- Community Home
- >
- Networking
- >
- IMC
- >
- [SOLVED] LDAPs fails
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Forums
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2020 08:55 AM - edited 05-22-2020 12:57 AM
05-18-2020 08:55 AM - edited 05-22-2020 12:57 AM
[SOLVED] LDAPs fails
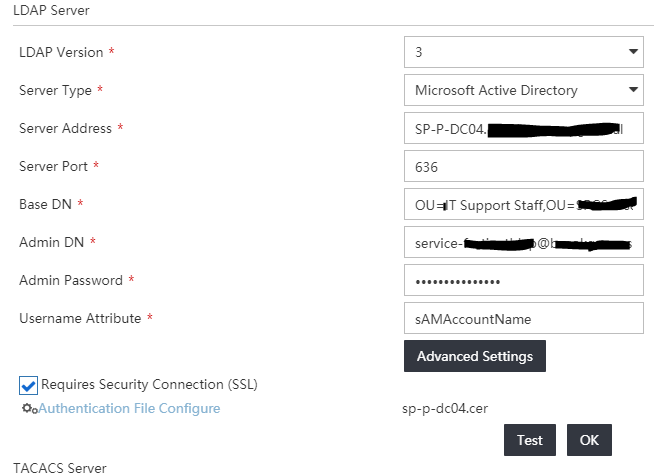
javax.naming.CommunicationException: simple bind failed: SP-P-DC04.brookgreen.spgs.local:636 [Root exception is javax.net.ssl.SSLHandshakeException: No trusted certificate found]
I have RootCA (MS ADCA) in every keystore on the IMC server that I think could be used.
Certificate is based on:
Template=LDAPoverSSL(1.3.6.1.4.1.311.21.8.16574533.5077679.4147093.4566469.16611918.39.9795857.15890548)
Major Version Number=100
Minor Version Number=3
It drives me nuts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2020 11:08 AM
05-21-2020 11:08 AM
Re: LDAPs fails
Anybody any ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2020 05:00 PM
05-21-2020 05:00 PM
Re: LDAPs fails
i tried to make it work as well. i had my DC certsrv issue a client cert to the user logging into LDAP/DC and uploaded that to imc. I figured it wanted a client cert that the DC would recognixe and It all looks ok. WIreshark shows it fails.
So I went back to the docs. They have an example but not for secure LDAp over SSL, so no help there as to how to set up the cert.
Looks like its broken unless someone else has made it work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2020 12:44 AM - edited 05-22-2020 12:59 AM
05-22-2020 12:44 AM - edited 05-22-2020 12:59 AM
Re: LDAPs fails
Well, my AD server definitely works with LDAPs (LDAP over SSL) as tested with ldp.exe
Certificate was issued by MS ADCA as per this or even better this
Just to make sure I did follow the bit in above writeup - Exporting the LDAPS Certificate and Importing for use with AD DS
And once imported to NTDS\Personal IMC was OK to use provided certificate & do LDAPs connection!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2020 03:01 PM - edited 05-27-2020 08:49 AM
05-26-2020 03:01 PM - edited 05-27-2020 08:49 AM
Re: LDAPs fails
Thanks!
Those links were helpful. My main misunderstanding was regarding the uploaded certificate in the IMC config.
I assumed it was supposed to be a client cert issued to the IMC server, NOT the cert created using the LDAP over SSL template and issued to the DC
Now it works
EDIT: downside, I'm running active and standby. The standby gets its configuration for this through the nightly backup as there is no option to configure much on the standby server. The regular LDAP config gets synced, but the LDAP over SSL does not get correctly configured. So make sure you have a local admin account configured as no authentication sever will be available.