- Community Home
- >
- Networking
- >
- Legacy
- >
- Switches, Hubs, Modems
- >
- MSR2003 and IKEv2
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-12-2020 07:14 AM - edited 11-12-2020 07:15 AM
11-12-2020 07:14 AM - edited 11-12-2020 07:15 AM
MSR2003 and IKEv2
Hello, community!
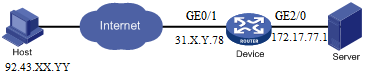
I try to set up HPE MSR2003 router with host-to-site configuration, and I have a trouble with IKE. At HPE FlexNetwork MSR Router Servies Comware 7 Security Configuration Guide on 438 page placed IKE local extended authentication and adress pool authorization configuration example.
I adapt it for my network comfiguration and take error 13868 "Policy match error" at Windows 10 Client.
Please, give me advice: there I have mistake, at router config or this is Windows problem? Which direction I need continue investigation for resolve this issue?
Config:
#
version 7.1.059, Release 0306P30
#
sysname HPE
#
password-recovery enable
#
vlan 1
#
controller Cellular0/0
#
interface Aux0
#
interface NULL0
#
interface GigabitEthernet0/0
port link-mode route
ip address dhcp-alloc
#
interface GigabitEthernet0/1
port link-mode route
ip address 31.X.Y.78 255.255.255.252
ipsec apply policy map1
#
interface GigabitEthernet2/0
port link-mode route
ip address 172.17.77.1 255.255.255.0
#
interface GigabitEthernet2/1
port link-mode bridge
#
interface GigabitEthernet2/2
port link-mode bridge
#
interface GigabitEthernet2/3
port link-mode bridge
#
scheduler logfile size 16
#
line class aux
user-role network-admin
#
line class tty
user-role network-operator
#
line class vty
user-role network-operator
#
line aux 0
user-role network-admin
#
line vty 0 63
user-role network-operator
#
ip route-static 0.0.0.0 0 31.X.Y.77
#
domain dm
authentication ike local
authorization ike local
#
domain system
#
domain default enable system
#
role name level-0
description Predefined level-0 role
#
role name level-1
description Predefined level-1 role
#
role name level-2
description Predefined level-2 role
#
role name level-3
description Predefined level-3 role
#
role name level-4
description Predefined level-4 role
#
role name level-5
description Predefined level-5 role
#
role name level-6
description Predefined level-6 role
#
role name level-7
description Predefined level-7 role
#
role name level-8
description Predefined level-8 role
#
role name level-9
description Predefined level-9 role
#
role name level-10
description Predefined level-10 role
#
role name level-11
description Predefined level-11 role
#
role name level-12
description Predefined level-12 role
#
role name level-13
description Predefined level-13 role
#
role name level-14
description Predefined level-14 role
#
user-group system
#
local-user ike class network
service-type ike
authorization-attribute user-role network-operator
authorization-attribute ip-pool pool
#
local-user test class network
password cipher $c$uvw==
service-type ike
authorization-attribute user-role network-operator
#
cwmp
cwmp enable
#
ipsec transform-set tran1
encapsulation-mode transport
esp encryption-algorithm aes-cbc-256
esp authentication-algorithm sha1
#
ipsec policy-template pt 1
transform-set tran1
ike-profile profile1
reverse-route dynamic
#
ipsec policy map1 1 isakmp template pt
#
ike address-group pool 172.20.33.1 172.20.33.100 255.255.255.255
#
ike profile profile1
keychain keychanin1
local-identity address 31.X.Y.78
match remote identity address 92.43.XX.YY 255.255.255.0
client-authentication xauth
aaa authorization domain dm username ike
#
ike keychain keychain1
pre-shared-key address 172.20.33.1 255.255.255.255 key cipher $c$3vWU=
#
return
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-12-2020 09:43 PM
11-12-2020 09:43 PM
Re: MSR2003 and IKEv2
Hi,
Please check if the policy configured on HPE device and client trying to negotiate the policy are same. If not same or configured then we generally face the issue.
