- Community Home
- >
- Storage
- >
- Around the Storage Block
- >
- Mitigating the Impact of Ransomware with HPE and V...
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Receive email notifications
- Printer Friendly Page
- Report Inappropriate Content
Mitigating the Impact of Ransomware with HPE and Veeam
The “WannaCry” ransomware attack was unprecedented in scale and impact. Here’s how best practice data protection from HPE and Veeam mitigates one of the most feared threats for IT environments.

This highly malicious strain of malware—first developed by the US National Security Agency and subsequently stolen by cybercriminals and hackers—exploited a Windows operating system vulnerability (for which Microsoft released a security patch in March) and combined with a worm application to spread rapidly across networks in different sectors across the world. The virus rapidly locked up files in more than 200,000 PCs in governments, hospitals and major companies across 150 countries while demanding money (in the form of bitcoins) in return for unlocking encrypted files.
Organizations infected by the virus have included Germany's rail network Deutsche Bahn (where hacked train and departure boards led to a temporary return to chalk and blackboards), Spanish telecommunications operator Telefonica, US logistics giant FedEx and Russia's interior ministry. One of the most seriously impacted victims of the ransomware attack was the National Health Service in the UK where some hospitals were forced to cancel outpatient appointments.
The rise of ransomware
The “WannayCry” virus is the latest and highest profile example of a rapid growth in ransomware attacks which are exploiting regulatory and compliance demands, vulnerable networks, and poor data protection best practices.
As the threat escalates, users across more verticals and businesses of all sizes are being targeted and exploited. Even with strong cyber security solutions and practices, networks are consistently penetrated. The FBI reported that victims paid $209M to ransomware criminals in Q1 2016 and were on pace to reach $1 billion in 2016. And that doesn’t include the costs to remediate attacks or the productivity and reputational impact, and nor does it include unreported attacks. According to a now highly prescient report from the Institute for Critical Infrastructure Technology (ICIT), 2017 was expected to be a year in which ransomware wreaks havoc on companies.
So for any business, the question is no longer this: “Will I be a victim of ransomware?” Instead it’s: “Will I be prepared when ransomware attacks?”
How to mitigate the impact of ransomware
There are some obvious steps that all organisations need to take to avoid ransomware attacks. Keep all your software up to date, perform a threat analysis with your security team (including penetrating testing to find any vulnerabilities) and train your staff on cyber security best practices (not opening attachments or links from unknown sources and informing employees if a virus reaches the company network). But with ransomware threats becoming more frequent and complex, organizations also need to ensure that they mitigate the impact of ransomware by adopting common best practices for data protection. Once attacked, you have two courses of action; pay the ransom (with no guarantee of the recovery of the encrypted files or that a reinfection won’t occur) or restore your data as quickly and reliably as possible.
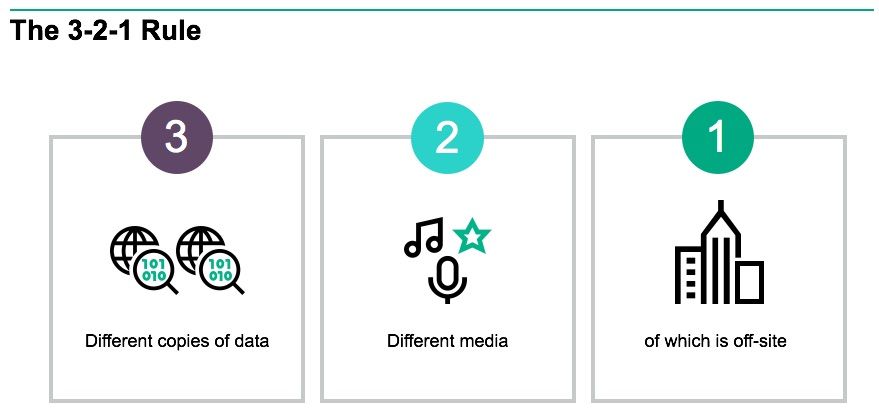
One of the timeless data protection rules that can effectively mitigate a ransomware attack is called the 3-2-1 rule which prescribes that you should:
- Have at least three copies of your data—the primary data and two copies—to avoid losing data to a faulty backup.
