- Community Home
- >
- Services
- >
- The Cloud Experience Everywhere
- >
- Cyber security awareness: How to establish an effe...
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Forums
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Receive email notifications
- Printer Friendly Page
- Report Inappropriate Content
Cyber security awareness: How to establish an effective program
In today’s challenging environment, cyber security awareness programs must deliver much more than just the ability to check a compliance box. Here’s a straightforward model to ensure that your training is really changing behavior.

Let’s not be too hard on ourselves though. It was only ten years ago that security was far down on the list of priorities and not at the top of every agenda as it is today. In fact, in the past, cybersecurity training was managed by human resources, whereas today it quite rightly comes under the office of the chief information security officer (CISO). Or at least it should. So, how should we address security awareness today? The answer may sound simple—we need to “change people’s behavior”—but that is easier said than done. The good news is that help is available.
The following simple outline shows the essential components of an effective security awareness solution. It is generic enough for any organization to use as a starting point to create a program that meets your specific and unique needs, adding a practical and effective component to zero-trust best practices.
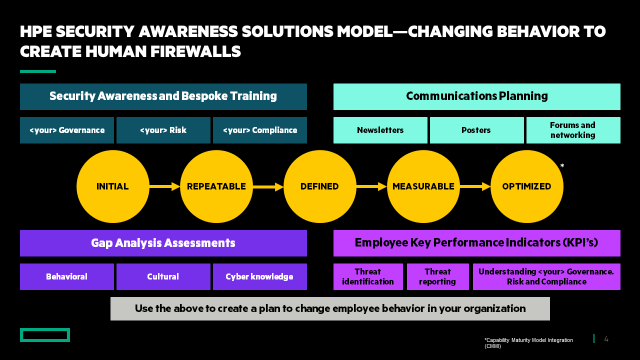
Common components of an effective cyber security awareness solution
The image below shows the HPE Security Awareness Solutions Model. Throughout the model (see the middle of the graphic—represented by the yellow circles) is the well-known Capability Maturity Model Integration (CMMI) from Carnegie Mellon University. You can work on several maturity steps at any one time—you do not necessarily have to complete one before starting the other.
Let’s look at the other major components of the model:
1. Security Awareness and Bespoke Training. Security awareness training is normally provided by a third-party specialist through short eLearning modules. It’s important to consider multi-language capability.
Consider also eLearning delivery options. When it comes to learning, one size does not fit all. By this I mean that individuals have different learning preferences—traditional self-paced, web-based training; “listen to an expert”; “live action”; “host-led animation”; “interactive”; “gamification”; and more. These eLearning options make the program most effective and accelerate security awareness adoption.
Help your learners involve family and friends ─ If possible, choose a program that includes subjects like “Keeping Your Kids Safe Online.” Sharing training helps people internalize the training themselves. One way to do this may involve enabling learners to take a laptop home so they can show family members the content that they have been provided. Explain why your organization provides this training and its importance in keeping everyone safe. Remind them that by keeping themselves safe, they are also keeping their friends safe. Make sure they’re aware of your organization’s policies and that they should not leave their laptop where it might be vulnerable to theft or unintentional misuse.
I have used the phrase “creating human firewalls” for years, and this still resonates with people by generating feelings of empowerment and contribution.
Bespoke Training is the second part of this component of the model. It’s important that you deliver training that provides awareness to reflect the way your organization looks at, and deals with, cybersecurity. Your employees will want to understand the potential harm/cost to the organization ─ using external examples is helpful.
2. Gap Analysis Assessments. We know how important it is to identify the gaps in your current approach. Here are three potential areas for assessment: behavioral, cultural, and cyber knowledge.
We encourage you to evaluate each category with a standalone assessment using short and unambiguous questions. This assists in mapping awareness training to specific groups within the organization to make your program more effective. It’s important to select a team to review the questions/answers beforehand, test the questionnaires on a specific group, and analyze the output to determine if you can act on the results. However, you’ll want to avoid creating questions to suit any pre-conceived answers that you are looking for.
3. Communications Planning. The way you communicate is critical to your success. If communications sound like directives or rules that must be obeyed, you can expect pushback (this is a natural human response). Look at the outcomes you are trying to achieve and communicate with those outcomes in mind. Remember, we need employees to help us combat cyber threats, however they manifest themselves.