-N

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2020 04:20 AM
11-16-2020 04:20 AM
Re: MSR2003 and IKEv2
Maybe I got wrong example of configuration?
Here is it:
# Configure IP addresses for interfaces. (Details not shown.)
Interface GigabitEthernet2/0
Port link-mode route
Ip address 172.17.77.1 255.255.255.0
exit
Interface GigabitEthernet0/1
Port link-mode route
Ip address 31.X.Y.78 255.255.255.252
# route to ISP
ip route-static 0.0.0.0 0.0.0.0 31.X.Y.77
# Create an ISP domain named dm.
<Device> system-view
[Device] domain dm
# Configure the device to perform IKE local authentication.
[Device-isp-dm] authentication ike local
# Configure the device to perform IKE local authorization.
[Device-isp-dm] authorization ike local
[Device-isp-dm] quit
# Create an IKE IPv4 address pool named pool with an IPv4 address range of 172.20.33.1 to 172.20.33.100.
[Device] ike address-group pool 172.20.33.1 172.20.33.100
# Add a network user named ike.
[Device] local-user ike class network
# Authorize user ike to use the IKE service.
[Device-luser-network-ike] service-type ike
# Specify IPv4 address pool pool as the authorized IPv4 address pool for user ike.
[Device-luser-network-ike] authorization-attribute ip-pool pool
[Device-luser-network-ike] quit
# Add a network user named test.
[Device] local-user test class network
# Authorize user test to use the IKE service.
[Device-luser-network-test] service-type ike
# Configure a password for user test.
[Device-luser-network-test] password simple abc
[Device-luser-network-test] quit
# Create an IKE keychain named keychain1.
[Device] ike keychain keychain1
# Set the preshared key used for IKE negotiation with the remote peer at 1.1.1.1.
[Device-ike-keychain-keychain1] pre-shared-key address 172.20.XX.YY 255.255.255.255 key simple 123456TESTplat&!
[Device-ike-keychain-keychain1] quit
# Create an IKE profile named profile1.
[Device] ike profile profile1
# Specify IKE keychain keychain1 for IKE profile profile1.
[Device-ike-profile-profile1] keychain keychain1
# Specify IP address 2.2.2.2 as the local ID.
[Device-ike-profile-profile1] local-identity address 31.X.Y.78
# Configure the peer ID for IKE profile matching.
[Device-ike-profile-profile1] match remote identity address 92.43.XXX.YYY 255.255.255.0
# Enable XAUTH authentication for clients.
[Device-ike-profile-profile1] client-authentication xauth
# Enable AAA authorization. Specify ISP domain dm and username ike.
[Device-ike-profile-profile1] aaa authorization domain dm username ike
[Device-ike-profile-profile1] quit
# Created an IPsec transform set named tran1.
[Device] ipsec transform-set tran1
# Specify the transport encapsulation mode.
[Device-ipsec-transform-set-tran1] encapsulation-mode transport
# Specify the ESP security protocol.
[Device-ipsec-transform-set-tran1] protocol esp
# Specify the ESP authentication algorithm and encryption algorithm.
[Device-ipsec-transform-set-tran1] esp encryption-algorithm aes-cbc-256
[Device-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[Device-ipsec-transform-set-tran1] quit
# Create an IPsec policy template entry. Specify the template name as pt and set the sequence number to 1.
[Device] ipsec policy-template pt 1
# Specify IPsec transform set tran1.
[Device-ipsec-policy-template-pt-1] transform-set tran1
# Specify IKE profile profile1.
[Device-ipsec-policy-template-pt-1] ike-profile profile1
# Enable IPsec RRI.
[Device-ipsec-policy-template-pt-1] reverse-route dynamic
[Device-ipsec-policy-template-pt-1] quit
# Use IPsec policy template pt to create an IKE-based IPsec policy entry. Specify the policy name as map1 and set the sequence number to 1.
