- Community Home
- >
- Networking
- >
- IMC
- >
- IMC Compliance Policy
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2021 02:06 PM
11-03-2021 02:06 PM
Trying to figure out how to write compliance policy for ip authorized-mangagers.
I have done the regular expression to verify the ones I need exist but cannot figure out how to make sure there are no others. Seems to work with no issue when I do one line but I have several lines and have issues doing a negate lookforward to find any I dont want. Any guidance you can give is appreciated!
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2021 11:04 AM - edited 11-05-2021 12:19 PM
11-05-2021 11:04 AM - edited 11-05-2021 12:19 PM
Re: IMC Compliance Policy
This issue needs lab intervention, can you log a case with HPE Support by using the below link:
https://support.hpe.com/hpesc/public/home/
Thanks!

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2021 12:43 AM
11-08-2021 12:43 AM
SolutionHello,
I've done this before for one project, and can share some experience in this regard, as it can be one of the more complex use cases for Compliance Policy. The challenge here is that you need to ensure not only all "ip authorized-managers" entries exist in the config, but no additional entries are present that shouldn't be there. In my case there was also a variable IP address in the authorized list (the default gateway of the switch) that needed to be matched.
This can be done with two rules. First, a Basic Strict Match that includes all lines which should exist in the match pattern, including a variable for the default gateway IP, which would look like:
ip authorized-managers 10.10.10.10 255.255.255.255 access manager access-method ssh
ip authorized-managers ${DefaultGateway} 255.255.255.255 access manager access-method ssh
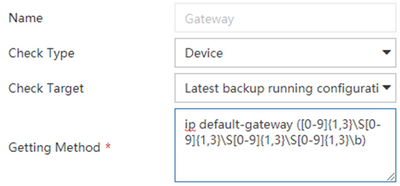
...and so on, in the order these entries are shown in the config. We need to tell IMC how to get this variable information from the device config, which we would do by extracting it from the "ip default-gateway" line using RegEx with a capturing group (
This will look for “ip default-gateway” in the configuration, followed by four octets of 1-3 characters from 0-9, each of which (except the last) ends with a “character that is not a whitespace character”, indicated by \S. Note we cannot use \. instead, because iMC only allows numbers and letters in the capturing group. The last octet should end with a word boundary indicated by \b.
The rule will fail if the device config does not exactly match, so any unexpected “ip authorized-managers” entries between the expected lines would be caught by the rule. The limitation here is that any “ip authorized-managers” lines before or after the expected ones would not cause the rule to fail.
This limitation could be worked around in one of several ways:
• Include the lines before and after the “ip authorized-managers” segment of the configuration. The concern here is that these lines might differ across devices, so it's not reliable.
• Create an additional rule that uses Advanced Match (Excluded) with a negative lookahead in RegEx to ensure no “ip authorized-managers <ip-address>” entries exist that should not be there.
For example:
ip authorized-managers (?!10\.10\.10\.(10|20|30)|192\.168\.10\.(10|20)|Gateway)
Note that the word “Gateway” would need to be replaced with the gateway IP for the devices that need to be checked, in a RegEx format matching the other IP addresses. If you don't need this, it will be simpler for you, and you can just leave it out.
The check would fail if any “ip authorized-managers” lines exist that are not followed by one of the IP addresses in the negative lookahead. The limitation here is that the gateway cannot be filled in automatically using a variable, so a separate policy would need to be created for each set of devices that is using the same gateway.
Hope that makes sense and helps you get the policy working.
Justin
Working @ HPE

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2021 02:42 PM
11-08-2021 02:42 PM
Re: IMC Compliance Policy
Thank you very much!! Worked perfectly!!