- Community Home
- >
- Services
- >
- The Cloud Experience Everywhere
- >
- Zero Trust – A business led approach
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Forums
Discussions
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
- BladeSystem Infrastructure and Application Solutions
- Appliance Servers
- Alpha Servers
- BackOffice Products
- Internet Products
- HPE 9000 and HPE e3000 Servers
- Networking
- Netservers
- Secure OS Software for Linux
- Server Management (Insight Manager 7)
- Windows Server 2003
- Operating System - Tru64 Unix
- ProLiant Deployment and Provisioning
- Linux-Based Community / Regional
- Microsoft System Center Integration
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Receive email notifications
- Printer Friendly Page
- Report Inappropriate Content
Zero Trust – A business led approach
Security teams responsible for protecting enterprises today are constantly challenged by a rapidly changing threat landscape. Digital assets not only continue to increase in value, but also the vulnerability footprint is widening as mobile, cloud, and BYOD break down traditional forms of perimeter-based protection. Attacks change more rapidly than traditional defenses can combat, and security teams are understaffed with inefficient tools focusing more on silo-based protection methods, rather than analytics-driven insights.
Traditionally organizations have relied upon a ‘castle and moat’ approach to perimeter security, however more recently security strategies are starting to be designed around the concepts of de-perimeterization and zero trust. De-perimiterization originates initially from the work of the Jericho Forum back in 2004 and involves, per Wikipedia, ‘protecting an organization's systems and data on multiple levels by using a mixture of encryption, secure computer protocols, secure computer systems and data-level authentication, rather than the reliance of an organization on its network boundary to the Internet’. This evolved over time into what John Kindervag, whilst working for Forrester Research, introduced to the world as ‘zero trust'.
At a high level, the tenants of zero trust are fairly simple to understand:
- Focus security controls on the inside of the organizational perimeter by reducing the trust zones and removing the idea of implicit trust based upon location
- Identify users, devices and workloads and ensure all are authenticated and authorized to access resources
- Continuously monitor the environment in order to detect both advanced attacks and context changes
Or, in other words, design the network from the inside out, always verify but never trust, and log everything. If we combine those concepts with the ‘assume breach’ idea, then we conclude that the enterprise is a hostile environment, and trust needs to be continuously verified and granted or removed as appropriate.
But whereas every networking and security vendor today is pushing a zero trust solution of one kind or another, each one of these is a point solution focusing upon the strengths that the vendor focuses on – whether it’s network access control, or application allowed list, or workload verification. For an enterprise to adopt zero trust concepts holistically across the entire organization requires zero trust to be evaluated not as a series of siloed technologies, but as a new approach to security architecture. At HPE Pointnext Services we address this by introducing a business-led approach to zero trust security.
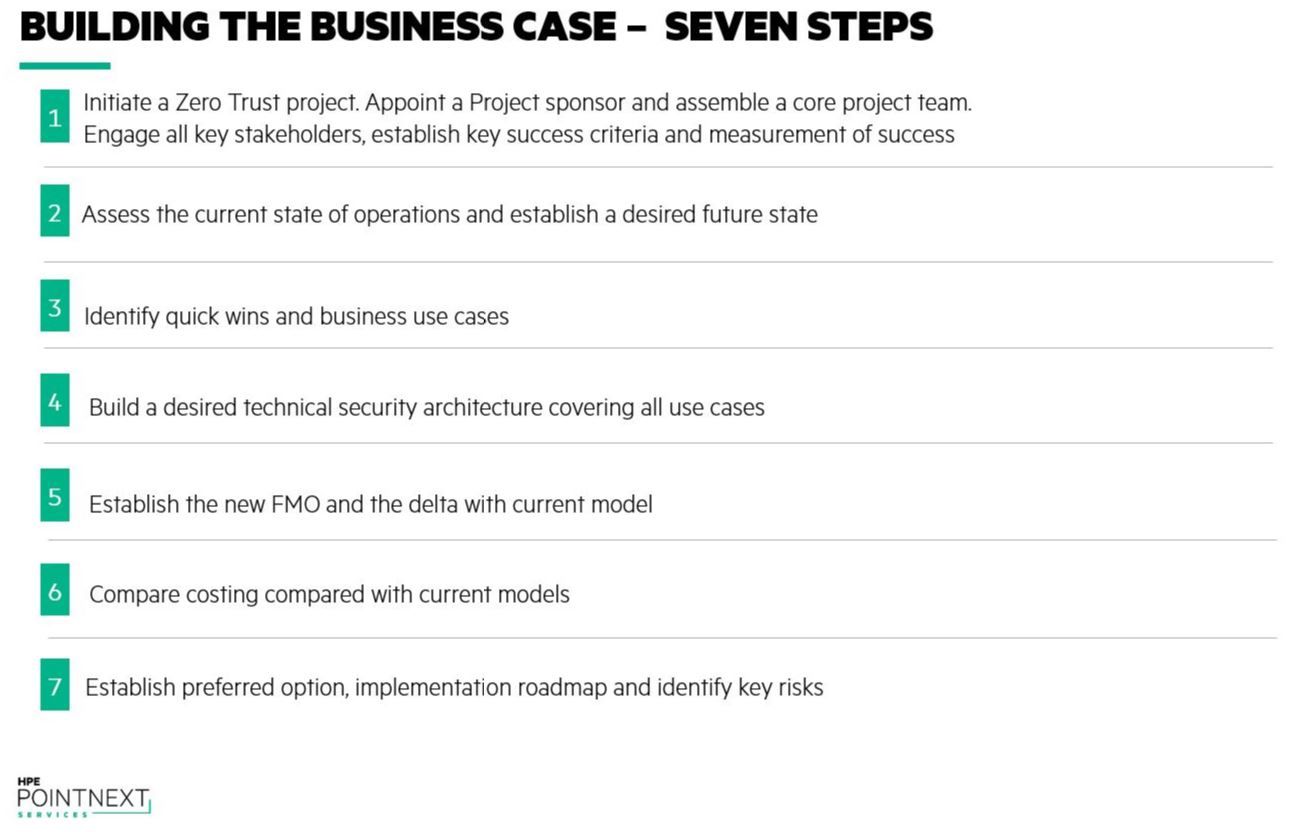
A business-led approach means taking a step back from the technology solutions, and first gaining a better understanding of why the business wants to adopt zero trust, or what the security team aims to achieve by providing a zero trust architecture to the business. The business-led approach starts with an in-depth business process review to provide visibility into the current state of operations, and then uses this background information as part of a gap analysis to establish a desired future state of operations. With this information in hand and the concepts of zero trust in mind, it becomes clearer to understand where zero trust can add value, and what some of the potential quick wins and business use cases for adopting zero trust can be.
