- Community Home
- >
- Services
- >
- The Cloud Experience Everywhere
- >
- Security for the rapidly expanding remote workforc...
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Receive email notifications
- Printer Friendly Page
- Report Inappropriate Content
Security for the rapidly expanding remote workforce
The rapid expansion of work-from-home has exposed businesses to potential cyber threats and data privacy challenges, together with legal risks. Cyber criminals see new opportunities.
The COVID-19 pandemic caught everyone unaware, both personally and professionally, and has required everyone to make changes in the way they live and work in a short timeframe. While it’s easy to look only at the negative impact of moving to a remote workforce, it’s also an opportunity for organizations to take a step back and see how they can programmatically approach secure remote working to strengthen business resiliency. Over the years, we’ve seen many of our customers adopt a remote workforce strategy; however, while telecommuting has grown 115% in the past decade, 44% of companies don't allow remote work at all, due in part to a lack of workplace culture change, according to an article from smallbizgenius.

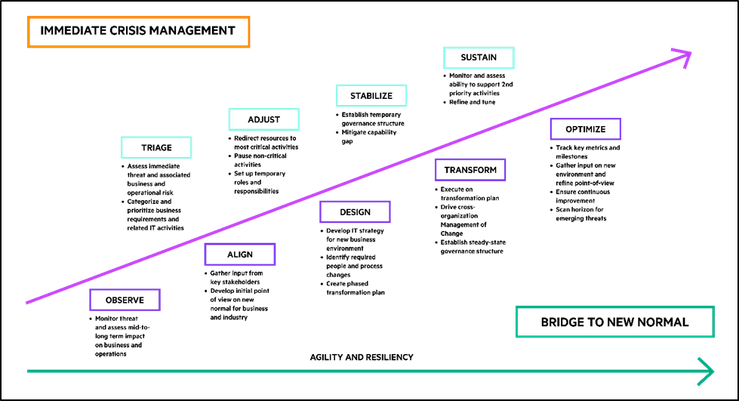
HPE Pointnext Services has developed a clear nine-step model, composed of two phases, to guide organizations through the immediate crisis and, in parallel, plan for the medium- to long-term.
The first four steps are related to immediate crisis management, activating the organization’s resources to protect the business fundamentals and operate with enough capacity to fulfill only the highest-priority needs. The latter five steps establish the bridge to the "new normal." While a future article will consider security in more expansive remote working scenarios in the new normal, here we focus on immediate crisis management relative to security for the rapidly expanding remote workforce.
Step One: Triage
In the nine-step model, the main aims of the triage step are to assess and categorize the organization’s current position in a crisis management situation requiring employees to work from home, and then to define a minimum set of capabilities that will support business as usual. It’s important that the security team is involved in this stage, as there is increased risk that the organization will be exposed to a security breach while already struggling to keep the business going. Experience has shown us that malware authors and cybercriminals will use chaos to exploit new phishing and malware campaigns, and the COVID-19 global pandemic is no exception.
A couple of easy first steps to take during Triage include assessing the mobile workforce: identify the number of mobile workers and their technology requirements, and evaluate the resulting technology risk, putting this into perspective with any top-of-mind cyber risks driven by the current threat landscape.
The security team should convene with the IT and business stakeholders to review the identified cyber risks, especially those that could have an immediate negative impact to the business due to the new crisis. The identified risks should be prioritized and appropriate remediation actions agreed upon to minimize risk to the IT infrastructure. In particular, the review should focus on weaknesses, based on likelihood of exploitation and organizational exposure, plus the resultant impacts to the organization, particularly those brought about by a rapid expansion of the remote workforce.
It may be necessary to temporarily tighten access control and reconsider security and environmental changes until the situation is well understood and the new operating baseline is established. The key objective in triage is to understand your current situation and to maintain the integrity of the organization’s security posture until proper adjustments can be made based on the crisis at hand.
In a later step, after the crisis situation has been stabilized, a more formal approach to reviewing the cybersecurity controls that are currently in place should be undertaken to determine the effectiveness of those controls in the new normal and assess what security control changes need to be made to facilitate secure advancement to future steps.
Step Two: Adjust
Once the organization has triaged the current state and determined the short-term priority actions, the nine-step model advises the creation of small teams that can act swiftly on the action items in an agile manner. At this point cybersecurity needs to get integrated into those teams to ensure that each of the priority actions is handled in a secure manner. Cybersecurity’s role is key – firstly in ensuring that the organization understands and accepts the risk of the project (and any new technical solutions that are part of it), and secondly in ensuring that the project has the appropriate technical security controls and processes in place.
Cybersecurity must be empowered to rapidly assess any new tools that are being adopted – for example, are there any known security concerns for the online video collaboration tool that has been chosen? If so, identify the risks, document them, and determine treatment – can the risk be accepted by putting usage best practices into place? Can the risk be remediated, or is it a red flag?
In many cases the technologies to be used may already be implemented, and just need to be expanded to fit the new use case – for example, by considering whether VPN gateways are in the right geographic location and set up in a highly available manner to service users without negatively impacting latency. Or considering whether the network security controls are scaled effectively to handle the new demands. It may useful to look at public-cloud-based, software-defined perimeter solutions as an alternative. Or to look at expanding the current VPN capabilities to include NAC tools that assess device risk upon connection to the network, and take actions based upon current compliance state. These actions include quarantining high-risk remote access devices to a separate secure VLAN or enforcing the update of endpoint software or security configuration before the remote connection is accepted. This helps to mitigate the risk of users forced to use personal devices to access corporate applications.
