- Community Home
- >
- Networking
- >
- Switching and Routing
- >
- Web and Unmanaged
- >
- Re: HP V1810-48G je009a spanning tree missing in c...
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2017 03:56 PM - edited 06-15-2017 04:07 PM
06-15-2017 03:56 PM - edited 06-15-2017 04:07 PM
Re: HP V1810-48G je009a spanning tree missing in configuration? general spanning tree questions?
The point is that if the Core is made of E1 and E2 stacked together (into a Virtual Switch), E1 and E2 act as a single logical identity (E1 and E2 are stacked using (a) special Stacking modules and cables, this is usually called backplane stacking or (b) normal (Tengiga/Giga)bit Ethernet ports, this is called generally frontplane stacking...in both cases E1 and E2 are seen as a single E Switch), and to benefit from added resiliency of the Stack of E1 and E2 you will need (it's a good practice) to deploy Servers (or NAS, as example) as dual homed network devices...dual homing means basically to concurrently connect the device to both E1 and E2 using Port Trunking (with LACP)...that way when one Stack member goes down, connectivity between each physical dual homed Server is granted through the other Switch member of the same stack...switch which we presume still up and running.
Stacking provides generally two (well three) stacking networking topologies, the daisy chain and the ring...there is also mesh but it isn't so common.
When E1 and E2 are "simply" just interconnected together (so not properly stacked as was explained to you)...and that can happen using a Port Trunking (Good<-resiliency) or using a single link Trunk (Bad<-no resiliency)...then E1 and E2 will remain logically separated entities (and STP jumps in playing a role) so Servers could still be dual homed to both Switches physically (clearly not using LACP Port Trunking due to LACP implementation restrictions) but they can't be dual homed logically (I mean they aren't really dual homed "concurrently")...this because your three objects E1, E2 and Server will form a loop exactly through the Server's NIC...this means that - thanks to STP named above - only one link from Server to E1 and E2 will be active at the same time...if E1 or E2 will go down, the link from Server to it will go down...but the other link (previously blocked by STP) will be automatically activated and so connectivity to at least one Switch is somewhat granted.
Clearly the stacking approach (Virtual Switch, speaking the HPE jargon VSF or IRF...as examples) is better.
Sorry for simplicistic explanation but, more or less, this is the scenario...
I'm not an HPE Employee

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2017 05:19 PM
06-15-2017 05:19 PM
Re: HP V1810-48G je009a spanning tree missing in configuration? general spanning tree questions?
I very much doubt Cisco 300 switches are stackable.
The way you get resiliency is that you interconnect the two "Cores". Then you patch each Access switch to both "Cores", and you patch each server to both "Cores".
How you manage the servers' dual connections is something you get from the server doco - "teaming" or whatevere they call it.
The Access switches' dual connections is managed by enabling spanning-tree on every switch, and giving Core1 a priority of "0", Core2 a priority of "1" and then leaving your access switches' priority at 8. If you have any Access switches daisy chained off other Access switches, they need to have their STP priority increased by 1 for each hop they are away from the "Core".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2017 05:53 PM
06-15-2017 05:53 PM
Re: HP V1810-48G je009a spanning tree missing in configuration? general spanning tree questions?
I just read the datasheet on the Cisco 300s, they look pretty good. I haven't bought Cisco for any customer for years though, as you get much better bang for your buck with almost any other vendor. Compare prices with the HP2930, which is better than the Cisco300.
Looking at your wiring closet, it looks like you have almost 200 desks, although you only have half as many phones, so maybe there is a heap of patching on those black patch panels that doesn't need to be? Or maybe you also have a bunch of analog phones patched in elsewhere? I must say I don't understand what these "PoE" things are - they can't be power injectors or there would more patching coming out of them - are they simply switches?
The first thing you could do is to halve the amount of wiring by patching the PCs through the phones, like VoIP was designed to be deployed.
You will have to learn how to manage VLANs.
A basic VLAN plan would be to have 6 VLANs:
VLAN10 - Data, all your users' PCs, untagged on all the Access switch ports
VLAN20 - Voice, all your phones, tagged on all the Access switch ports
VLAN30 - Servers, all your servers, not spanned to any other switches
VLAN100 - Management, all your network switches have an IP address on this VLAN so you can telnet or https to them for management.
VLAN200 - Edge, connectivity to your gateway environment/firewall.
VLAN99 - black hole VLAN, add it to the inter-switch links as the untagged VLAN. Do not put any IP addressing on it on any switch.
