr2003 not w...
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2019 01:39 AM - edited 08-07-2019 04:22 AM
08-07-2019 01:39 AM - edited 08-07-2019 04:22 AM
configure ipsec vpn cisco881 and msr2003 not work (
Cannot configure ipsec vpn between cisco881 and msr2003
I ask for help
Phase 1 works, and then no:
cisco800#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
213.213.213.213 212.212.212.212 QM_IDLE 2001 ACTIVE
shema:
host192.168.5.111 <--> 192.168.5.1(cisco881)212.212.212.212 <--> 213.213.213.213(msr2003)192.168.0.1 <--> host 192.168.0.28
map:
Phase 1
Authentication Method PSK
Encryption Scheme IKE
Diffie-Hellman Group Group 2
Encryption Algorithm AES256
Hashing Algorithm sha1
Main or Aggressive Mode Main Mode
Lifetime (for renegotiation) 3600 sec
Phase 2
Encapsulation (ESP or AH) ESP
Encryption Algorithm AES256
Authentication Algorithm sha1
Perfect Forward Secrecy YES
Lifetime (for renegotiation) 86400 sec
Lifesize in KB (for renegotiation) 0
VPN type Site-to-site
Encryption domain 192.168.5.111/32 (local)
Encryption domain 192.168.0.28/32 (remote) </PRE>
config cisco 881
!
crypto isakmp policy 1
encr aes 256
authentication pre-share
group 2
crypto isakmp key QWasZX12 address 213.213.213.213
!
!
crypto ipsec transform-set TS esp-aes esp-sha-hmac
!
crypto map map1 10 ipsec-isakmp
set peer 213.213.213.213
set transform-set TS
match address VPN-TRAFFIC
!
interface FastEthernet4
ip address 212.212.212.212 255.255.255.252
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
crypto map map1
!
interface Vlan1
ip address 192.168.5.1 255.255.255.0
ip nat inside
ip virtual-reassembly
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 212.112.104.5
ip route 192.168.0.28 255.255.255.255 213.213.213.213
!
ip nat inside source list 100 interface FastEthernet4 overload
!
ip access-list extended VPN-TRAFFIC
permit ip host 192.168.5.111 host 192.168.0.28
!
access-list 100 deny ip host 192.168.5.111 host 192.168.0.28
access-list 100 permit ip 192.168.5.0 0.0.0.255 any
!
config MSR2003
interface GigabitEthernet0/0
port link-mode route
ip address 213.213.213.213 255.255.255.252
nat outbound 3000 address-group 1
ipsec apply policy msr
#
ip route-static 192.168.5.111 32 212.212.212.212
#
acl advanced 3000
rule 0 deny ip source 192.168.0.28 0 destination 192.168.5.111 0
rule 2 permit ip source 192.168.1.0 0.0.0.63
#
acl advanced 3001
rule 0 permit ip source 192.168.0.28 0 destination 192.168.5.111 0
#
ipsec anti-replay window 1024
ipsec sa global-duration traffic-based 86400
ipsec sa idle-time 120
#
ipsec transform-set msr
esp encryption-algorithm aes-cbc-128
esp authentication-algorithm sha1
#
ipsec policy-template msr 1
transform-set msr
security acl 3001
remote-address 212.212.212.212
ike-profile msr
reverse-route dynamic
reverse-route preference 10
reverse-route tag 100
#
ipsec policy msr 1 isakmp template msr
#
ike identity address 213.213.213.213
ike nat-keepalive 5
#
ike profile msr
keychain msr
exchange-mode aggressive
local-identity address 213.213.213.213
match remote identity address 212.212.212.212 255.255.255.255
proposal 1
#
ike proposal 1
encryption-algorithm aes-cbc-128
dh group2
#
ike keychain msr
pre-shared-key address 212.212.212.212 255.255.255.255 key simple QWasZX12
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2019 10:48 PM
08-07-2019 10:48 PM
Re: configure ipsec vpn cisco881 and msr2003 not work (
please give a link to ipsec Troubleshooting Guide
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2019 02:27 PM
08-12-2019 02:27 PM
Re: configure ipsec vpn cisco881 and msr2003 not work (
Alex,
Is QWasZX12 really your pre-shared secret in plain text or does the Cisco encrypt it like we do on Comware? If so, you need to know the plaintext secret and put that into the configuration on the MSR. It will then be encrypted in the config file to preserve its secrecy.