In this step, it is also worth considering whether the operational security processes that are in place are suitable for a large remote workforce scenario. Ensure that controls exist to check whether the latest vulnerabilities are patched – not just on data center and infrastructure components, but also on managed endpoints.
Current security models, designed for predominantly on-site operations, may need to be extended to address security concerns for remote device access. For example, organizations may be prudent to adopt reputation-based proxy services to protect home users, or accelerate the introduction of EDR (endpoint detect and respond) tools to supplement traditional anti-virus.
Focus on the human factor. Many of the security organizations we speak to are experiencing an increase in the number of phishing attempts trying to capitalize on the COVID-19 chaos. Organizations should immediately develop messaging to their users warning of the risks of phishing attacks, how to spot them and avoid them. For those organizations that have tools in place to detect and block phishing attempts, a review of the tool must be adjusted to detect COVID-19-related phishing attempts and provide the same protection for the remote worker.
Use the potential slowdown of normal business activities as an opportunity to provide IT staff with online security trainings to increase their organizational value, but also keep their minds fresh – check this recent enterprise.nxt article for some suggestions: It’s a good time to take an online security course.
Step Three: Stabilize
Once the crisis has been triaged and any critical short-term adjustments have been made, cybersecurity teams should look to build a sustainable security model for the future that assumes that the remote workforce may not reduce to its previous scale.
An initial step to stabilize the situation is the establishment of a security governance structure. This will involve assessing security operations – the nerve center for what’s happening in your organization, security-wise – to make sure appropriate log sources are integrated and normalized for easy identification of related events. The log sources should be closely monitored for increases in security incidents, and security analysts should determine if specific types of threats are more prevalent (phishing, malware etc.) and make necessary adjustments to security tools and associated remediation processes. A good security governance program should also include compliance reporting to help identify any threats or operational vulnerabilities early.
As the situation is beginning to stabilize, identify major gaps that weren’t addressed in the short term, but need to be resolved, and build a plan. This starts by conducting a formal security controls analysis to determine if the current security control structure is mature enough to carry the organization forward in a stable and risk-appropriate manner. HPE recommends assessing security controls against open, well-known standards such as the CIS Top 20 Critical Controls, ISO27002 or NIST 800-53. This important activity will surface weaknesses in the security controls used by the organization and sets the stage for remediation activities to address the discovered weaknesses.
The assessment of the current state of the organization’s security controls should not be performed in isolation. It’s vital for the security controls assessment team to work closely with the business stakeholders to understand the impact that working remotely will have on the organization. In addition to assessing the organization’s security controls, the infrastructure must be fully evaluated for vulnerabilities. This is best accomplished by rigorous vulnerability scanning and prioritized remediation of high- and critical-level vulnerabilities.
Step Four: Sustain
The Sustain step is primarily a function of formalizing and institutionalizing the activities performed in the first three steps (Triage, Adjust and Stabilize). Because the first three steps can themselves be difficult to adopt and cause disruption, the newly embraced security activities, controls and processes must rapidly evolve to the new normal. The Sustain step requires that you closely monitor and assess the adjustments you have made to the security program to determine if they are having the desired effect of reducing risk brought about by the crisis.
To fulfill the Sustain step, it may be necessary to iterate back to previous steps and refine activities to enhance the emerging steady state.
A key part of Sustain is to capture and document key learnings from the previous steps so that as you move into the next phase of the nine-step model, you can make these learnings an integral part of your ongoing security program.
Integrating security in the new normal
The current pandemic and the challenges that organizations are faced with are demonstrating the importance of including the cybersecurity team in a crisis management program. The HPE Pointnext Services nine-step model formalizes this by making security an integral part of the response effort. A future article in this series will focus on Phase 2 (Bridge to the New Normal) and the specific cybersecurity actions that you should undertake to move to the new normal with an optimized cybersecurity capability that will position you for the next crisis.
Learn more about risk and security management services from HPE Pointnext Services.
Stay safe,
Timothy
Timothy Ferrell
Hewlett Packard Enterprise
linkedin.com/showcase/hpe-technology-services/
Simon Leech CISSP-ISSAP CCSK CISM CRISC is a contributing author for this post. Simon is a leader in HPE Pointnext Services' Security and Risk Management Practice.
- Back to Blog
- Newer Article
- Older Article
- Deeko on: The right framework means less guesswork: Why the ...
- MelissaEstesEDU on: Propel your organization into the future with all ...
- Samanath North on: How does Extended Reality (XR) outperform traditio...
- Sarah_Lennox on: Streamline cybersecurity with a best practices fra...
- Jams_C_Servers on: Unlocking the power of edge computing with HPE Gre...
- Sarah_Lennox on: Don’t know how to tackle sustainable IT? Start wit...
- VishBizOps on: Transform your business with cloud migration made ...
- Secure Access IT on: Protect your workloads with a platform agnostic wo...
- LoraAladjem on: A force for good: generative AI is creating new op...
- DrewWestra on: Achieve your digital ambitions with HPE Services: ...