- Store the copies on two different types of media—such as tape, disk, secondary storage, or cloud.
- Keep one backup copy offsite—either on tape or in the cloud—in the event of local hazards or ransomware infections within the network.
Following the 3-2-1 rule will mean you always have an available and useable backup of your data and systems, and in a world where ransomware can instantly take you offline, that’s a vital precaution.
In addition, performing regular risk assessments should be part of your overall data protection strategy to proactively identify potential risks. As part of the risk assessment, you need to be able to verify that data is recoverable and that it can be restored quickly and easily.
How to follow the 3-2-1 best practice data protection rule with HPE and Veeam
Veeam’s integration with HPE storage solutions lets you create application-consistent backups from HPE 3PAR StoreServ and HPE StoreVirtual snapshots for fast and efficient data protection. For long-term external storage, HPE StoreOnce provides deduplication for efficient storage utilization and fault isolation for data. StoreOnce can copy backups to HPE StoreEver tape storage or to the cloud for long-term offsite data archival. This strategy enables you to meet the “3-2-1 rule” of data protection—where there are three copies of the data, on two different media types, and one copy is kept offsite.
Veeam and HPE solutions overview
Veeam and industry-leading HPE solutions are fully equipped for businesses of all sizes to mitigate ransomware attacks and protect data.
- Rapid data restores and recovery—HPE Storage Snapshots enables fast virtual machine (VM) and granular recovery to override encrypted ransomware databases, applications, files, and operating systems (OS). Recover quickly and avoid application downtime with proven integration with HPE 3PAR StoreServ, Store Virtual, StoreOnce and StoreOnce Catalyst.
- Infrastructure lockdown—Ransomware can’t infect what it doesn’t see. HPE makes this possible through an integration with StoreOnce Catalyst based repositories which are not directly accessible by the OS. This makes backup images invisible and inaccessible to ransomware, thereby making restore possible. An additional layer of protection is added through offline StoreEver tape and asynchronous remote replication copies.
- Testing environment—Test and remove ransomware items quickly before restoring VMs to production with Veeam On-Demand Sandbox™ and Veeam SureBackup.
- Built-in ease of use—Leverage the built-in backup assessment to ensure your critical VMs are protected with the Veeam ONE™ monitoring, reporting and capacity planning tool.
These capabilities are standard with the Veeam Availability Suite™ and HPE storage combined integration. This solution does not require any special scripts and leverages standard HPE and Veeam products. Veeam software products are now available from HPE via the HPE Complete program, so you can source all components of the 3-2-1 best practice data protection ecosystem from a single vendor.
The bottom line
The chaos unleashed by the “WannaCry” virus shows why ransomware attacks represent such a serious threat to organizations across multiple industries worldwide. While the HPE Veeam 3-2-1 best practice data protection solution doesn’t prevent ransomware, it does enable companies to quickly and effectively restore critical data infected by ransomware to a known good “production ready” state.
Find out more
Ransomware: Holding data hostage – business white paper
Protect your data from malicious ransomware threats – solution brief
Meet Around the Storage Block blogger Simon Watkins, WW Product Marketing Manager, Data Availability and Protection, HPE Storage.
xxx
- Back to Blog
- Newer Article
- Older Article
- Back to Blog
- Newer Article
- Older Article
- haniff on: High-performance, low-latency networks for edge an...
- StorageExperts on: Configure vSphere Metro Storage Cluster with HPE N...
- haniff on: Need for speed and efficiency from high performanc...
- haniff on: Efficient networking for HPE’s Alletra cloud-nativ...
- CalvinZito on: What’s new in HPE SimpliVity 4.1.0
- MichaelMattsson on: HPE CSI Driver for Kubernetes v1.4.0 with expanded...
- StorageExperts on: HPE Nimble Storage dHCI Intelligent 1-Click Update...
- ORielly on: Power Loss at the Edge? Protect Your Data with New...
- viraj h on: HPE Primera Storage celebrates one year!
- Ron Dharma on: Introducing Language Bindings for HPE SimpliVity R...