You configure these VLANs on the "Cores", add all VLANs to the inter-"Core" links, add in IP addressing on both "Cores" (If they don't stack, use VRRP), enable VLANs as needed on the local ports, then span VLANs out as appropriate to the other switches.
In the process, that cable mess can be sorted out.
Also, you should be able to reduce your switch requirement down to 2? 3? or maybe 4? 48-port Access switches and 2xCores. Even fewer if you patch some Access layer connections directly to a "Core" - on your size network, this is probably a good option to save having to buy too many switches.
The rackspace this frees up can be inserted between the black patch panels so you can manage the patch cables better.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2017 07:32 PM - edited 06-15-2017 07:39 PM
06-15-2017 07:32 PM - edited 06-15-2017 07:39 PM
Re: HP V1810-48G je009a spanning tree missing in configuration? general spanning tree questions?
@Vince-Whirlwind wrote:I just read the datasheet on the Cisco 300s, they look pretty good. I haven't bought Cisco for any customer for years though, as you get much better bang for your buck with almost any other vendor. Compare prices with the HP2930, which is better than the Cisco300.
Looking at your wiring closet, it looks like you have almost 200 desks, although you only have half as many phones, so maybe there is a heap of patching on those black patch panels that doesn't need to be? Or maybe you also have a bunch of analog phones patched in elsewhere? I must say I don't understand what these "PoE" things are - they can't be power injectors or there would more patching coming out of them - are they simply switches?
The first thing you could do is to halve the amount of wiring by patching the PCs through the phones, like VoIP was designed to be deployed.
You will have to learn how to manage VLANs.
A basic VLAN plan would be to have 6 VLANs:
VLAN10 - Data, all your users' PCs, untagged on all the Access switch ports
VLAN20 - Voice, all your phones, tagged on all the Access switch ports
VLAN30 - Servers, all your servers, not spanned to any other switches
VLAN100 - Management, all your network switches have an IP address on this VLAN so you can telnet or https to them for management.
VLAN200 - Edge, connectivity to your gateway environment/firewall.
VLAN99 - black hole VLAN, add it to the inter-switch links as the untagged VLAN. Do not put any IP addressing on it on any switch.You configure these VLANs on the "Cores", add all VLANs to the inter-"Core" links, add in IP addressing on both "Cores" (If they don't stack, use VRRP), enable VLANs as needed on the local ports, then span VLANs out as appropriate to the other switches.
In the process, that cable mess can be sorted out.
Also, you should be able to reduce your switch requirement down to 2? 3? or maybe 4? 48-port Access switches and 2xCores. Even fewer if you patch some Access layer connections directly to a "Core" - on your size network, this is probably a good option to save having to buy too many switches.The rackspace this frees up can be inserted between the black patch panels so you can manage the patch cables better.
We have about 40 people overall, but there are many desks with multiple ports.. conference rooms, flex rooms, front areas, various other spots in the office.. its adds up to 192.. then there is a "voice" port for each desk.. these goto the POE Netgear 24 port switches x 3 in the pic and diagram. For some reason the communication company that did our phones did it that way originally, i think in a vlan on the netgears.. still havent gotten that far in re-checking things.
We use ip office 500 and avaya phones.. i'm not sure how the pc's would patch into those "voice" lines if we could merge switches and get all POE switches I assume.. or do you mean get enough to cover 72 phone / voice cat 6's and the rest of the 192, all POE, with a core switch.
Yes it appears vlans is the direction i should be going.. issue is.. the downtime i can invest in this is probably limited to a saturday and into early sunday worst case. Already figuring it will take me a good part of a day just to rewire (and more properly tag each cable this time)... i have 10 foot cables coming (200) as well as velcro ties and i'm getting rid of the verticle teeth manager on the right and putting a 6 foot manager on left and right that are "open" air with the ring style instead.
But in doing the vlans.. if all of this was merged per say.. is it safe to assume i'm just as well off with one core (and a hotspare under it ready to plugin when needed if it dies)? As was mentioned, it sounds as if the cisco's cant be stacked.
I've also seen it suggested to use purely stackable switches.. like Hp Procurve 2900? (i cant seem to find pricing/info on this).. where all of them as a unit would have one management ip address and server as a core router for all networks (unsure on this last part).. then with various vlans as mentioned here. I think i saw that a dell powerconnect 6248p would work (cant find much on this either).. i'm assuming these are POE stackable switches and maybe thats what i should look up, unsure..
Or just go the easy route, which is likely prefered by the local company.. cisco switches.. one at the core, one spare.. and the satelite ones (mix of the cisco and the remaining "good" dlinks and or hps).
Wouldnt the vlan live on various switches, not just the core, though the servers all being on the core, since there are only 48 ports.
