- Community Home
- >
- Servers and Operating Systems
- >
- Servers & Systems: The Right Compute
- >
- Securing containers across your IT ecosystem
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Forums
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Receive email notifications
- Printer Friendly Page
- Report Inappropriate Content
Securing containers across your IT ecosystem

Why containers? Simply put, containers offer an efficient way to develop and deploy microservices. (Go deeper in HPE’s definition of what containers are. Docker also offers a great explanation.)
A container makes an ideal platform for running tools and to manage micro service-based applications. This means that, in turn, containers provide an ideal platform to meet rapidly evolving DevOps infrastructure needs—where time to market is critical. At the same time, security is an equally important element to consider when planning your entire containerized IT infrastructure.
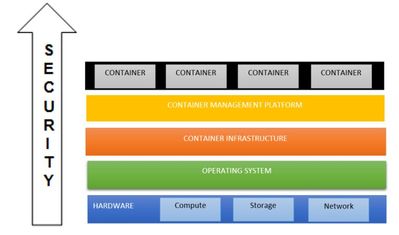
Taking a containerized IT ecosystem overview
To secure a containerized IT ecosystem, you need to understand its fundamentals. Here are the high-level components of a typical containerized IT ecosystem.
Securing containerized IT ecosystems holistically
HPE solutions offer a holistic approach to securing complete ecosystems, including servers, storage, networking or operating systems. This includes:
Silicon Root of Trust
Secure data begins with secure infrastructure. With HPE Gen10 Servers, HPE offers the first industry-standard servers to include a silicon root of trust built into the hardware. This creates a digital footprint in silicon and ensures that servers will never boot with compromised firmware.
Storage Encryption
Persistent storage is an important element in container ecosystem design. This helps store and retrieve data within a container in addition to sharing data across containers. HPE direct-attach storage solutions provide Smart Array Secure Encryption. This is a controller-based data-at-rest encryption solution for any SAS/SATA drive connected to the HPE Smart Array Controller or HPE Smart Host Bus Adapter. Storage arrays for performance such as HPE 3PAR StoreServ or HPE Nimble all-flash storage provide data-at-rest encryption solution and predictive analysis via HPE InfoSight.
Network Security
Container ecosystems provide network connection options like bridge, IPvLAN and overlay. Apart from the normal methodologies of securing data in transit, Arista switches provide Macro-Segmentation Service (MSS) to complement micro-segmentation implemented as part of most software-defined data center network deployment. MSS provides dynamic and scalable network functions to insert security into the path of traffic. This is regardless of whether the security service or workload is physical or virtual and is enabled with automatic and seamless service insertion. Typical scenarios like securing server-to-server network traffic and monitoring and securing management interfaces can be handled efficiently with MSS
Operating System
Operating system security (OS security) is the process of ensuring OS integrity, confidentiality and availability. OS security refers to specified steps or measures used to protect the OS from threats, viruses, worms, malware or remote hacker intrusions. HPE Workload Aware Security for Linux (WASL) provides security compliance to industry standards for Linux operating system instances. Automating security compliance across your servers and workloads can be as simple as a single-click from a centralized dashboard.
Container Infrastructure
When it comes to secure container infrastructure, you should consider these guidelines:
- Run integrity checks on container images and digitally sign them at build time
- Leverage solutions like Security-Enhance Linux (SELinux) or AppArmor to customize specific security profiles and guard against unauthorized access. HPE Workload Aware Security for Linux (WASL) provides standard security templates which can be leveraged
- Scan containers for vulnerabilities in all registries
- Protect secrets such as passwords and API keys required for run-time container access by using third party tools or key management services
- Reduce your risk by running application containers in read-only/non-persistent mode when required
You need to constantly monitor and protect the run-time environment. Understanding normal application network behavior and enacting a security policy to enforce authorized connections are equally important. Monitoring every container for abnormal behavior or policy violations needs to be considered too.
Container Management Platform
With both hardware and container infrastructure secured, you are ready to consider these best practices for securing your container management platform:
- Don’t install unvetted or unapproved images
- Run compliance checks of your management environment
- Use third-party container security solution such as Aqua or Sysdig that integrate well with your management platform
Keep in mind that you need to monitor every container for abnormal behavior or policy violations.
A strong security strategy for your container IT ecosystem is your best defense
Securing your IT container ecosystem is similar to securing your physical or virtual machine infrastructure. Your underlying infrastructure for the container ecosystem should be your strongest defense. It’s no longer adequate to limit security to firewalls. Arming your business with the latest security innovations will help you prevent, detect and recover from security attacks. Keep in mind that security and monitoring go hand in hand and are always a work in progress.
HPE solutions provide you with a foundation on which you can build a secure containerized Infrastructure. Please contact your HPE representatives for further discussion.
If you are ready to embark on your journey to containerization, you might want to check this out: Containers Dummies Guide. (Registration required to download.)
Meet Infrastructure Insights blogger Edwin Anthony Joseph, Infrastructure 
Solution design, documentation, implementation and evangelization-focused architect/engineer with broad experience across private, hybrid and public cloud platforms with both Microsoft/Linux technologies such as virtualization, containers and converged solutions. A total of 14+ years IT experience with an interest inIT security along with emerging technology and trends. An avid reader, on a relentless path to “self-discovery” with an “always -earning” attitude and a “be the change” approach alongside melodious music and food.
Infrastructure Insights
Hewlett Packard Enterprise


- Back to Blog
- Newer Article
- Older Article
- PerryS on: Explore key updates and enhancements for HPE OneVi...
- Dale Brown on: Going beyond large language models with smart appl...
- alimohammadi on: How to choose the right HPE ProLiant Gen11 AMD ser...
- ComputeExperts on: Did you know that liquid cooling is currently avai...
- Jams_C_Servers on: If you’re not using Compute Ops Management yet, yo...
- AmitSharmaAPJ on: HPE servers and AMD EPYC™ 9004X CPUs accelerate te...
- AmandaC1 on: HPE Superdome Flex family earns highest availabili...
- ComputeExperts on: New release: What you need to know about HPE OneVi...
- JimLoi on: 5 things to consider before moving mission-critica...
- Jim Loiacono on: Confused with RISE with SAP S/4HANA options? Let m...
-
COMPOSABLE
77 -
CORE AND EDGE COMPUTE
146 -
CORE COMPUTE
161 -
HPC & SUPERCOMPUTING
138 -
Mission Critical
88 -
SMB
169