It’s important to realize though that zero trust, just like Rome, is not something that can be built in a day. There are typically three deployment models that we see our customers considering. The first is a greenfield deployment – not common, as very few organizations are in the position to start a new security architecture from scratch, although we have seen a few cases where customers are building a new datacenter and want to apply zero trust principles to the entire DC estate. The second model is a cloud-based model, where the organization uses zero trust to build an intra-cloud trust model which in itself is a very strong driver for zero trust, and very relevant for cloud-native application development. And the final and most common approach is a hybrid model, where initial adoption in part of the business aims to create quick value and build momentum for further initiatives.
Zero trust as a concept is also much wider than the network alone, and for an enterprise wide approach to succeed should address five key tenants: device trust, user trust, application trust, data trust, and session trust. Whilst this goes beyond the ‘traditional’ opinion that zero trust is something best dealt with at the network level, expanding the concept to all levels of the technology stack enables the strategy to be addressed with a much more holistic approach.
So the initial current state assessment needs to take a number of items into consideration to get a comprehensive view of the current environment, including reviewing business processes, current asset inventory, security controls and architecture assessment, security governance model and IT security strategy, and last but not least any future business and growth initiatives. The outcome of the assessment will be the beginnings of a zero trust strategy for the organization, following four main pillars:
- Future proof – a new way of security policy enforcement to provide stability against changes in IT or business strategy
- Risk aware – inclusive of many initiatives and use cases, all with the aim of reducing organizational risk
- Flexible – defined by the right level of detail, and leaving space to build upon and adapt as the business evolves
- Proven design – a ‘security by design’ approach following industry architecture best practices, organizational objectives and supported by senior stakeholder buy in from the start
HPE Pointnext has already helped customers around the world to build business-centric security strategies for zero trust with our Security Analysis and Roadmap Service. If you’d like to find out how we can help your business, please reach out to your local Pointnext representative, or click on any of the resources below.
HPE Pointnext Services - Security Consulting Services
Enterprise.nxt article on Zero Trust
SimonLeech
Simon is Deputy Director in the HPE Global Security Center of Excellence. He is responsible for bringing together cyber experts from across HPE to support the vision of an open and secure edge to cloud platform, and works with HPE's enterprise customers worldwide, evangelising the strategy of HPE Global Security and articulating our ‘Secure by Design’ and ‘Operationally Secure’ principles. Simon has worked in the IT security industry for over 25 years and is well versed in many areas of IT security, including network security, operational security, malware, cyber threats, vulnerability management, hybrid cloud security, container security, zero trust security, and cyber resilience. Simon is active on Twitter as @DigitalHeMan
- Back to Blog
- Newer Article
- Older Article
- Deeko on: The right framework means less guesswork: Why the ...
- MelissaEstesEDU on: Propel your organization into the future with all ...
- Samanath North on: How does Extended Reality (XR) outperform traditio...
- Sarah_Lennox on: Streamline cybersecurity with a best practices fra...
- Jams_C_Servers on: Unlocking the power of edge computing with HPE Gre...
- Sarah_Lennox on: Don’t know how to tackle sustainable IT? Start wit...
- VishBizOps on: Transform your business with cloud migration made ...
- Secure Access IT on: Protect your workloads with a platform agnostic wo...
- LoraAladjem on: A force for good: generative AI is creating new op...
- DrewWestra on: Achieve your digital ambitions with HPE Services: ...