[Device] ipsec policy map1 1 isakmp template pt
# Apply the IPsec policy to GigabitEthernet 0/1.
[Device] interface gigabitethernet 0/1
[Device-GigabitEthernet1/0/1] ipsec apply policy map1
[Device-GigabitEthernet1/0/1] quit
As I uderstood, here is two settings of crypto policy:
esp encryption-algorithm aes-cbc-256
esp authentication-algorithm sha1
Maybe default Windows settings for IKE tunnel not suitable for HPE routers and need addition settings? Via PowerShell I did this settings:
AuthenticationTransformConstants : GCMAES256
CipherTransformConstants : GCMAES256
DHGroup : Group14
IntegrityCheckMethod : SHA1
PfsGroup : PFS2048
EncryptionMethod : GCMAES256
But nothing changed.
I also include this parameters in Windows Registry:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RasMan\Parameters]
"NegotiateDH2048_AES256"=dword:00000002
"DisableIKENameEkuCheck"=dword:00000001
Sorry for my newbie questions, this is my first HPE router.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2020 07:18 AM
11-16-2020 07:18 AM
Re: MSR2003 and IKEv2
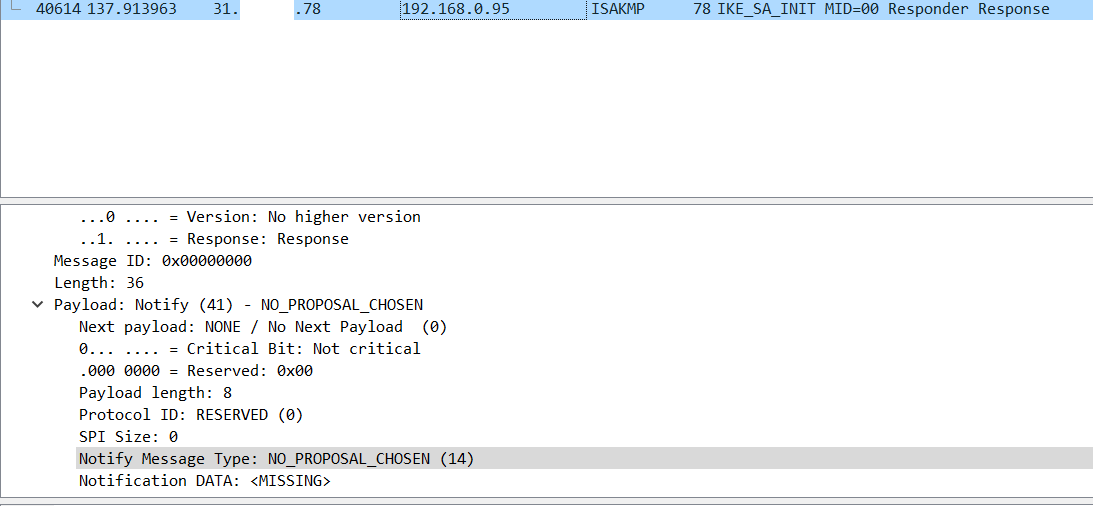
I scanned the connection with the Wireshark and found the message No proposal chosen.
