- Community Home
- >
- Networking
- >
- Switching and Routing
- >
- WAN Routing
- >
- HPE MSR954 VPN site to site
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Forums
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2018 09:48 PM
09-27-2018 09:48 PM
Hi, i need to setup an VPN to connect 2 site.
both location using HPE MSR954 with static IP.
Can anyone guide me how to set it?
Thanks a lot
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2018 12:30 AM
09-28-2018 12:30 AM
Re: HPE MSR954 VPN site to site
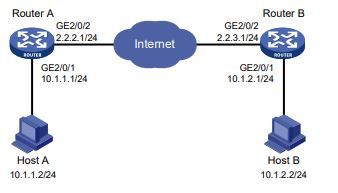
Example:
Configuration procedure
1. Configure Router A:
# Configure IP addresses for interfaces. (Details not shown.)
# Configure an ACL to identify data flows from subnet 10.1.1.0/24 to subnet 10.1.2.0/24.
<RouterA> system-view
[RouterA] acl advanced 3101
[RouterA-acl-ipv4-adv-3101] rule permit ip source 10.1.1.0 0.0.0.255 destination
10.1.2.0 0.0.0.255
[RouterA-acl-ipv4-adv-3101] quit
# Configure a static route to Host B. The command uses the direct next hop address (2.2.2.3)
as an example.
[RouterA] ip route-static 10.1.2.0 255.255.255.0 gigabitethernet 2/0/2 2.2.2.3
# Create an IPsec transform set named tran1.
[RouterA] ipsec transform-set tran1
# Specify the encapsulation mode as tunnel.
[RouterA-ipsec-transform-set-tran1] encapsulation-mode tunnel
# Specify the security protocol as ESP.
[RouterA-ipsec-transform-set-tran1] protocol esp
# Specify the ESP encryption and authentication algorithms.
[RouterA-ipsec-transform-set-tran1] esp encryption-algorithm aes-cbc-128
[RouterA-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[RouterA-ipsec-transform-set-tran1] quit
# Create a manual IPsec policy entry with the name map1 and the sequence number 10.
[RouterA] ipsec policy map1 10 manual
# Apply ACL 3101.
[RouterA-ipsec-policy-isakmp-map1-10] security acl 3101
# Apply the IPsec transform set tran1.
[RouterA-ipsec-policy-isakmp-map1-10] transform-set tran1
# Specify the local and remote IP addresses of the IPsec tunnel as 2.2.2.1 and 2.2.3.1.
[RouterA-ipsec-policy-isakmp-map1-10] local-address 2.2.2.1
[RouterA-ipsec-policy-isakmp-map1-10] remote-address 2.2.3.1
# Apply the IKE profile profile1.
[RouterA-ipsec-policy-isakmp-map1-10] ike-profile profile1
[RouterA-ipsec-policy-isakmp-map1-10] quit
# Apply the IPsec policy map1 to interface GigabitEthernet 2/0/2.
[RouterA] interface gigabitethernet 2/0/2
[RouterA-GigabitEthernet2/0/2] ip address 2.2.2.1 255.255.255.0
[RouterA-GigabitEthernet2/0/2] ipsec apply policy map1
[RouterA-GigabitEthernet2/0/2] quit
2. Configure Router B:
# Configure IP addresses for interfaces. (Details not shown.)
# Configure an ACL to identify data flows from subnet 10.1.2.0/24 to subnet 10.1.1.0/24.
<RouterB> system-view
[RouterB] acl advanced 3101
[RouterB-acl-ipv4-adv-3101] rule permit ip source 10.1.2.0 0.0.0.255 destination
10.1.1.0 0.0.0.255
[RouterB-acl-ipv4-adv-3101] quit
# Configure a static route to Host A. The command uses the direct next hop address (2.2.3.3)
as an example.
