- Community Home
- >
- Networking
- >
- Switching and Routing
- >
- Web and Unmanaged
- >
- Wildcard with macadress switch 1920
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-27-2018 08:05 AM
05-27-2018 08:05 AM
Wildcard with macadress switch 1920
Hi everyone, good morning (at least here in Brazil).
So, I recently purchased a HP Switch 1920 (JG925A) and I am trying to do an ACL between all my network and my server. My need is to block all mac address to access my server, and only some computers will get the access to my server. In resume: block all (with mac address acl) and release some (also with mac address acl).
The firmware of the switch was updated to the last version (2017).
I do not find any document with the right procedure and/or the rigt mac address wildcard schema to reach my goal.
Thanks for the help.
- Tags:
- ACLs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2018 05:37 AM
06-04-2018 05:37 AM
Re: Wildcard with macadress switch 1920
Hi,
You may refer 'Configuring MAC Authentication' in the user guide below.
I am an HPE Employee

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2018 08:51 PM
06-04-2018 08:51 PM
Re: Wildcard with macadress switch 1920
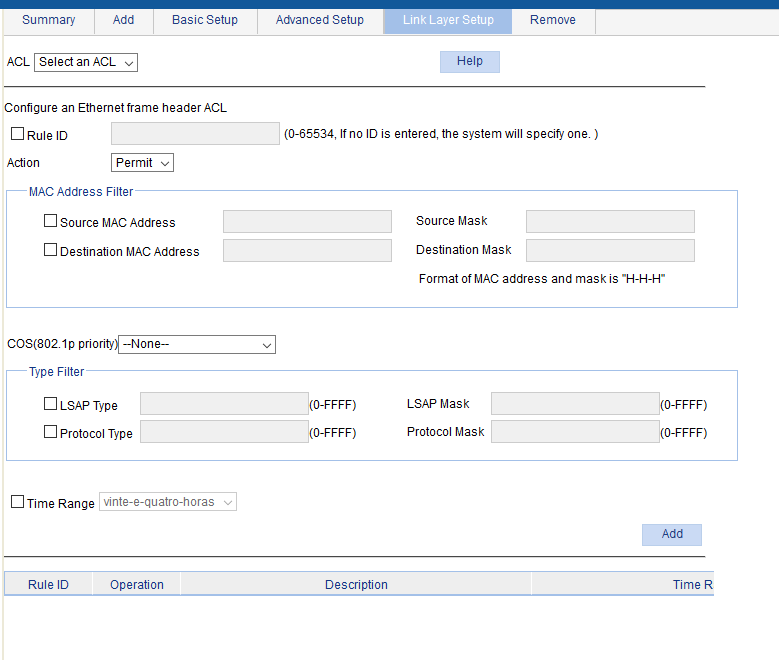
No, I don't want to do the feature "mac authentication". I want do to an ACL layer 2 blocking all mac address and permiting only some macs... look the picture, this screen is intended to create an ACL layer 2 with mac address. There are 2 fields: one to mac adress and right after for the mask. Which options do I have in the field mask? The mask FFFF-FFFF-FFFF is for the exactly mac address... but if I wish to blok all mac address? Which mask do I have to use? And not only this page is necessary to make the acl works, there are other 4 configurations to do, like classifier, behavior, qos policy and finaly port policy. In 2 of them I need to specify the "drop" or "permit", it's ambiguous... make no sense.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2018 01:59 PM
06-15-2018 01:59 PM
Re: Wildcard with macadress switch 1920
I found the solution to block all macs and permit only the authorized macs.
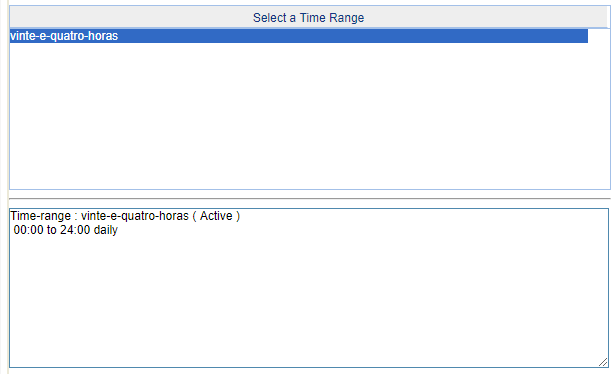
1- Create a time range to make the rules to be active, accordly to your needs.
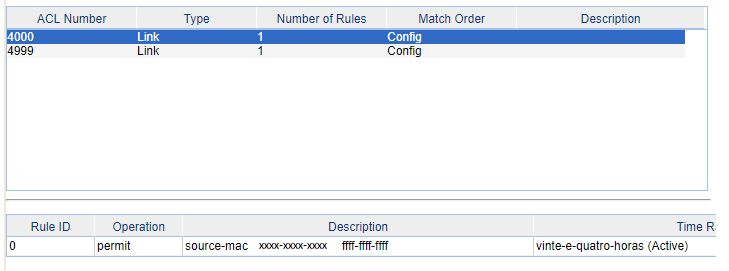
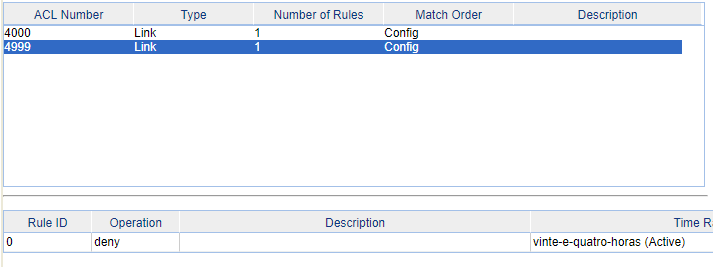
2- Create 2 acls, one to permit the macs (with lower acl number) and another to block all macs (with a higher acl number). In my enviroment, I created the ACL 4000 to permit the macs and the ACL 4999 who is intended to block all other macs. Obviously, the ACL 4000 need to be the "permit" type and the acl 4999 "deny" type. The FFFF-FFFF-FFFF is the maks who identify the exactly mac address, in other means, only the mac who you inform will be authorized on the switch. On the ACL 4999, the source and destination mac can be 0 in each field. Do not forget to inform the time range in each ACL.
