- Community Home
- >
- Software
- >
- HPE Ezmeral: Uncut
- >
- Security that scales: 3 ways policy-based data sec...
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Receive email notifications
- Printer Friendly Page
- Report Inappropriate Content
Security that scales: 3 ways policy-based data security improves data governance

The same lesson applies to handling security for a large-scale enterprise data system: just because you can do something at small scale does not mean it’s practical to do it with consistency in a large, complex system. An even bigger challenge is to be able to make changes efficiently when they are needed. How, for example, do you quickly and accurately change control over who has access when there are millions of files in question?
As a data management professional, you need data infrastructure designed to give you fine-grained control over different types of data and applications in a huge system. Yet, it still must let you implement changes without massive effort. Policy-based security addresses these needs.
What is policy-based security?
Large-scale data systems use a variety of security measures to control who can (and who cannot) access or modify data., The system also must support audits and protect data in motion via wire-level encryption. But policy-based security goes a step further: It lets administrators group the specific security controls needed for each situation into a manageable number of security policies. This capability provides much needed simplicity as the system scales.
Policy-based security is a key feature of the software-based, highly scalable data technology known as HPE Ezmeral Data Fabric File and Object Store, which can store, manage, and move data across an enterprise--from edge to data center, on premises, or in cloud. Introduced in version 6.2, policy-based security makes it easier to apply the variety of data security controls (including ACEs and ACLs) that are built into data fabric.
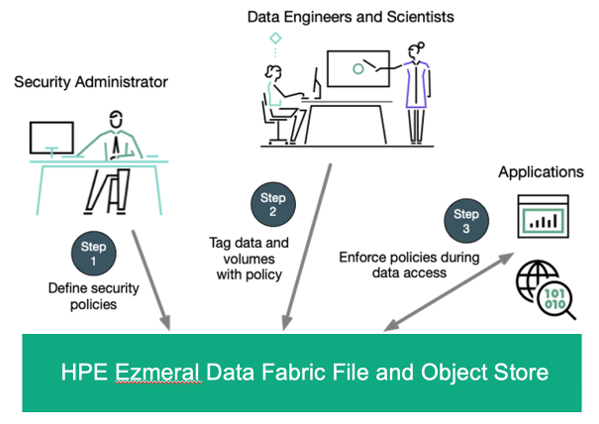
To understand the three ways policy-based security improves data governance, let’s start with how policy-based security works. The process is illustrated in Figure 1.
Figure 1. Steps in using data fabric’s policy-based security
The first step is for a system administrator to define a set of security policies to meet the current needs of the system. This step provides a clue to why policy-based security is so powerful: defining each security policy is done independently of the data structure(s) to which it is intended to apply. This separation is key to the advantages that policy-based security provides, as explained below.
The second step is for the administrator to apply the desired policy to the particular data of interest. And as depicted in Figure 1, the final step is for data fabric to enforce the appropriate policy when applications attempt to access or modify data. The figure shows that volumes as well as other data entities can be tagged with a security policy. A data fabric volume is an important construct in making a large system manageable.
Data fabric volumes play a key role in managing security
With potentially billions of files, tables, and event streams in multiple physical locations, it’s essential to have a way to apply policies consistently across many files and directories so that management is practical in a huge system. HPE Ezmeral Data Fabric File and Object Store provides a data management construct known as a data fabric volume (not to be confused with block storage volumes).
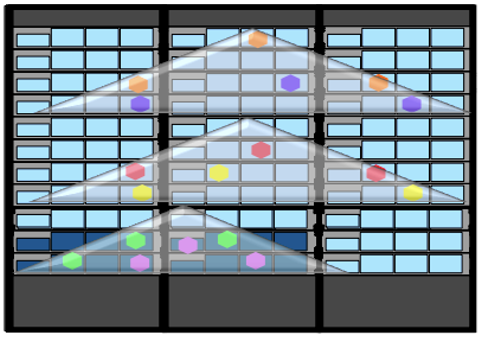
A data fabric volume, shown in Figure 2, essentially acts like a directory with superpowers. It is the highest level at which security policies can be applied to data. Although individual data directories, files, tables, and event streams can also be tagged to apply a security policy, volumes are often the primary point because they let you manage data at scale efficiently, millions of files at a time.
Read the blog post “What’s your superpower for data management?”
Figure 2. Data fabric volumes (triangles) distribute data replicas (hexagons) across cluster
Figure 2 shows that data fabric volumes span a cluster by default, placing data replicas on different machines for data protection.
Now that you have an idea of how policy-based security works, let’s look at three ways it improves data governance.
