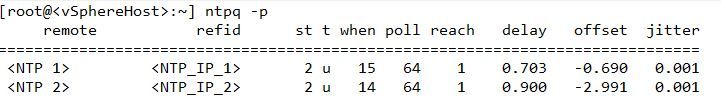- Community Home
- >
- Software
- >
- HPE OneView
- >
- OneView - Server NTP configuration hijacked
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Forums
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-29-2020 09:11 PM
02-29-2020 09:11 PM
OneView - Server NTP configuration hijacked
I understand why each system's clock needs to be confifured to use the same time across the board. That's why everysystem should be pointed to a valid NTP server. If I didn't have an NTP server already, I'd appreciate the NTP server service that comes built in with my freshly deployed HPE OneView Appliance...
Yes, I searched the forums and read a couple of posts where other users had similar concerns. The posts I read were responded to... I'm asking a similar question again because the answers I read are unacceptable. The kind of unacceptable that could prevent further implementation.
I work for a companty that has switches, servers, storage arrays, and who knows what else deployed to 300+ sites across the US. Syncronizing time across each site was a problem, 20 years ago. Since then a robust NTP infastructure has been deployed, and every device is already configured to use our own local NTP servers - Hard to justify using OneView as an NTP server where you are already pulleding a Stratum-2 time.
I can't be the only one with this problem? There's got to be some other users out there who have run into the same problem... Some other users who were not happy to find their NTP settings had been overwritten...
Is there a way to override / disable the NTP configuration changes that OneView makes when systems are managed by OneView?
If there's no way to override the changes when systems are added to OneView, has anyone come up with a creative solution?
As it stands today, my firewall team will not allow connectivity from end devices to my OneView Appliance on UDP-123, so now instead of pointing to "a stratum-2 NTP server" my systems are pointed to an NTP server that does not exist / is not accessible.
Should I stop where I am.... Power my VM down... and move on to some other problem?
Thanks for the Rant!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2020 04:40 AM
03-02-2020 04:40 AM
Re: OneView - Server NTP configuration hijacked
There is no way to override / disable the NTP configuration changes that OneView makes when systems are managed by OneView.
HPE advise to set the appliance to use a specific NTP server or servers, or your Hypervisor host. The reason of doing this is, we don't want logs that OneView records are different time than the iLO time.
[Any personal opinions expressed are mine, and not official statements on behalf of Hewlett Packard Enterprise]

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2020 07:13 AM
03-02-2020 07:13 AM
Re: OneView - Server NTP configuration hijacked
> If I didn't have an NTP server already, I'd appreciate the NTP server service that comes built in with my freshly deployed HPE OneView Appliance...
That is not really what OneView is offering here. The best practice is to have an NTP server configured in OV and then OV can push that setting to all the managed devices. So OV is strictly a NTP client of your NTP server. On a VM, by default OV uses the VM host as it's NTP server and assumes you have configured the hypervisor host appropraitely as an NTP client to your NTP server. Same applies to Synergy Composer - you are expected to configure NTP server there as well.
> As it stands today, my firewall team will not allow connectivity from end devices to my OneView Appliance on UDP-123, so now instead of pointing to "a stratum-2 NTP server" my systems are pointed to an NTP server that does not exist / is not accessible.
That is the real issue here. If there was a OV feature to allow you to configure per-device NTP servers, would it be the same set of NTP servers for a single OV instance? That would be easy to support. Or would a single OV instance have to support managed devices that each could habe a separate set of NTP servers? In that case it couldn't be a server profile attribute. or you'd end up with server profile bloat. How would you envision it working?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2020 10:43 PM
03-02-2020 10:43 PM
Re: OneView - Server NTP configuration hijacked
Thanks to the failures of those before me, i prefer to NOT synchronize any of my VMs with the hosting hypervisor. The stories... And the reasons why i shouldn't / 2ae scolded for correcting the host whose time was off by 3 days... Let's just say i didn't agree!
Best practice to configure OV to point to an NTP server - won't catch me arguing here. I didn't know it was a best practice, but it works with NTP, so i configure it!
I think you hit the nail on the head with your last comment. If there was an OV feature that allowed me to point OV to "NTP-1" and "NTP-2", while also allowing managed devices to point to "NTP-1" and "NTP-2"... Then i think that would solve my problem.