[RouterB] ip route-static 10.1.1.0 255.255.255.0 gigabitethernet 2/0/2 2.2.3.3
# Create an IPsec transform set named tran1.
[RouterB] ipsec transform-set tran1
# Specify the encapsulation mode as tunnel.
[RouterB-ipsec-transform-set-tran1] encapsulation-mode tunnel
# Specify the security protocol as ESP.
[RouterB-ipsec-transform-set-tran1] protocol esp
# Specify the ESP encryption and authentication algorithms.
[RouterB-ipsec-transform-set-tran1] esp encryption-algorithm aes-cbc-128
[RouterB-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[RouterB-ipsec-transform-set-tran1] quit
# Create and configure the IKE keychain named keychain1.
[RouterB] ike keychain keychain1
[RouterB-ike-keychain-keychain1] pre-shared-key address 2.2.2.1 255.255.255.0 key
simple 123456TESTplat&!
[RouterB-ike-keychain-keychain1] quit
# Create and configure the IKE profile named profile1.
[RouterB] ike profile profile1
[RouterB-ike-profile-profile1] keychain keychain1
[RouterB-ike-profile-profile1] match remote identity address 2.2.2.1 255.255.255.0
[RouterB-ike-profile-profile1] quit
# Create an IKE-based IPsec policy entry with the name use1 and the sequence number 10.
[RouterB] ipsec policy use1 10 isakmp
# Apply ACL 3101.
[RouterB-ipsec-policy-isakmp-use1-10] security acl 3101
# Apply the IPsec transform set tran1.
[RouterB-ipsec-policy-isakmp-use1-10] transform-set tran1
# Specify the local and remote IP addresses of the IPsec tunnel as 2.2.3.1 and 2.2.2.1.
[RouterB-ipsec-policy-isakmp-use1-10] local-address 2.2.3.1
[RouterB-ipsec-policy-isakmp-use1-10] remote-address 2.2.2.1
# Apply the IKE profile profile1.
[RouterB-ipsec-policy-isakmp-use1-10] ike-profile profile1
[RouterB-ipsec-policy-isakmp-use1-10] quit
# Apply the IPsec policy use1 to interface GigabitEthernet 2/0/2.
[RouterB] interface gigabitethernet 2/0/2
[RouterB-GigabitEthernet2/0/2] ip address 2.2.3.1 255.255.255.0
[RouterB-GigabitEthernet2/0/2] ipsec apply policy use1
[RouterB-GigabitEthernet2/0/2] quit
Verifying the configuration
# Initiate a connection from subnet 10.1.1.0/24 to subnet 10.1.2.0/24 to trigger IKE negotiation. After
IPsec SAs are successfully negotiated by IKE, the traffic between the two subnets is IPsec
protected.
# Use the display ipsec sa command to display IPsec SAs on Router A and Router B. This example
uses Router A to verify the configuration.
[RouterA] display ipsec sa
-------------------------------
Interface: GigabitEthernet2/0/2
-------------------------------
-----------------------------
IPsec policy: map1
Sequence number: 10
Mode: ISAKMP
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Path MTU: 1443
Tunnel:
local address: 2.2.3.1
remote address: 2.2.2.1
Flow:
sour addr: 2.2.3.1/0.0.0.0 port: 0 protocol: ip
dest addr: 2.2.2.1/0.0.0.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 3769702703 (0xe0b1192f)
Connection ID: 1
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 3000/28800
SA remaining duration (kilobytes/sec): 2300/797
Max received sequence-number: 1
Anti-replay check enable: N
Anti-replay window size:
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 3840956402 (0xe4f057f2)
Connection ID: 2
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 3000/28800
SA remaining duration (kilobytes/sec): 2312/797
Max sent sequence-number: 1
UDP encapsulation used for NAT traversal: N
Status: Active
Please refer below document for "Configuring IPsec "

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2018 06:26 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2018 08:20 PM
09-30-2018 08:20 PM
Re: HPE MSR954 VPN site to site
Hi, i managed to set it from telnet.
but when i come to the local-address.
it show
[LION_NEWOFFICE-ipsec-policy-manual-map1-10]local-address x.x.x.x
^
% Unrecognized command found at '^' position.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2018 08:13 PM
10-09-2018 08:13 PM
Re: HPE MSR954 VPN site to site
what is current version on device..?