I'll look tomorrow for the troubleshooting guide for you. What version of code are you running on the MSR? Can you post the display version output? Thanks!
Regards,
David
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-13-2019 03:46 AM - edited 08-13-2019 05:20 AM
08-13-2019 03:46 AM - edited 08-13-2019 05:20 AM
Re: configure ipsec vpn cisco881 and msr2003 not work (
<msr2003>display version
HP Comware Software, Version 7.1.059, Release 0304P15
Copyright (c) 2010-2015 Hewlett-Packard Development Company, L.P.
HP MSR2003 uptime is 0 weeks, 6 days, 14 hours, 15 minutes
Last reboot reason : User reboot
Boot image: flash:/msr2000-cmw710-boot-r0304p15.bin
Boot image version: 7.1.059P08, Release 0304P15
Compiled Nov 14 2015 13:41:09
System image: flash:/msr2000-cmw710-system-r0304p15.bin
System image version: 7.1.059, Release 0304P15
Compiled Nov 14 2015 13:41:09
Feature image(s) list:
flash:/msr2000-cmw710-security-r0304p15.bin, version: 7.1.059
Compiled Nov 14 2015 13:41:09
flash:/msr2000-cmw710-voice-r0304p15.bin, version: 7.1.059
Compiled Nov 14 2015 13:41:09
flash:/msr2000-cmw710-data-r0304p15.bin, version: 7.1.059
Compiled Nov 14 2015 13:41:09
CPU ID: 0x1
1G bytes DDR3 SDRAM Memory
2M bytes Flash Memory
PCB Version: 3.0
CPLD Version: 2.0
Basic BootWare Version: 1.44
Extended BootWare Version: 1.44
[SLOT 0]AUX (Hardware)3.0, (Driver)1.0, (CPLD)2.0
[SLOT 0]GE0/0 (Hardware)3.0, (Driver)1.0, (CPLD)2.0
[SLOT 0]GE0/1 (Hardware)3.0, (Driver)1.0, (CPLD)2.0
[SLOT 0]CELLULAR0/0 (Hardware)3.0, (Driver)1.0, (CPLD)2.0
[SLOT 2]SIC-4GSW (Hardware)2.0, (Driver)1.0, (CPLD)1.0
Update 13.08.2019
I configured vpn tunnel cisco881 and msr2003.
These were test settings for CISCO.
Now I can’t lift the tunnel with Cisco ASA
The opponent says that he does not see Ipsec packets from me (phase 1 does not work).
Claims that my HP MSR2003 router is not compatible with Cisco ASA Ipsec settings.
Is there an example of an IPSEC tunnel configuration between the Cisco ASA and MSR2003 (COMWARE version 7)?
Or are they really not compatible?
my config MSR2003
interface GigabitEthernet0/0
nat outbound 3000 address-group 1
nat static enable
ipsec apply policy msr
#
acl advanced 3000
rule 1 deny ip source 192.168.5.32 0 destination 10.51.5.5 0
rule 4 permit ip source 192.168.5.0 0.0.0.255
rule 100 deny ip
#
acl advanced 3001
rule 1 permit tcp source 192.168.5.32 0 destination 10.51.5.5 0 destination-port eq 443
#
ip route-static 0.0.0.0 0 213.213.213.125
#
ipsec anti-replay window 1024
ipsec sa global-duration traffic-based 86400
ipsec sa idle-time 120
#
ipsec transform-set msr
esp encryption-algorithm aes-cbc-256
esp authentication-algorithm sha1
#
ipsec policy-template msr 1
transform-set msr
security acl 3001
remote-address 185.185.185.185
