- Community Home
- >
- Servers and Operating Systems
- >
- Servers & Systems: The Right Compute
- >
- Staying ahead of security threats
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Receive email notifications
- Printer Friendly Page
- Report Inappropriate Content
Staying ahead of security threats
HPE understands how small to midsize business operates: its custom tailored security solutions provide much-needed protection for the many organizations under this umbrella.
It’s far, far easier to avoid or otherwise steer around security issues than it is to find and fix them. That’s because the costs of reporting, remediation, and repair can be high enough to threaten business viability. Indeed, that goes double for smaller operations where unexpected and unplanned for costs can cause incredible difficulties.
Thus, understanding and preparing for security threats and vulnerabilities is an essential strategy to ensure (and allow) business success. Ultimately, managing security means managing and limiting risk. This involves a three-step process from which no business, no matter how small, is exempt:
Step 1: Identify those threats and vulnerabilities that might (or do) pose risks to the business, and assess potential impacts or consequences.
Step 2: Among items that do incur actual risks, prioritize them according to their costs or impact, so that the costliest or most damaging is addressed first, and so forth, in decreasing order.
Step 3: For items that warrant a response, set up risk mitigation and action plans to address them.
Best practice, particularly in businesses too small to support in-house security capability, is to subscribe to a threat intelligence and remediation service. This lets businesses outsource the security function to a seasoned and capable out-of-house team. Indeed, HPE and partners can help, and can identify, prioritize, and remediate security risks as part of their various security service offerings.
With cloud everything changes, security included
Organizations of all sizes and scales are buying into the cloud. The ever-increasing number of cloud-based subscriptions and services introduces new and vexing threat vectors. Adding cloud into the mix makes for a more complex security situation. It also ups the ante for—and the importance of—a proper security posture and sufficient robustness and resilience in IT infrastructures. Most experts recommend that businesses undertake the following tasks to ensure they can establish and maintain a proper security posture:
- Align security strategy to business priorities: By understanding and filling the gaps between cybersecurity and business priorities, key players (management, stakeholders, and technology pros) can bring security strategy in line with business priorities. This also helps make sure resources and budgets match up. First and foremost, business leaders must agree on their security priorities and risk profiles.
- Make security-first the watchword: Putting an emphasis on security helps businesses to thrive in an uncertain world rife with risks and threats. Protecting vital assets becomes a shared responsibility for all players. This means investing in staff security awareness (it’s a leading contributor to cyber risk). It also means that everyone will understand and work to avoid, mitigate and handle cyberthreats.
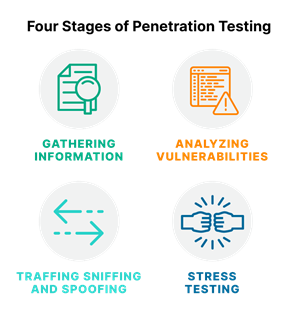
- Do unto yourself, before others do unto you: Cyber vulnerability analysis, aka security or penetration testing, means understanding your attack surfaces, and fixing vulnerabilities before attacks exploit them. This process is depicted in Figure 1, which shows the four stages of penetration testing (pen testing).
How HPE (and partners) can help you secure IT
HPE and its partners offer businesses a broad range of cybersecurity solutions. All are designed to be comprehensive, innovative, robust, and affordable. In fact, HPE’s security capabilities cover the gamut from hardware all the way to users and systems on the network edge. The prime objectives are to gather and analyze intelligence to track threats constantly, to secure systems and services in businesses against those threats, and to advise and assist clients in managing and minimizing the security risks they must face.
Download the full tech brief “2022 Global Study on Closing the IT Security Gaps” to learn more about critical IT security needs. Let HPE provide insight, assistance, and security solutions to protect your very small, small, or midsize business from damage, loss, and harm. For more information, visit the HPE Small and Midsize Business IT Solutions page.
Meet our Compute Experts guest blogger Ed Tittel, technology writer/consultant
Ed Tittel is a longtime IT industry writer and consultant who covers tools, technologies, and security topics. He’s a regular contributor to ComputerWorld, TechTarget, and GoCertify. To learn more, please visit edtittel.com
- Back to Blog
- Newer Article
- Older Article
- Back to Blog
- Newer Article
- Older Article
- PerryS on: Explore key updates and enhancements for HPE OneVi...
- Dale Brown on: Going beyond large language models with smart appl...
- alimohammadi on: How to choose the right HPE ProLiant Gen11 AMD ser...
- ComputeExperts on: Did you know that liquid cooling is currently avai...
- Jams_C_Servers on: If you’re not using Compute Ops Management yet, yo...
- AmitSharmaAPJ on: HPE servers and AMD EPYC™ 9004X CPUs accelerate te...
- AmandaC1 on: HPE Superdome Flex family earns highest availabili...
- ComputeExperts on: New release: What you need to know about HPE OneVi...
- JimLoi on: 5 things to consider before moving mission-critica...
- Jim Loiacono on: Confused with RISE with SAP S/4HANA options? Let m...
-
COMPOSABLE
77 -
CORE AND EDGE COMPUTE
146 -
CORE COMPUTE
154 -
HPC & SUPERCOMPUTING
137 -
Mission Critical
87 -
SMB
169