Does stacking like with a procurve stackable 2900 still require having dual output sets of ethernet from each server, one to each core switch i assume.. or in the case of stacking 2900s ?without a central core? does that change things (the picture i saw didnt really seem to suggest it had a core)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2017 08:34 AM - edited 06-16-2017 12:05 PM
06-16-2017 08:34 AM - edited 06-16-2017 12:05 PM
Re: HP V1810-48G je009a spanning tree missing in configuration? general spanning tree questions?
In discussing with higher ups here.. unfortunately the "right way" which i do now think is more stackable.. wont fly assuming the cost is $8k to get us there.. I'm still trying to gather those details on the fully stackable solution so i can have that on the backburner when this planA goes to pot in a few months again.
That said, i guess the only thing that can be done here is to go with planA with the ciscos mixed with the dlinks/hps, have a cisco as a hot spare ready as a core for this star layout for now, all tying into the exisitng 3x 24 port POE switches as well for voice.
Question is, with all these flavors of switches and this new arrangement.. how can i still configure vlans.. wouldnt i ultimately have a vlan for workstations, a vlan for the phones (72 ports) and a vlan for servers as well as the management vlan i guess.. but with a cisco at the center and dlinks/netgears and hps sateliting around it.. how would that work and how do they tie together to properly route (IE: workstation vlan to the server vlan).
I used to know much of this but over the years have gotten rusty as I dont do this much since the layout here is mostly static/non changing..
edit:
Actually since putting this on here, looks as if i can get the procurve 2900-48G for around $295 from newegg refurbed with a 1 year warranty (and these all have lifetime warranties from HP), which seems amazing considering these were $2000+ switches i think.. but we could still use some POE versions to add to the mix too, to get rid of the netgear poes and have em all in the same stack.. not finding much with POE that is this cheap or even $600.. the POE's all seem to run closer to $2000 for a 48 port version (need 2)..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2017 01:42 PM - edited 06-16-2017 02:11 PM
06-16-2017 01:42 PM - edited 06-16-2017 02:11 PM
Re: HP V1810-48G je009a spanning tree missing in configuration? general spanning tree questions?
i guess the cx4s on this arent considered stacking, maybe only the x2 ports? which need x2 transceivers? (i read the cx4 are limited to 2.5 gbps bandwidth because in 4 channels whereas x2 is newer and better, though none of our servers exceed 1gbps
edit: from digging deeper, seems the 2900 series might not be truly stacked switches.. but rather a big virtual switch that is just able to be managed as a whole and can still suffer cascading issues.?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2017 05:02 PM
06-16-2017 05:02 PM
Re: HP V1810-48G je009a spanning tree missing in configuration? general spanning tree questions?
The 2930s are a proper stacking switch.
By consolidating on a small number of smaller switches you reduce support time required, and probably reduce power consumption as well. Having a mish mash of different switch types is not much fun.
Regardless of what you do, cleaning up that network is something that an experienced network manager could get done in about 3 days.
Anything you are unsure about, eg, spanning a VLAN from a Cisco300 to a DLink, you will need to test first before implementing it, so you understand how it works and how not to break it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2017 08:31 AM - edited 06-19-2017 08:42 AM
06-19-2017 08:31 AM - edited 06-19-2017 08:42 AM
Re: HP V1810-48G je009a spanning tree missing in configuration? general spanning tree questions?
@Vince-Whirlwind wrote:The 2930s are a proper stacking switch.
By consolidating on a small number of smaller switches you reduce support time required, and probably reduce power consumption as well. Having a mish mash of different switch types is not much fun.
Regardless of what you do, cleaning up that network is something that an experienced network manager could get done in about 3 days.
Anything you are unsure about, eg, spanning a VLAN from a Cisco300 to a DLink, you will need to test first before implementing it, so you understand how it works and how not to break it.
I wish they'd pay the price to go that route with the proper stacking switch.. i'm unsure if the cisco500 is in the same league as well or carries the lifetime warranty.. either way similar cost.. (EDIT: looks like it may be possible to get a 500 series cisco for $529 refurbished unsure what the difference is between sf and sg? scratch that, it was only 10/100 on most ports)
I did have vlans working at some point, but havent had a real need till now... i had a general understanding on how to link the vlans.. not sure if its 100% accurate..
