- Community Home
- >
- Software
- >
- HPE OneView
- >
- OneView CERT
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Forums
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2018 01:58 PM
03-15-2018 01:58 PM
I am trying to import a cert from my windows CA DC to my new 4.0 OneView appliance.
I am first generating the CR from the OneView appliance. Then I create it from my Windows CA using teh WebServer2048 option.
I keep getting the below error message: The certificate is not valid
Unable to import signed certificate.
Extended Key Usage(EKU) field in the certificate does not contain Server Authentication and/or Client Authentication
Resolution Provide a valid certificate with EKU field set as specified
If the issue persists, Create a support dump and contact your authorized support representative for assistance.
Please advise...
Scott
Solved! Go to Solution.
- Tags:
- certificate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2018 03:14 PM - edited 03-15-2018 03:15 PM
03-15-2018 03:14 PM - edited 03-15-2018 03:15 PM
Re: OneView CERT
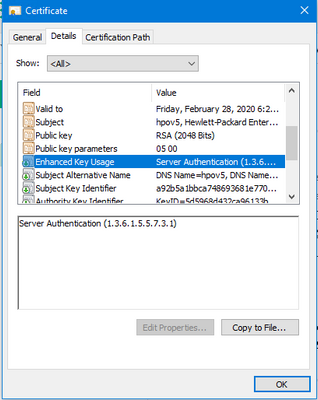
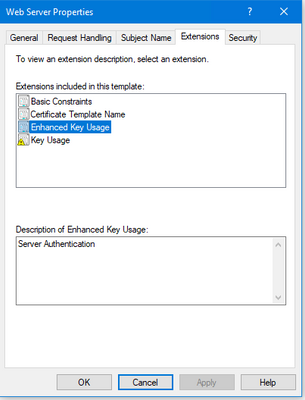
The message is quite clear what is wrong. The SSL certificate you created must contain the Server Authentication attribute set. Take a look at the screenshot of a certificate deployed on my appliance.
I'm also attaching the Web Server Certificate Template policy I used on my Windows Server 2016 CA
[Any personal opinions expressed are mine, and not official statements on behalf of Hewlett Packard Enterprise]

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2018 07:11 PM
03-15-2018 07:11 PM
Re: OneView CERT
Thanks for your reply Chris! I see the buck stops with you here in the OneView forums.
So I generated the certificate request through the "Guided Section" area on my OneView appliance(4.00.07-0330056). I then generated the cert from my Windows 2012 CA utility seen in the attachment. I selected the "WedServer2048" for the Certificate Template. I do not have a certificate template for Server authenication. So I am a little confused on how to create the certificate properly. The install guide does not talk much about installing a cert on the appliance.
Thanks for any assistance. As you can tell, cert management is not my speciality.
Any additional info woudl be great.
Thanks in advance, Scott
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2018 07:22 PM
03-15-2018 07:22 PM
Re: OneView CERT
The reason why we don't document the CA part is that every customer is different, and uses different enterprise CA products. Since you are using Microsoft Enterprise Certificate Authority Services, it's quite simple. On your Issuing CA, you need to make sure a Web Server Template is available, or a CA Template Policy that is configured with the Enhanced Key Usage policy I showed in the screenshot. Also, review these Microsoft Technet links (Link1 and Link2) on how to configure a Certificate Template Policy. Even though those links are for Windows Server 2003, they still apply to Server 2008, Server 2012 and Server 2016.
[Any personal opinions expressed are mine, and not official statements on behalf of Hewlett Packard Enterprise]

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2018 11:34 PM
04-12-2018 11:34 PM
Re: OneView CERT
I too have had this error, however my WebServer template does allow for EKU and the certificate does show Server Authentication as a valid purpose (same as in your certificate as shown).