Using OV as an NTP server for synergy blades in the same enclosure, makes enough sense... Can't really argue it. In my case i am trying to use the Virtual OV, for a couple of seemingly simple reasons. Since it's forced upon us with each Synergy, using the same tool, same GUI, same processes to manage non-Synergy pizza boxes and enclosures seemed like a good idea. A real improvement over the firmware was updated "when the server was installed, 7 years ago" or "when we ran into a problem that we couldn't figure out, so it seemed like a good idea.". It's hard enough to convince management to take a system out of production, the easier it is to deploy updated firmware and drivers, the better!
To answer your question - "If there was a OV feature to allow you to configure per-device NTP servers, would it be the same set of NTP servers for a single OV instance?" - Yes it would be the same set of NTP servers per OV instance.
Truth be told, since i couldn't get around this problem... I haven't read enough to know how many OV instances would be required to manage / monitor the systems I'm thinking about. Perfect world, 1 instance in the center of the country would suffice!
Since posting my NTP Rant / disappointment, I've downloaded and deployed a new VM, the iLO Amplifer pack. I intended to connect a couple of systems to it, a small proof of concept to figure out how it worked, figure out if it was easy to use and most importantly figure out if it was the answer to my problems! I was showing one guy what i was working on, he gave me 1 CVS to import... 1500 systems. So much for small proof of concept...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2020 01:51 AM
03-10-2020 01:51 AM
Re: OneView - Server NTP configuration hijacked
As a customer I agree, I would prefer to be able to control if OneView sets NTP for iLO or not. This has been an annoying for myself. When you do a full NTP server setup (at least 4 servers with Stratum 1 or 2 as the masters), I shouldn't be pointing clients at a single source such as a VM instance of OneView.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2020 05:25 AM
03-16-2020 05:25 AM
Re: OneView - Server NTP configuration hijacked
I'm not sure I'm understanding the problem statement? You can tell OneView to use external NTP servers. Using hponcfg you can configure all of your iLOs to use the same NTP servers. Using your appropriate tools, you can set your OS's to use the same NTP servers. I've never seen OneView forcing iLO's or OS's to change their NTP setup. I do think the OneView server profile template should include a setting for the iLO NTP setup. I think I might be missing your point?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2020 12:33 PM
06-24-2020 12:33 PM
Re: OneView - Server NTP configuration hijacked
If I have servers at multiple sites (or in DMZs), using local NTP devices is ALWAYS preferred, as having HPE OneView push NTP to those devices is incredibly stupid. I have complained about this issue since HPE OneView 3.0.
In my use case, we have servers in a DMZ that are monitored by HPE OneView. NTP is blocked on the upstream firewall by-design because we have local NTP servers that we are expected to use. Since the iLOs can't reach HPE OneView for time, they go out of sync. We have to run a script every day to change the NTP settings on every iLO to the correct and desired NTP servers to obtain correct time... and then HPE OneView changes the NTP settings back to itself.
There should be an option at the very least to either use HPE OneView for time or to NOT use it for time so it stops breaking all of our iLOs (can't log in using Active Directory if the time is not correct, and it never is)
FORCING changes to NTP is the absolute WORST design decision and HPE needs to FIX IT!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 02:46 PM
10-27-2020 02:46 PM
Re: OneView - Server NTP configuration hijacked
Just discovered today that all our ILO servers had their time server settings hijacked by OneView, with no indication whatsoever of this occurring during the setup process!
Is it still not possible to disable this and prevent OneView from doing it? Is our only option to manually set the time server for each ILO?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2020 02:53 AM
10-28-2020 02:53 AM
Re: OneView - Server NTP configuration hijacked
We have two oneview instances (5.30) and hundreds of proliant DL360s, DL380s, and DL580s G9 and G10. None of them have had their iLO SNTP settings changed. We have all of the buttons on the SNTP page turned off. Just have the time servers entered and the time zone. If you have any of those buttons turned on, I wonder if that could be causing the problem you are seeing?
It is quite strange. I hope you can find an answer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-10-2020 11:20 AM - edited 11-10-2020 11:41 AM
11-10-2020 11:20 AM - edited 11-10-2020 11:41 AM
Re: OneView - Server NTP configuration hijacked
We also only have the primary time server and time zone entered, with the rest of the settings disabled. (OneView 5.50)
I have confirmed that performing a "Refresh" in OneView for any node will overwrite the existing SNTP settings in the ILO, replacing "Primary Time Server" with the OneView server's IP address. When watching the progress indicator for the Refresh action, one of the readouts is "Configuring NTP..."
In addition to this, any new server added to OneView will have its ILO NTP set to the OneView server's IP address by default, and has to be changed after deployment.