Benefit 1: Reuse security policies
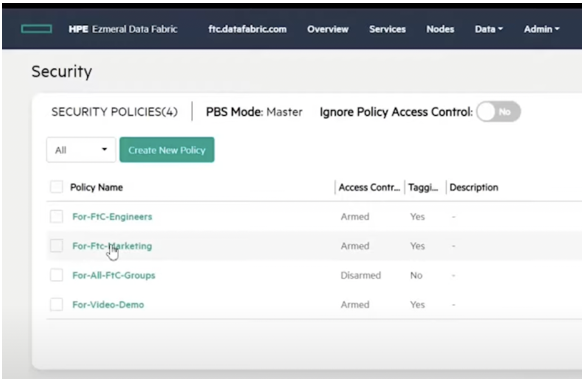
With data fabric’s policy-based security, the policy is applied to entities in the data fabric but defined apart from the data entities to which it applies. This separation means a security can be defined by a compliance specialist but applied by a data engineer. Separation also makes it possible to reuse a security policy, as shown in Figure 3. Using the data fabric’s control plane, you can choose from a list of previously defined policies. Or, if you have sufficient privilege in the system, you can create new data policies.
Figure 3. Data fabric control system: create a new security policy or select a pre-existing one
Being able to reuse a security policy is a particular advantage in a large, complex system with many users, petabytes or more of data, and millions of files and directories. Reuse of a policy not only simplifies defining a security policy, it also reduces the risk of error. This advantage improves the consistency of data governance.
The figure above is a screen capture from a video by Eric Brown, Technical Solutions Engineer with HPE Storage.
Watch the full video “HPE Ezmeral Data Fabric 6.2 Policy-Based Security”
Benefit 2: Single point for change
What happens when a security policy needs to change? Making consistent adjustments to permissions across millions or even billions of data entities can be a big challenge in complex systems at scale, but HPE Ezmeral Data Fabric File and Object Store’s policy-based security makes change much quicker, easier, and more accurate. Separation of policy definition from the data to which it applies creates a single point to adjust security features.
Having a single point of change lets administrators modify the policy centrally, without having to update permissions individually on potentially millions of files or directories. Once the change has been made centrally by the administrator, the data fabric platform then enforces the new policy accordingly, controlling access or modification permissions for all data previously tagged for that policy. Making the change centrally also means that a change can take place in seconds rather than over a period of hours as would happen if data entities are changed individually.
The video demonstrates how the policy can be changed without even mentioning the data.
Having a single point for change of security requirements is a big advantage for handling real-world practicalities in a large-scale system. This benefit, along with the ability to reuse a security policy, improves data governance by making it more likely you can execute security strategies accurately and consistently. But while doing data security well is essential, it’s quite another thing to be able to conclusively demonstrate you’ve done it correctly.
Benefit 3: Better transparency for audit
Policy-based security provides big advantages when it comes to a data audit. An audit is an exercise in proving something to a human. By defining security requirements centrally through security policies, rather than laboriously and potentially inconsistently for individual data objects, it becomes easier to demonstrate security has been handled correctly. This advantage is particularly important in large and complex systems. Simplifying the process of executing your security strategies makes it more likely you’ve done it correctly and more likely you can demonstrate that convincingly to an auditor.
Better data governance
Policy-based security makes uniform, platform-level security easier and more consistent to apply or modify and easier to verify yourself or to an outside auditor. It’s a way to deliver excellent data governance even in a large-scale system over time, in good time, and without missing a beat.
To find out more about HPE Ezmeral Data Fabric File and Object Store, read this solution brief. For more on data security in large-scale systems, take advantage of free training with HPE Ezmeral Learn On-demand courses on data security including “Securing the Ezmeral Data Fabric”.
Ellen Friedman
Hewlett Packard Enterprise
Ellen_Friedman
Ellen Friedman is a principal technologist at HPE focused on large-scale data analytics and machine learning. Ellen worked at MapR Technologies for seven years prior to her current role at HPE, where she was a committer for the Apache Drill and Apache Mahout open source projects. She is a co-author of multiple books published by O’Reilly Media, including AI & Analytics in Production, Machine Learning Logistics, and the Practical Machine Learning series.
- Back to Blog
- Newer Article
- Older Article
- SFERRY on: What is machine learning?
- MTiempos on: HPE Ezmeral Container Platform is now HPE Ezmeral ...
- Arda Acar on: Analytic model deployment too slow? Accelerate dat...
- Jeroen_Kleen on: Introducing HPE Ezmeral Container Platform 5.1
- LWhitehouse on: Catch the next wave of HPE Discover Virtual Experi...
- jnewtonhp on: Bringing Trusted Computing to the Cloud
- Marty Poniatowski on: Leverage containers to maintain business continuit...
- Data Science training in hyderabad on: How to accelerate model training and improve data ...
- vanphongpham1 on: More enterprises are using containers; here’s why.
- data science course on: Machine Learning Operationalization in the Enterpr...