We too are using MS CA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2018 07:32 AM
04-13-2018 07:32 AM
Re: OneView CERT
You need both Server AND Client authentication. Do you have both?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2018 12:14 AM
05-25-2018 12:14 AM
Re: OneView CERT
I have the same issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2018 05:34 AM
05-29-2018 05:34 AM
Re: OneView CERT
You need to make sure that your CA honours the request for the EKU fields Server Authentication and Client Authentication. One or both of these are missing from the certificate generated by your CA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2018 04:34 AM
06-01-2018 04:34 AM
SolutionHello Scott,
that's what I've got (after some lengthy discussion) from HPE support:
If you create a Certificate Signing Request (CSR) in OV, it will request the following usages:
X509v3 Key Usage:
Digital Signature, NonRepudiation, Key Encipherment
X509v3 Extended Key Usage:
TLS Web ServerAuthentication, TLS Web Client Authentication
If you submit this CSR to your CA, the resulting certificate should contain all these features.
Make sure, that your CA will generate a ceritifcate that includes ALL of above.
Had to get our CA team to try several times, until OneView was satisfied with the generated certificate.
Regards,
Daniel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2018 01:27 PM
06-04-2018 01:27 PM
Re: OneView CERT
Duplicate WebServer template, check ServerAuth and add ClientAuth, add Non Repudiation... add Template in your CA and Works!
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2021 08:45 AM - edited 02-03-2021 08:50 AM
02-03-2021 08:45 AM - edited 02-03-2021 08:50 AM
Re: OneView CERT
Here's the steps for someone using a Microsoft cert authority in their windows domain.
- Create the cert request from Oneview
- Log into Oneview and from the NAV in the top left select Settings.
- Click on Security
- In the Actions menu top right, select Create appliance certificate signing request
- Fill in the details and click OK to get the large text block containing the base64 encoded cert request.
- Copy the cert request to your clipboard or save the text in Notepad.
- Create a certificate template that OneView will be happy with.
- On your Windows CA, open the "Certification Authority" app.
- In the tree on the left side, right-click on Certificate Template and select Manage.
- Scroll down to Web Server and right-click select Duplicate Template
- On the General tab, tweak the names to your liking. I use "HPE OneView".
- On the Extensions tab, click Application Policies and click Edit. Add Client Authentication. Click OK. You should now have both Server Authentication and Client Authentication.
- On the same Extensions tab, click Key Usage and click Edit. Checkmark "signature is proof of origin (nonrepudiation)". Ensure Allow key exchange only with key encryption (key encipherment) radio button is selected. Click OK.
- On the Security tab, apply read and enroll to whichever user account will be requesting the cert from this CA (ie: domain admins, your windows account, etc). I use my domain admin account.
- Click OK/Apply and close editing that template.
- Back at the main Certification Authority screen, right click again on the Certificate Template folder and select New -> Certificate Template to issue.
- Choose the certificate template you just duplicated (in my case: HPE OneView).
- Verify that you see it in the list.
- Request the certificate from your CA using the new template
- Open a web browser and navigate to your CA's webpage. In my case: http://dc09/certsrv
- Click on "Download a CA Certificate, certificate Chain, or CRL
- Select Base64 and click Download CA Certificate - Name it CA-cert.txt and save it somewhere.
- Go back to the home page and click Request a Certificate
- Click Advanced Certificate Request
- Click Create and Submit a request to this CA.
- Paste in the base64 text copied from step 1 and in Certificate Template select the template name you just created, in my case HPE OneView.
- Click Submit.
- Select Base64 encoded and click Download Certificate, save the file oneview.txt.
- Import both the CA and the server certificate into Oneview.
- Back on the Security settings page of OneView, click on Actions > Manage Certificates
- Click Add Certificate
- Using Notepad, open the CA-cert.txt file you downloaded in step 3-3 above. Copy and paste the base64 text into the dialog and then click Add.
- Assuming no issues, close that page and then click Actions > Import Appliance certificate.
- Open the oneview.txt cert downloaded in step 3-9 above and copy/paste the text into this Import cert dialog.
- Click OK and if all goes well, no errors and the system will import the cert.
Next time you browse the page you should get a happy cert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2024 10:48 AM
03-07-2024 10:48 AM
Re: OneView CERT
Followed @CorbettEnders detailed directions, worked perfectly for us!
Only addition was giving the user that was doing the certificate intall enrollment rights on the certificate template.