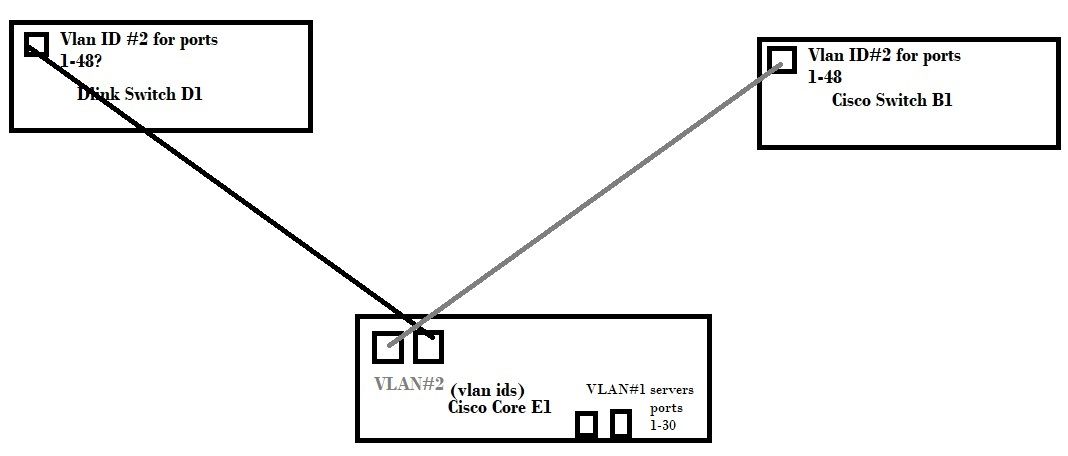
Lets say I had workstations plugged into a cisco and dlink satellite switches off the cisco at the core.. so 48 ports x2 available for vlanning..
Would I set cisco satellite E1 ports 1-48 say VLAN ID #2.. then the dlink 1-48 would also be VLAN ID #2 (even though a different vendor).. then at the cisco at the core.. I would have two ports going to each of those satellite switches and assign a tagged vlan ID of #2 to each one of those?
then the question is.. if I have say vlan id #1 for servers on the core switch on say ports 1-30, how do I make sure vlan id #1 (servers) can route to vlan id #2 (workstations), not shown are the other forks of the core.. or the POE1-3 that would go into 3 of the satellites as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2017 07:03 PM
06-19-2017 07:03 PM
Re: HP V1810-48G je009a spanning tree missing in configuration? general spanning tree questions?
First thing, be careful about HP "2900-series". There are some ancient HP switches called 2900s which aren't much use to you. I think there are 2910s as well, which you should also avoid (I think they aren't even HP switches, but a 3rd-party job). 2920s are excellent switches for your environment, if you can get those. 2930s are the current model.
Secondly, for a 40-person site, you have waaaay too much infrastructure and cabling in the wiring closet. A stack of 2x 48-port switches should give you all the active ports you need. Telcommunications installers who insist on putting in their own switches should not be allowed! (A/V installers and security installers do the same thing).
Thirdly, the time to get budget to buy the good gear you need is when a new IT project is being initiated and you talk them into recognising that your network needs to be replaced with a simple stack of proper low-latency, high throughput modern managed switches, preferably with some 10Gb options for your servers and storage.
OK, for your example, you have 1 core and two access switches.
Are those DLink switches managed switches? If not, and you want the devices that are patched to the DLinks to be in VLAN2, then you need to patch them to ports on your core that are *untagged* in VLAN2. So the unmanaged switch ends up being on VLAN2 without ever knowing anything about VLANs. You can't get multiple VLANs on the unmanaged switch (well, you can, using H3C hybrid port config but don't even think about it).
If the DLinks are managed switches, then you configure the interswitch link ports as *tagged* in VLAN2 at both ends, then on the DLink switches change all the Access ports to *untagged* in VLAN2.
Think of a VLAN as a circuit.
At Layer2 (switching) you need to ensure that everything that is in the same subnet is also in the same VLAN. And you need to make sure that each VLAN is continuous between switches - if two switches both have ports in a VLAN, then those switches need to be connected in that VLAN. That's a broadcast segment.
At Layer3, you want things in different VLANs to be able to communicate - this is where routing comes in. Pick a location: your "core" switch. Make sure all VLANs are trunked back to that switch and create them all on the "core", create a VLAN interface for each VLAN. Each VLAN is synonymous with a subnet. The IP address that goes on the VLAN interface is the "router"/"default gateway" address for that subnet.
eg,
VLAN10 "DATA" - 10.1.10.0/24....VLAN10 interface IP address on the core 10.1.10.1/24. All hosts on VLAN10 have 10.1.10.1 as their "default gateway".
VLAN20 "VOICE" - 10.1.20.0/24....VLAN20 interface IP address on the core 10.1.20.1/24. All hosts on VLAN20 have 10.1.20.1 as their "default gateway".
etc...