But what parameters should be set in Windows?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2020 09:42 PM
11-17-2020 09:42 PM
Re: MSR2003 and IKEv2
Hi,
From the windows client configuration I can see its using GCMAES256 while the HPE device is using CBCAES256 due which there is a mismatch in proposal. I will suggest to change the windows client to use CBC-AES-256 and check if it works. If CBC is not applicable on windows client then you can try with below any other cipher suites
3des-cbc 168-bit CBC mode 3DES
aes-cbc-128 128-bit CBC mode AES
aes-cbc-192 192-bit CBC mode AES
aes-cbc-256 256-bit CBC mode AES
aes-ctr-128 128-bit CTR mode AES
aes-ctr-192 192-bit CTR mode AES
aes-ctr-256 256-bit CTR mode AES
camellia-cbc-128 128-bit CBC mode Camellia
camellia-cbc-192 192-bit CBC mode Camellia
camellia-cbc-256 256-bit CBC mode Camellia
des-cbc 56-bit CBC mode DES
Windows Client Proposal -
AuthenticationTransformConstants : GCMAES256
CipherTransformConstants : GCMAES256
DHGroup : Group14
IntegrityCheckMethod : SHA1
PfsGroup : PFS2048
EncryptionMethod : GCMAES256
HPE Router Proposal -
esp encryption-algorithm aes-cbc-256
esp authentication-algorithm sha1
-N

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2020 01:44 AM - edited 11-20-2020 01:45 AM
11-20-2020 01:44 AM - edited 11-20-2020 01:45 AM
Re: MSR2003 and IKEv2
Thanks for answer!
As I understood, Windows 10 20H2 supports next algorithm:
AuthenticationTransformConstants: GCMAES256 (MD596, SHA196, SHA256128, GCMAES128, GCMAES192, GCMAES256, None)
CipherTransformConstants: GCMAES256 (DES, DES3, AES128, AES192, AES256, GCMAES128, GCMAES192, GCMAES256, None)
EncryptionMethod: GCMAES256 (GCMAES128, GCMAES192, GCMAES256)
IntegrityCheckMethod: SHA384 (MD5, SHA1, SHA256, SHA384)
PfsGroup: PFS2048 (None, PFS1, PFS2, PFS2048, ECP256, ECP384, PFSMM, PFS24)
DHGroup: Group14 (None, Group1, Group2, Group14, ECP256, ECP384, Group24)
So Windows 10 version 20H2 supports only GCMAES128, GCMAES192, GCMAES256 encryption methods, as I understood HPE doesn't support this connection type.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2020 05:57 PM
11-22-2020 05:57 PM
Re: MSR2003 and IKEv2
Hi,
Below are the supported cipher from HPE Device.
For IPSEC transform set, HPE supports below encryption
[MSR-ipsec-transform-set-test]esp encryption-algorithm ?
3des-cbc 168-bit CBC mode 3DES
aes-cbc-128 128-bit CBC mode Advanced Encryption Standard (AES)
aes-cbc-192 192-bit CBC mode AES
aes-cbc-256 256-bit CBC mode AES
aes-ctr-128 Use 128-bit AES-CTR
aes-ctr-192 Use 192-bit AES-CTR
aes-ctr-256 Use 256-bit AES-CTR
camellia-cbc-128 Use 128-bit CAMELLIA-CBC
camellia-cbc-192 Use 192-bit CAMELLIA-CBC
camellia-cbc-256 Use 256-bit CAMELLIA-CBC
des-cbc 56-bit CBC mode Data Encryption Standard (DES)
gmac-128 Use 128-bit GMAC
gmac-192 Use 192-bit GMAC
gmac-256 Use 256-bit GMAC
gcm-128 Use 128-bit GCM
gcm-192 Use 192-bit GCM
gcm-256 Use 256-bit GCM
null Use NULL
For IKEv2 Proposal, HPE supports below encryption
[MSR-ikev2-proposal-test]encryption ?
3des-cbc 168-bit CBC mode 3DES
aes-cbc-128 128-bit CBC mode AES
aes-cbc-192 192-bit CBC mode AES
aes-cbc-256 256-bit CBC mode AES
aes-ctr-128 128-bit CTR mode AES
aes-ctr-192 192-bit CTR mode AES
aes-ctr-256 256-bit CTR mode AES
camellia-cbc-128 128-bit CBC mode Camellia
camellia-cbc-192 192-bit CBC mode Camellia
camellia-cbc-256 256-bit CBC mode Camellia
des-cbc 56-bit CBC mode DES
You may chose anyone one of them which is available in windows and also to inform IPSEC transform set and IKE Proposal are two different things so we have to make sure windows client is negotiating properly with correct proposal.
-N