- Community Home
- >
- Servers and Operating Systems
- >
- HPE BladeSystem
- >
- BladeSystem - General
- >
- How to disable TLSv1.0 on c7000 Onboard Administra...
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Forums
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2018 08:16 AM
12-20-2018 08:16 AM
Hello,
I am trying to mitigate the SSLv2, SSLv3, TLSv1.0, POODLE vulnerability on a c7000 chassis in both the Onboard Administrator and Virtual Connect Interconnects but am having some difficulty. I have 5 c7000 boxes to address configured in 2 system configurations:
System1 OA3.60 / VCM4.50
System2 OA4.30 / VCM4.50
According this HP Support Communication, (https://h20564.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_n
a-c05157667), it is possible to address the Onboard Administrator provided OA v4.3 or later is installed.
According to the HPE Virtual Connect Manager Command line interface for c-class bladesystem version 4.40/4.41 Documentation (https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=1&ved=2ahUKEwjD4cbJ2a7fAhUBjq0KHZ1dBlgQFjAAegQICRAC&url=https%3A%2F%2Fsupport.hpe.com%2Fhpsc%2Fdoc%2Fpublic%2Fdisplay%3FdocId%3Demr_na-c04562191%26docLocale%3Den_US&usg=AOvVaw3ls1msGT26gnwCtHCGRApv), it is possible to disable TLSv1.0 (p124) on the VCMs.
In my scenarios, I am unable to update the OA on System1 to 4.3+. I tried to update with several SPP packages thinking I may have to step through the udpates: SPP2015.04, SPP2016.10, SPP2017.104, SPP_G7.1, and SPP_Gen8.1. All attempts to update the OA fail with "(Error -3)".
On System2, the OA "Edit Advanced Security Settings" option is not in any of my systems.
In both System configurations, I am unable to disable TLSv1.0. It is not in the GUI or the CLI menus. I have even SSH'd into the VCM, and used CLI command "show ssl" and no TLS option is shown.
Q1: How do you recommend updating the OAs?
Q2: What am I missing to disable the TLSv1.0/POODLE in the VCMs?
Many thanks,
Bobby
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-24-2018 07:00 AM
12-24-2018 07:00 AM
Re: How to disable TLSv1.0 on c7000 Onboard Administrator?
Hello BJohnson101 ,
Indeed the information/documents you shared are accurate. Based on your description I understand that you are trying to upgrade OA via SPP (SUM). If you want to troubleshoot further, once the upgrade fails SUM allows you to expand the error & delve into the text message in order to locate more info on the cause that interrupted the update process.
If for any reason, you still face difficulties via SPP you can always upgrade OA module via the GUI by uploading relevant OA bin file that you can download from the hpe.com site. Relevant option for OA firmware upgrade is under Active OnBoard Administator. You can find more info here: https://support.hpe.com/hpsc/doc/public/display?sp4ts.oid=null&docLocale=en_US&docId=emr_na-c00806740&withFrame by searching firmware update
m_icha
I'm an HPE EmployeeNeed assistance? Contact HPE Support
How to Say Thank You? Just click the KUDOS!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2018 02:30 PM
12-27-2018 02:30 PM
Re: How to disable TLSv1.0 on c7000 Onboard Administrator?
Hi BJohnson101,
For your first query, I see m_icha has provided a response.
For your query regarding vulnarability, check out the below link for SSLv3 POODLE Vulnerability - CVE-2014-3566.
https://www.hpe.com/us/en/services/security-vulnerability.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 11:38 AM
01-02-2019 11:38 AM
Re: How to disable TLSv1.0 on c7000 Onboard Administrator?
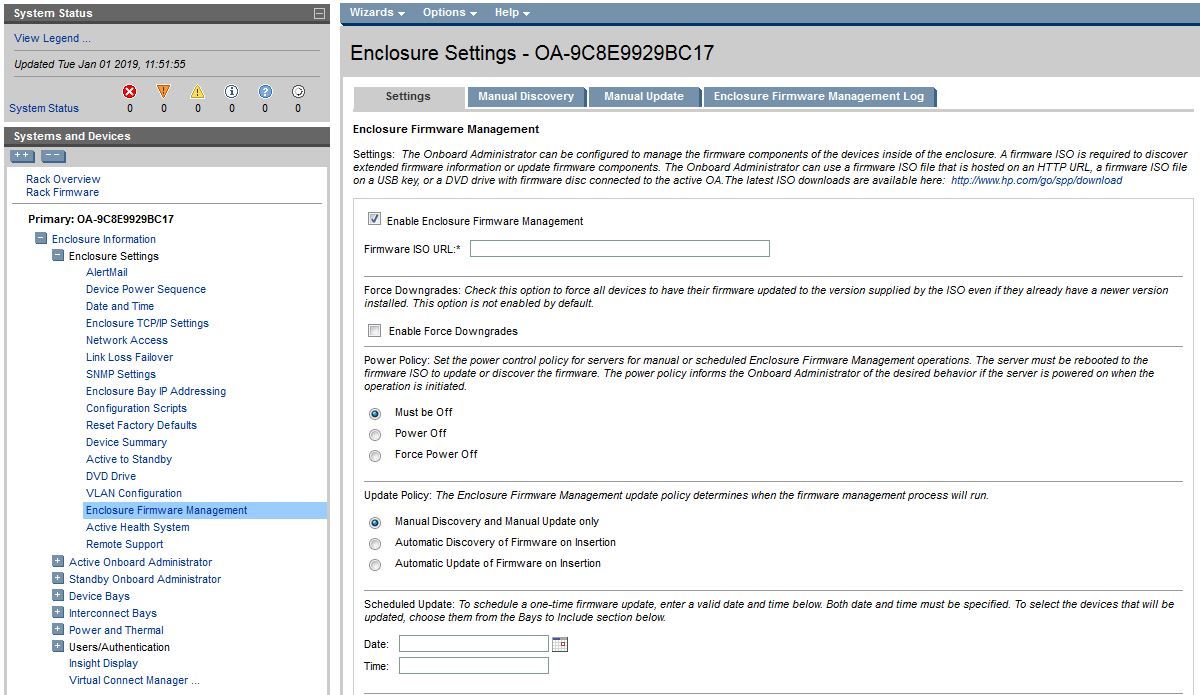
Yes, updating the firmware directly to the OA would be a great idea, but I don't have that option. When i click on Enclosure Information>>Enclosure Settings >> Enclosure Firmware Management >> Settings Tab, I can enable the "Enable Enclosure Firmware Managment" option, but can ONLY utilize a URL. The option to "Browse" to locate a file is not available:
Do you have any other suggestions?
Thanks,
Bobby
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 12:50 PM
01-02-2019 12:50 PM
SolutionNevermind, I now see what I was doing wrong: I should have drilled down into the Enclosure Information >> Active Onboard Administrator >> Firmware update...... NOT the Enclosure Settings.
I have update the FW on the OA and now the TLS options are there to disable.
Thanks everyone!
Bobby