- Community Home
- >
- Servers and Operating Systems
- >
- HPE ProLiant
- >
- ProLiant Servers (ML,DL,SL)
- >
- Proliant ML350 Gen9 with latest BIOS still listed ...
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2018 12:04 PM
08-22-2018 12:04 PM
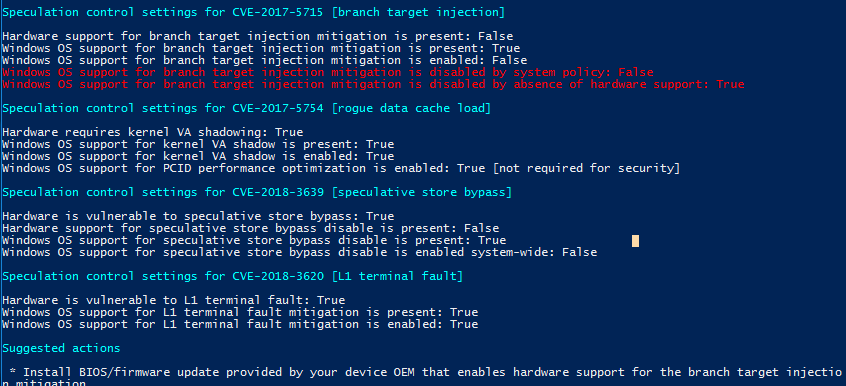
Looking to get a Proliant ML350 Gen9 all patched to protect against the recent speculative threats.
It runs multiple Windows Server 2016 VM's under VMWare (HPE-ESXi-6.5.0-Update1-iso-650.U1.10.1.5.26 (Hewlett Packard Enterprise)).
We updated the BIOS to the latest version of May 20, 2018. P92 Version 2.60
Running a check of the mitigation status in Powershell lists us as still vulnerable to CVE-2017-5715 [branch target injection] due to out of date BIOS/firmware.
Does BIOS P92 Version 2.60 still not protect against this vulnerability?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-27-2018 07:50 PM
08-27-2018 07:50 PM
SolutionPlease review the customer bulletin
https://support.hpe.com/hpsc/doc/public/display?docId=emr_na-a00039267en_us
SUPPORT COMMUNICATION - CUSTOMER BULLETIN
Document ID: a00039267en_us
Version: 15
Bulletin: (Revision) HPE ProLiant, Moonshot and Synergy Servers - Side Channel Analysis Method Allows Improper Information Disclosure in Microprocessors (CVE-2017-5715, CVE-2017-5753, CVE-2017-5754)
For CVE-2017-5715 mitigation, both OS Update and microcode update are required.
Name CVE Number OS Update Required Microcode Required
Variant 1 Spectre CVE-2017-5753 Yes No
Variant 2 Spectre CVE-2017-5715 Yes Yes
Variant 3 Meltdown CVE-2017-5754 Yes No
Review VMware article for more details
https://kb.vmware.com/s/article/52245
VMware Response to Speculative Execution security issues, CVE-2017-5753, CVE-2017-5715, CVE-2017-5754, and CVE-2018-3693 (aka Spectre and Meltdown) (52245)
Action Requested
==================
Update Bios - 2.60
Update OS using VMware-ESXi-6.5.0-Update1-7388607-HPE-650.U1.10.2.0.23-Feb2018.iso
Run the scan and if the issue still persists , Log a case with HPE Support.
NOTE: I am an HPE Employee
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2018 01:56 PM
08-28-2018 01:56 PM
Re: Proliant ML350 Gen9 with latest BIOS still listed as vulnerable to CVE-2017-5715
Had to bump the VMWare OS to HPE ESXi 6.5.0 Update 2, but that brought the mitigations online as we needed.