- Community Home
- >
- Servers and Operating Systems
- >
- Servers & Systems: The Right Compute
- >
- A secure supply chain: the foundation to zero trus...
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Forums
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Receive email notifications
- Printer Friendly Page
- Report Inappropriate Content
A secure supply chain: the foundation to zero trust
Data centers are only as strong as the supply chain foundation they’re built on. And supply chain attacks are getting exponentially worse. Learn how to respond with a 360-degree view to security.
Data is the new currency of the 21st century and securing this valuable commodity is of the upmost importance for any organization seeking to safeguard critical and sensitive data. However, securing your data center is only as strong as the supply chain foundation it is built upon. Any disruptions and risk to the integrity of the products or services being delivered can have long lasting damaging operational, financial and brand consequences.
Many of us in the IT security space probably remember the major data breaches that Target and Home Depot suffered within mere months of each other. Target estimated the total cost of their data breach to had been $202 million, whereas Home Depot estimated their total cost to have been $198 million.
Fast forward to today, and the pandemic has opened cybersecurity gaps in the supply chain leading to more companies finding themselves on the wrong side of headlines—most notably the SolarWinds attack that reported the emergence of counterfeit hardware and the critical infrastructure ransomware attack on the Colonial Pipeline.
Supply chain attacks have only gotten exponentially worse over the years, increasing 42% in the first quarter of 2021 according to the Identify Theft Resource Center (ITRC)—a trend that appears to be here to stay. The severity of these attacks have prompted organizations to challenge IT security leaders to implement a zero-trust framework. In fact, President Joe Biden has found the threat to be so intrusive that in a recent Executive Order on Improving the Nation’s Cybersecurity sets a strict 180-day deadline from May 12th, 2021 for all federal civilian executive branch entities to adopt zero trust architectures.
The continued threat to the supply chain mean that vendors must build the technology and feature sets that enable Zero Trust architectures and mechanisms that continuously validate the provenance, security, and trustworthy state of their products throughout their lifecycle. For hardware suppliers, this means that features must be included to validate the hardware, firmware and software of the shipped products continuously.
A supply chain is only as strong as its most vulnerable entity

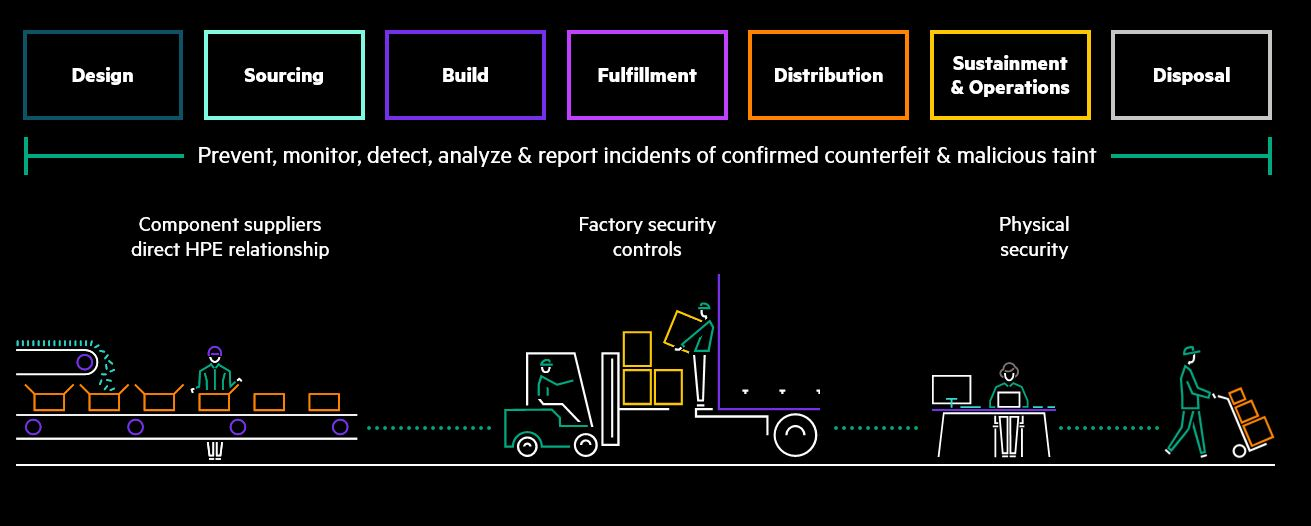
Your servers are only as secure as the supply chain they are built upon. Hewlett Packard Enterprise (HPE) delivers the world’s most secure industry-standard server portfolio that provides an enhanced holistic, 360-degree view to security that begins in the manufacturing supply chain and concludes with the safeguarded, end-of-life decommissioning.
From materials suppliers to logistics and transportation services, and production and assembly to warehousing and distribution, HPE suppliers are required to comply with company policies, as well as International Organization for Standardization (ISO) standards and the Defense Federal Acquisition Regulation Supplement (DFARS).
The HPE supply chain global operations compliance is assured through risk-based security audits, program monitoring, inspection of electronic parts, component traceability, and material control processes. These extreme practices are taken to prevent, monitor, detect, analyze and report incidents of confirmed counterfeit and malicious taint to all HPE products—providing organizations and businesses with the peace of mind that their HPE products arrive to them unharmed and untampered from any nefarious actors.
Raising the bar in supply chain security
HPE started building the groundwork for a zero-trust architecture with the introduction of HPE-exclusive silicon root of trust back in 2017 with HPE Gen10 servers. The silicon root of trust provides an immutable digital fingerprint in the HPE Integrated Lights-Out (iLO) silicate—validating the lowest level of firmware to BIOS and software to ensure the system is secure and in a known good state before the server even boots.