If you have these two VLAN interfaces configured on your "core", and you have "ip routing" enabled on the "core", then the "core" will automatically route between them.
If you can find a couple of spare switches, set up a lab to get comfortable with these concepts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2017 09:20 PM - edited 06-19-2017 09:23 PM
06-19-2017 09:20 PM - edited 06-19-2017 09:23 PM
Re: HP V1810-48G je009a spanning tree missing in configuration? general spanning tree questions?
@Vince-Whirlwind wrote:First thing, be careful about HP "2900-series". There are some ancient HP switches called 2900s which aren't much use to you. I think there are 2910s as well, which you should also avoid (I think they aren't even HP switches, but a 3rd-party job). 2920s are excellent switches for your environment, if you can get those. 2930s are the current model.
Secondly, for a 40-person site, you have waaaay too much infrastructure and cabling in the wiring closet. A stack of 2x 48-port switches should give you all the active ports you need. Telcommunications installers who insist on putting in their own switches should not be allowed! (A/V installers and security installers do the same thing).
Thirdly, the time to get budget to buy the good gear you need is when a new IT project is being initiated and you talk them into recognising that your network needs to be replaced with a simple stack of proper low-latency, high throughput modern managed switches, preferably with some 10Gb options for your servers and storage.
OK, for your example, you have 1 core and two access switches.
Are those DLink switches managed switches? If not, and you want the devices that are patched to the DLinks to be in VLAN2, then you need to patch them to ports on your core that are *untagged* in VLAN2. So the unmanaged switch ends up being on VLAN2 without ever knowing anything about VLANs. You can't get multiple VLANs on the unmanaged switch (well, you can, using H3C hybrid port config but don't even think about it).
If the DLinks are managed switches, then you configure the interswitch link ports as *tagged* in VLAN2 at both ends, then on the DLink switches change all the Access ports to *untagged* in VLAN2.Think of a VLAN as a circuit.
At Layer2 (switching) you need to ensure that everything that is in the same subnet is also in the same VLAN. And you need to make sure that each VLAN is continuous between switches - if two switches both have ports in a VLAN, then those switches need to be connected in that VLAN. That's a broadcast segment.At Layer3, you want things in different VLANs to be able to communicate - this is where routing comes in. Pick a location: your "core" switch. Make sure all VLANs are trunked back to that switch and create them all on the "core", create a VLAN interface for each VLAN. Each VLAN is synonymous with a subnet. The IP address that goes on the VLAN interface is the "router"/"default gateway" address for that subnet.
eg,
VLAN10 "DATA" - 10.1.10.0/24....VLAN10 interface IP address on the core 10.1.10.1/24. All hosts on VLAN10 have 10.1.10.1 as their "default gateway".
VLAN20 "VOICE" - 10.1.20.0/24....VLAN20 interface IP address on the core 10.1.20.1/24. All hosts on VLAN20 have 10.1.20.1 as their "default gateway".
etc...If you have these two VLAN interfaces configured on your "core", and you have "ip routing" enabled on the "core", then the "core" will automatically route between them.
If you can find a couple of spare switches, set up a lab to get comfortable with these concepts.
Thanks, this is all invaluable pointers/reminders.. on the going with the star config and re-using the dlinks mixed with the cisco 300s.. i all but decided against this today.. it seems too risky and I may end up in another mess, due to mixing brands/firmwares, models etc and trying to do the vlans.. I think i made a valid push for a higher budget that may yield us either the hp 2920's (hadnt considered the 2930s, may look as well).. at least the refurbs for around $800 x 7 get us at a $5500 price point, however, for 7 switches it seems it requires 6 if not 7 stacking modules at $220 a piece plus the cables (adding another $1500+) to this cost.. the other option was the cisco 2960-x, also the same bracket, or the Dell 6248 (though pretty old i think).
Yes, management wanted tons of data ports when this building was moved into.. which frankly, everyone does use, especially for development/r&d etc, we are a software/hardware company so everything is utilized.. The alternative i guess would be to not use quite a few of the extra ports in each area but instead throw small 6 and 8 port switches on the other end.. but i was never a fan of this approach, only where really needed.
Unfortunately though, the communications company wasnt the most efficient in laying things out.. for instance, those extra 3 poe switches for phones (24 x 3, 72 ports).. i now understand.. i should patch the phones to the computers lan cable and then back to the phone jack to save 72 ports.. so where i have 7 switches right now, this can become 5 Non POE and 2 POE type (adding to the cost figures above, but getting rid of the mix of equipment). I dont see any way to reduce from 7 switches overall though, but still down from 10.