This is unacceptable behavior and I'd like an explanation from HPE as to how we can stop it from happening. I want the ILO NTP setting to be permanent and not subject to being overwritten by OneView (which is using the same server for NTP in its own settings!).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2023 06:45 AM
04-25-2023 06:45 AM
Re: OneView - Server NTP configuration hijacked
We have the same problem.
HPE Oneview Appliance Firmware 8.20.00-0475724
We don't want the ntp servers to be changed. Is there any way to change this behaviour?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2023 04:58 AM
04-27-2023 04:58 AM
Re: OneView - Server NTP configuration hijacked
Hello @Westnetz_GmbH,
Thank you for writing to us! Since you have posted in an old topic and there is no response yet, we would recommend you create a new topic using the create "New Discussion" button, so the experts can check and guide you further.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2023 09:02 AM - edited 05-08-2023 09:03 AM
05-08-2023 09:02 AM - edited 05-08-2023 09:03 AM
Re: OneView - Server NTP configuration hijacked
Yes, adding a new topic for an existing unresolved topic will help soving it.... I don't think so. It would really be better that HPE finally solved this problem. The current behaviour is a no go in our environment as we want to keep control which ntp server is set in which location around the world as we have local ntp servers there. This is currently one of the show stoppers why we canceled our OneView test.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2023 10:55 AM - edited 05-08-2023 10:56 AM
05-08-2023 10:55 AM - edited 05-08-2023 10:56 AM
Re: OneView - Server NTP configuration hijacked
Well that's too bad. If you had created a topic I might have noticed sooner.
This is a global setting, you cannot say "don't touch the iLO" but you can put them in OneView and set the iLO to use those (not to redirect it to use OneView as the time service):
I work at HPE
HPE Support Center offers support for your HPE services and products when and how you need it. Get started with HPE Support Center today.
[Any personal opinions expressed are mine, and not official statements on behalf of Hewlett Packard Enterprise]

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2023 10:49 PM - edited 05-08-2023 10:50 PM
05-08-2023 10:49 PM - edited 05-08-2023 10:50 PM
Re: OneView - Server NTP configuration hijacked
Not sure what you want to tell me with that. I know that I can configure OV to either push its own addreess or the configured ntp servers in OV (in our case 3 servers) to the ILOs. But this does not help, you can only configure a fixed set of ntp servers. We have ntp servers around the world as network latency is sometimes an issue, so the ILOs should use the same local ntp server as all other devices in a location.
OV should simply not touch existing ntp settings! I set ntp and other ILO stuff in an ansible script + rest api. Maybe it would make sense that OV sets ntp server if nothing is configured yet, but last time I checked OV just overwrote settings.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2023 11:40 AM
05-09-2023 11:40 AM
Re: OneView - Server NTP configuration hijacked
I am confirming there is no way to not configure ntp as has been stated multiple times prior. This is a design choice as HPE OneView was not intended to span a scope beyond a single datacenter or a local region and the time must be synchronized with HPE OneView source (yes, it technically could be done externally) otherwise it cannot manage those iLO. It is reasonable to request that ntp, like local iLO accounts, be left alone -or- managed by HPE OneView.
I work at HPE
HPE Support Center offers support for your HPE services and products when and how you need it. Get started with HPE Support Center today.
[Any personal opinions expressed are mine, and not official statements on behalf of Hewlett Packard Enterprise]

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2023 10:51 PM
05-09-2023 10:51 PM
Re: OneView - Server NTP configuration hijacked
I'm not sure about OV only supporting one data center, at least in GUI you can configure/add multipe data centers in FACILITIES -> Data Centers. Maybe this is only meant as rooms not data centers. When we talked to HPE reps about our use cases nobody mentioned that we need to setup one OV instance per location. Which is also a no go in our case.
Regarding ntp, why not make ntp part of a server profile or as config option for the server hardware? Then you can decide which ntp to use at which location/server. I just don't see a technical reason why it has to be implemented like it is now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2023 03:05 AM
05-10-2023 03:05 AM
Re: OneView - Server NTP configuration hijacked
Hi guys,
Good day.
I'd like to share my use case here FYI,
1. Add server hardware as monitored into OV, (the NTP will be overwritten with the OV IP address)
2. Manually reset the NTP setting via PowerShell,
Set-HPILONetworkSetting -Server $server -Username xxx -Password xxx -DisableCertificateAuthentication -DHCPSNTP $DHCP_SNTP_SETTINGS_ENABLE -SNTPServer1 $SNTP_SERVER1 -SNTPServer2 $SNTP_SERVER2 -Timezone $TIMEZONE
after that, both OV and server hardware are working fine, and I didn't see any errors, so far so good.
Thanks