ike-profile msr
reverse-route dynamic
reverse-route preference 10
reverse-route tag 100
#
ipsec policy msr 1 isakmp template msr
#
nat address-group 2
#
ike identity address 185.185.185.185
ike nat-keepalive 5
#
ike profile msr
keychain msr
local-identity address 213.213.213.213
match remote identity address 185.185.185.185 255.255.255.255
proposal 1
#
ike proposal 1
encryption-algorithm aes-cbc-256
dh group2
#
ike keychain msr
pre-shared-key address 185.185.185.185 255.255.255.255 key cipher $c$3$d0O$c$3$d0oSv$c$3$d0jNBmAEBPMZU/wdWYCuP/Kf8wO9Lg==
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-13-2019 07:29 AM
08-13-2019 07:29 AM
Re: configure ipsec vpn cisco881 and msr2003 not work (
Alex,
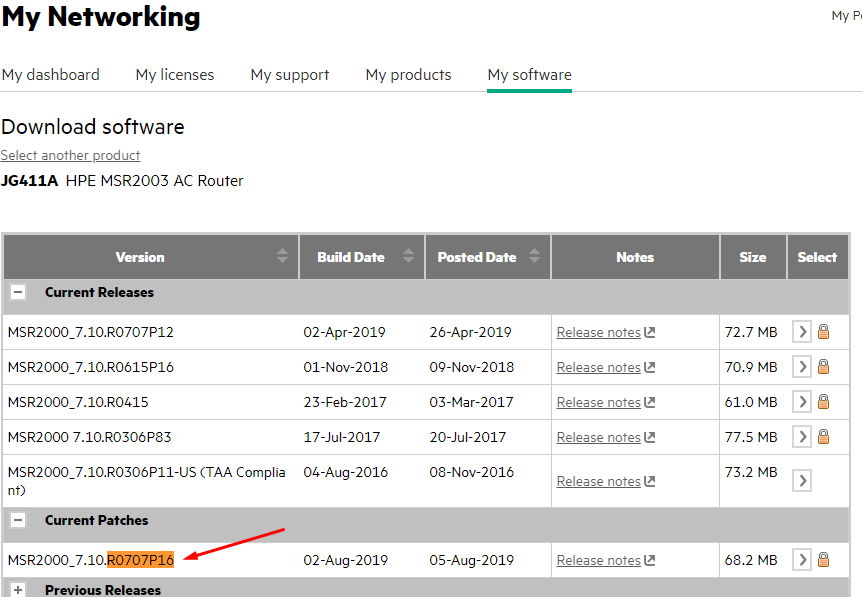
Any chance you can upgrade the code to at least R0615P16? If you aren't using 4G on this MSR you could go to the latest... R0707P16. There have been HUGE changes to that code since it was built in 2015 and the notes are that it only had critical bug fixes and that R0305 was better. But even at that, there were huge changes between then and now.
As for 4G, there is an issue with SIM status in the R0707 code that is going to be fixed shortly for SOME SIM cards. Not all are affected.
Regards,
David
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-13-2019 07:55 AM
08-13-2019 07:55 AM
Re: configure ipsec vpn cisco881 and msr2003 not work (
is this firmware? I need instructions on how to update the firmware please
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-13-2019 08:35 PM - edited 08-15-2019 01:35 AM
08-13-2019 08:35 PM - edited 08-15-2019 01:35 AM
Re: configure ipsec vpn cisco881 and msr2003 not work (
Flash files now
<msr2003>dir
Directory of flash:
0 -rw- 2287 Aug 07 2019 03:35:36 CN63FTY0KX.ak
1 drw- - May 24 2016 16:36:49 diagfile
2 -rw- 735 May 24 2016 19:57:50 hostkey
3 -rw- 387 Aug 13 2019 23:27:23 ifindex.dat
4 drw- - Aug 07 2019 03:46:35 license
5 drw- - Aug 13 2019 23:34:57 logfile
6 -rw- 6380544 Mar 18 2016 16:39:28 msr2000-cmw710-boot-r0304p15.bin
7 -rw- 2629632 Mar 18 2016 16:39:54 msr2000-cmw710-data-r0304p15.bin
8 -rw- 349184 Mar 18 2016 16:39:51 msr2000-cmw710-security-r0304p15.bin
9 -rw- 56171520 Mar 18 2016 16:39:51 msr2000-cmw710-system-r0304p15.bin
10 -rw- 1689600 Mar 18 2016 16:39:52 msr2000-cmw710-voice-r0304p15.bin
11 drw- - May 24 2016 16:36:49 seclog
12 -rw- 591 May 24 2016 19:57:50 serverkey
13 -rw- 12592 Aug 13 2019 23:27:23 startup.cfg
14 -rw- 72680 Aug 13 2019 23:27:24 startup.mdb
262144 KB total (189632 KB free)
This procedure is correct?
<HP>tftp 192.168.1.100 get MSR2000-CMW710-R0707P16.IPE
<HP>boot-loader file flash:/MSR2000-CMW710-R0707P16.IPE
<HP>display boot-loader
<HP>reboot
<HP> display version
Then delete the old firmware files?