Continuing on that journey HPE has introduced new innovations in HPE Gen10 Plus servers to further provide organizations the tools to enable a zero-trust architecture in their IT environments. With HPE iLO Advanced, business can take advantage of these advanced security and smart remote technologies ensuring trustworthy and strong authentication without compromise.
When your server is in the factory on the production floor, HPE personnel binds them with a unique device identifier known as the iLO iDevID. Once a server is issued an identifier, a certificate signing request is sent to HPE’s Certificate Authority where it is signed and protected by FIPS 140-2 Level 3 Validated Hardware Security Modules—regardless of what occurs in the OS, these credentials will stay with the server for the duration of its lifetime.
Before your server ships out of the factory, HPE customers can enable server configuration lock, using a password, to prevent any unauthorized changes or tampering with the server after production or in transit. Once server configuration lock is enabled a digital fingerprint of the server configuration is created logging all firmware, hardware components and options—if any unauthorized alterations are detected the server will brand the server unbootable. If an unauthorized configuration change has occurred, the administrator must enter the server configuration lock password to review the issue and continue the startup process.
Complementing and reinforcing server configuration lock is the chassis intrusion detection device. This feature registers an alert if the top of the server chassis is removed—logging an audit alert in the iLO firmware, even if the server does not have power. If any attackers or unauthorized personnel open the server chassis, the administrator will be notified that the server has potentially been tampered with.
Expanding on server configuration lock, platform certificates verify that the system is unmodified from when it was shipped from the factory and can detect if the system had been tampered with in the supply chain during shipment. These certificates allow customers to identify devices that have been tampered with or may have a bad or outdated version of software running on them, or even if there are counterfeits. Together, these advanced security features offer customers a way to validate the authenticity of the server—delivering confidence that the server has not been altered providing a foundation for zero trust architectures.
HPE Trusted Supply Chain
Bringing HPE’s global supply chain operations and secure supply chain features together to provide an experience that delivers protection for your most sensitive applications and data is the HPE Trusted Supply Chain.
Assembled in secure HPE facilities to the most stringent Country of Origin USA and conformance requirements, each server from the HPE Trusted Supply Chain is inspected to be free from malicious microcode and counterfeit parts, safeguarding it against cyber-exploits throughout its lifecycle.
The HPE Trusted Supply Chain experience offers hardened protection designed into select HPE servers with unrivaled supply chain visibility and standards compliance providing a 360-degree view and mitigation plan for current and emerging cyber threats.
Doubling down on your server protection with vetted HPE employees assigned to the product build to manage the product manufacturing process that adheres to the strictest sourcing, inspection and traceability standards. Organizations can even request delivery from a dedicated truck driver with security and HPE personnel to set up the servers.
Only HPE Trusted Supply Chain provides a first line of defense against cyber attackers with select servers built to the world’s toughest security standards in secured facilities—bringing together security, processes, and people to deliver unrivaled protection. This ensures peace of mind that all server components are assembled domestically, without passing through the hands of anybody but highly-vetted HPE employees.
Security where and when you need it
HPE continues to provide best-in-class security solutions and extend our leadership as a trusted security partner to navigate the threats of today and tomorrow. Watching the recent prevailing trends of the supply chain, we’ve taken security of production and supply chain to new heights.
Organizations require security that goes beyond the firewall and software to protect the heart of the infrastructure, starting with the supply chain. Security is only as strong as the layer below the point of attack and HPE world’s most secure-industry standard servers portfolio provides an enhanced zero trust, 360-degree security view that begins in the manufacturing supply chain and concludes with a safeguarded end-of-life decommissioning.
Learn more here or reach out to our security experts at ComputeSecurity@hpe.com
Related articles:
- How do we trust the untrustable? via HPE's Enterprise.nxt
- Security: The foundation for transformation success via HPE's Enterprise.nxt
- Constant scrutiny is the key to making zero trust happen via HPE's Enterprise.nxt
- Stay current on top tech trends and expert advice. Sign up for the weekly newsletter.
Ruben Ramirez
Hewlett Packard Enterprise
twitter.com/HPE_Servers
linkedin.com/showcase/hpe-servers-and-systems/
hpe.com/servers
Ruben_Ramirez
Ruben Ramirez is a WW Product Marketing Manager for Hewlett Packard Enterprise. As an experienced product marketing professional serving enterprise technology companies, Ruben excels at bringing new technologies to market, and helping to create compelling value propositions for customer business needs. Currently Ruben is responsible for bringing to market HPE composable infrastructure, and the world’s most secure industry standard server technologies.
- Back to Blog
- Newer Article
- Older Article
- PerryS on: Explore key updates and enhancements for HPE OneVi...
- Dale Brown on: Going beyond large language models with smart appl...
- alimohammadi on: How to choose the right HPE ProLiant Gen11 AMD ser...
- ComputeExperts on: Did you know that liquid cooling is currently avai...
- Jams_C_Servers on: If you’re not using Compute Ops Management yet, yo...
- AmitSharmaAPJ on: HPE servers and AMD EPYC™ 9004X CPUs accelerate te...
- AmandaC1 on: HPE Superdome Flex family earns highest availabili...
- ComputeExperts on: New release: What you need to know about HPE OneVi...
- JimLoi on: 5 things to consider before moving mission-critica...
- Jim Loiacono on: Confused with RISE with SAP S/4HANA options? Let m...
-
COMPOSABLE
77 -
CORE AND EDGE COMPUTE
146 -
CORE COMPUTE
155 -
HPC & SUPERCOMPUTING
138 -
Mission Critical
88 -
SMB
169