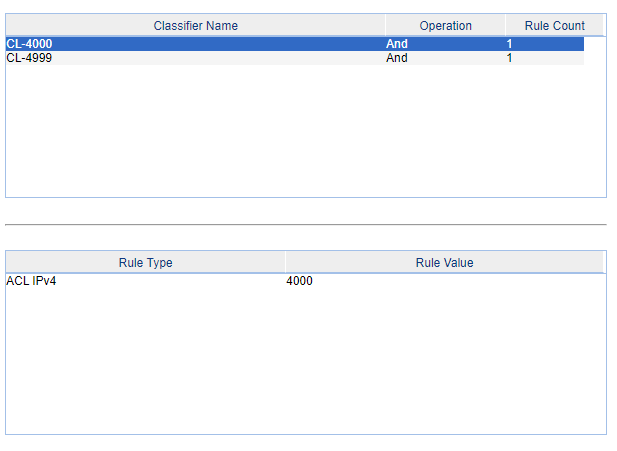
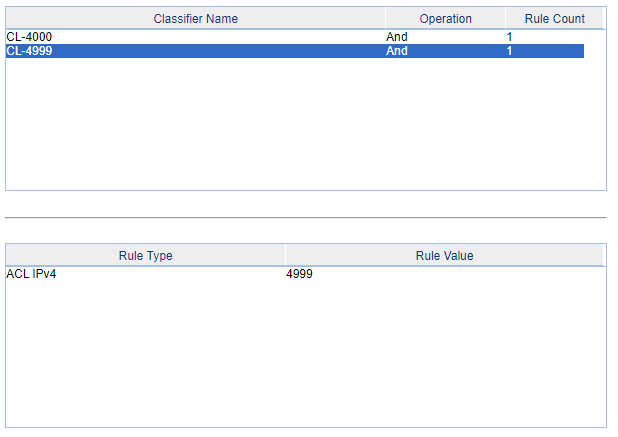
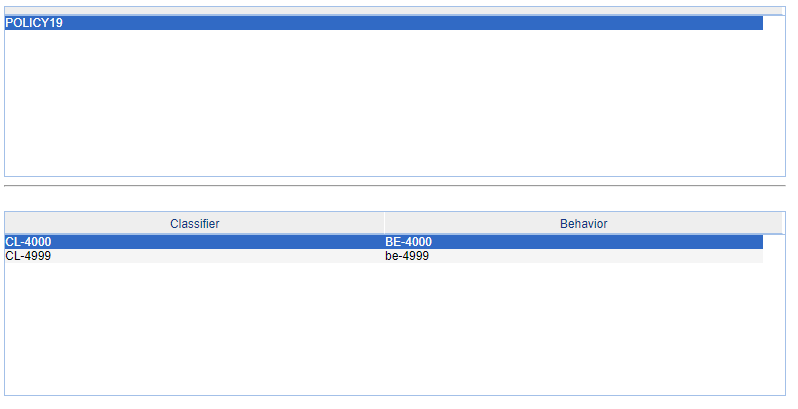
3- Create two classifiers, like below, on for ACL 4000 and another for 4999 ACL.
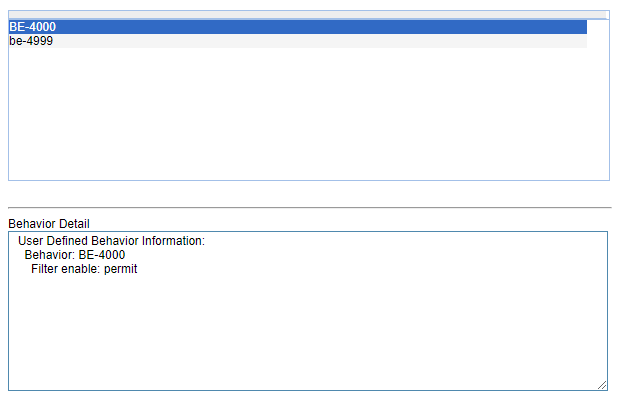
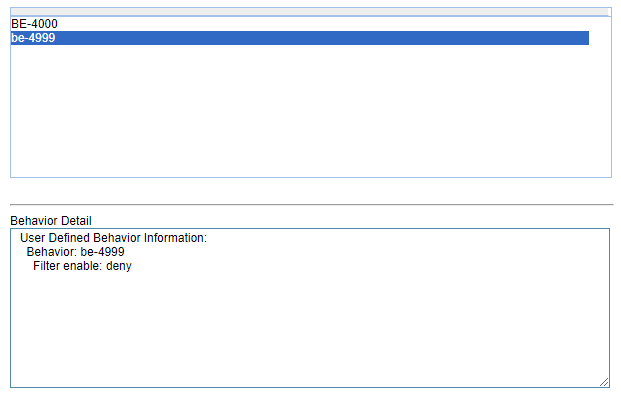
4- Create two behaviors, on for the ACL 4000 and another for ACL 4999. The first behavior must have the option PERMIT and the second will be DENY.
5- Link the behaviors and the classifiers in only one "QOS Policy", like below (the name of the policy is to better indentification when apply to the ports of the switch; the "only one policy" is because each port of the switch permit only one policy each time):
6- Apply the policy to the port accordly to your needs (mine is 19).
That´s it. My switch is running with the 1120 firmware.