A good starting point is to record a short presentation by your CEO or a senior leader, and another by your CISO (or equivalent), one supporting the other. This provides employees with context—as well as a feeling of worth and guidance— on how they can assist in combatting cyber threats. When creating a critical line of defense, the value of employees should not be underestimated.
There are many effective options for communicating (newsletters, posters, forums etc.) about cybersecurity. You need planning and a coordinated approach to make sure employees are not overloaded. If possible, restrict the majority of communications to real life examples such as:
- “xxxx Attack – How we are protected”
- “xxxx Attack – How you can help”
Subject lines like these demonstrate inclusion of, and reliance on, your employees—promoting contribution and self-worth at the individual level.
4. Employee Key Performance Indicators. It is worth remembering that KPIs are not targets. Simply put, if you miss a target it can be seen as failing, whereas a KPI provides trending data that you can improve upon. Here are some examples:
- Threat identification. Use ethical phishing tools to “test” if employees can identify certain threats. Identify how often employees are using the “button” to report potential phishing attacks. Do employees consider tailgating as simply being polite? Explain the danger.
- Threat reporting. Consider gamifying your training program or offering rewards to motivate employees to buy into the program, complete their training, and actively report potential issues. When phishing succeeds, let people know that if they do fail occasionally (for example, clicking on a link they thought was okay), that this is understandable, given the sophisticated nature of some attacks.
However, we also need to be clear on the importance of reporting the potential mistake immediately, and that it is not okay to hesitate or neglect to report incidents of this kind. You may also want to consider promoting the reporting of mistakes (for example, clicking a link you thought was okay) ─ reinforcing that this is welcome and will not be punished.
- Governance, risk and compliance (GRC). It is imperative that employees understand, in simple terms, the organization’s GRC policies. This provides employees with understanding, drives a sense of responsibility and helps with buy-in by making them feel part of a family. This also requires careful planning and testing because too much detail may lead to “switch off” or “tune out.”
A helping hand – and a special offer – for your program
My goal in this post was to provide you with enough information to start a conversation within your organization about the importance of an effective security awareness program to combat cybersecurity threats. Conversations are the beginning of change, and whether or not you agree with my opinions, I hope you have enough information to start the conversation. Please don’t take the risk of only doing the basics. If you want to truly change behavior and improve your organization’s security posture, commit to a cybersecurity awareness solution.
HPE has the tools, knowledge, skills, ability and experience to work with you in building an effective cybersecurity awareness program. For more information, visit this HPE Education Services page. You will also find a 7-Day FREE trial that includes a selection of our security awareness solution videos (with the option to choose up to 33 different languages and up to 7 modalities per training title).
In addition, HPE has exceptional and industry-recognized expertise and experience in the security and risk management services arena. Through HPE Advisory and Professional Services, we help organizations defend against, and recover from, cyber threats and attacks.
Learn more about how to improve your cyber-resilience:
HPE Security and Digital Protection Services
HPE Server Security and Infastructure Security Solutions
HPE Cybersecurity Awareness, Certification and Training
John F McDermott manages the HPE worldwide portfolio for cybersecurity education, training and certification. For the past five years, he has brought his 35+ years’ experience in IT Service Management best practices to the cybersecurity world.
Contact John on Linkedin and on Twitter.
Services Experts
Hewlett Packard Enterprise
twitter.com/HPE_Pointnext
linkedin.com/showcase/hpe-pointnext-services/
hpe.com/pointnext
- Back to Blog
- Newer Article
- Older Article
- Deeko on: The right framework means less guesswork: Why the ...
- MelissaEstesEDU on: Propel your organization into the future with all ...
- Samanath North on: How does Extended Reality (XR) outperform traditio...
- Sarah_Lennox on: Streamline cybersecurity with a best practices fra...
- Jams_C_Servers on: Unlocking the power of edge computing with HPE Gre...
- Sarah_Lennox on: Don’t know how to tackle sustainable IT? Start wit...
- VishBizOps on: Transform your business with cloud migration made ...
- Secure Access IT on: Protect your workloads with a platform agnostic wo...
- LoraAladjem on: A force for good: generative AI is creating new op...
- DrewWestra on: Achieve your digital ambitions with HPE Services: ...