- Community Home
- >
- Partner Solutions and Certifications
- >
- Alliances
- >
- Introducing: Extreme Search for Splunk from HPE an...
Categories
Company
Local Language
Forums
Discussions
Forums
- Data Protection and Retention
- Entry Storage Systems
- Legacy
- Midrange and Enterprise Storage
- Storage Networking
- HPE Nimble Storage
Discussions
Forums
Discussions
Discussions
Forums
Discussions
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Discussion Boards
Community
Resources
Forums
Blogs
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Receive email notifications
- Printer Friendly Page
- Report Inappropriate Content
Introducing: Extreme Search for Splunk from HPE and AMD
The Cybersecurity Challenge
Large organizations are facing the multiple challenges of exponentially growing data, large and vulnerable enterprise networks, increasing numbers of cyber intrusions, and finite resources and personnel available for IT operations and cybersecurity.
Companies, government agencies, and other large organizations have seen an increasing number of cyberattacks with major impacts on finances, mission, and reputation. Pandemic-driven changes in work patterns increased the attack surface and strained networks and IT admins as workers quickly shifted to remote access and “bring your own” technology.
Cybersecurity incident response (IR) teams are understaffed and overworked. On average, intrusion detection times range from 12 to 60 days, and containment takes an average of 287 days. Security teams are dealing with a high number of alerts and false positives, which results in alert fatigue. According to a recent survey report, 70% of companies face over 100 security threat alerts per day, and large enterprises can see thousands. An IBM study found that breach costs were 80% lower for companies using automated security tools.
An Added Challenge for U.S. Federal Customers
To add a further challenge, the U.S. government cybersecurity Executive Order 14028 of May 2021 requires improved data retention, processing, and long-term storage. Under this EO, Federal agencies must retain logs and cyber data for 12 months, resulting in multi-petabyte storage requirements that current indexing and search tools cannot meet within reasonable time and cost parameters. EO 14028 also requires agencies to process data in real time and have rapid search capability for over a year’s worth of historical data, which in some cases is an extremely large volume of data. Therefore, government agencies are scrambling to add high-volume search and storage capability to meet these requirements and improve their cybersecurity incident response posture.
The Solution: Extreme Search for Splunk
Extreme Search allows Enterprise IT to analyze all IT infrastructure event logs more completely, including the application of artificial intelligence and machine learning (AI/ML) algorithms. The Extreme Search solution delivers a future where automated tools accelerate incident detection and response, and operators have a comprehensive view of their IT operations. By processing data as it arrives – in parallel with Splunk, and by making months or years of historical data immediately searchable, incidents can be detected, analyzed, and remediated rapidly. Extreme Search may be integrated with existing cybersecurity tools and enhances the performance of those tools, and can be a critical part of elevating the overall cybersecurity posture of an Enterprise.
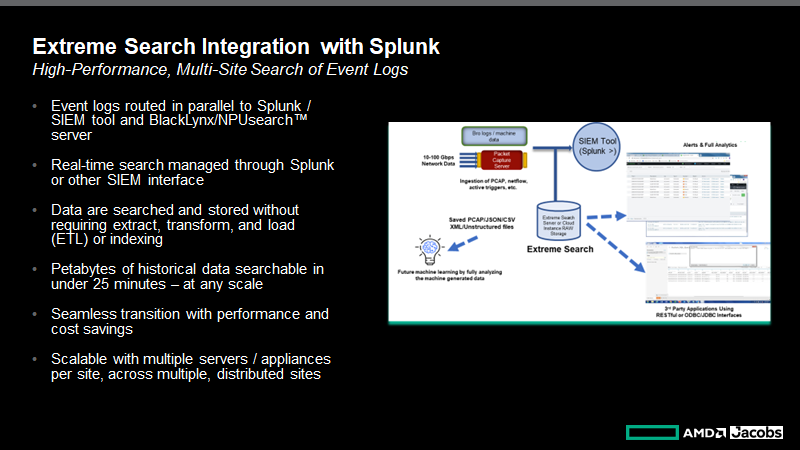
Furthermore, Extreme Search enables distributed, multi-site analytics that Splunk simply does not offer on its own, and delivers unparalleled performance – returning query results across petabytes of data in less than 25 minutes. Surprisingly, Extreme Search delivers these benefits at a lower total cost of deployment and operation than brute force indexing methods that are incapable of delivering rapid, multi-site results.
Extreme Search Architecture
Extreme Search is implemented via a parallel integration architecture. This means that event logs are forwarded to the both the Extreme Search Server and Splunk simultaneously. CyberLynx from Jacobs/BlackLynx is the underlying technology that interfaces to Splunk and to the Extreme Search server, enabling an operator to launch Extreme Search queries and receive results through the familiar Splunk user interface. This approach enables a seamless transition and introduction of Extreme Search.
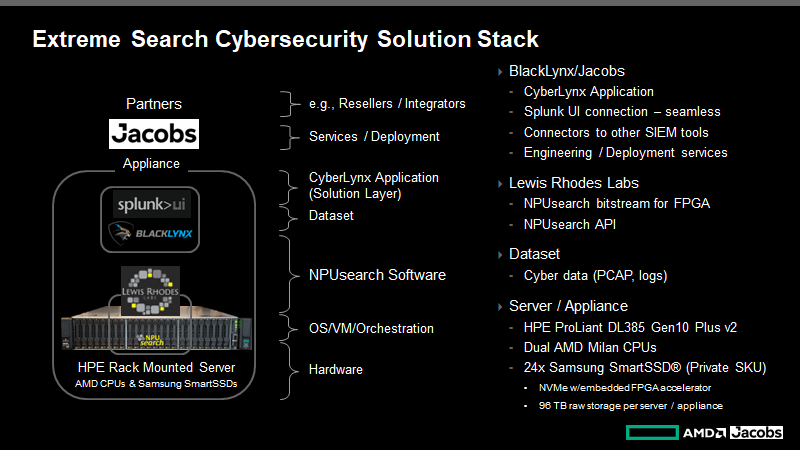
Extreme Search incorporates several innovative, industry-leading components into its architecture, which together provide a solution with peerless capabilities and performance:
- The CyberLynx tool created by Jacobs (through their BlackLynx acquisition) analyzes the incoming data stream and provides alerting back to the Splunk dashboard.
- Samsung’s SmartSSD® was produced in collaboration with AMD (through their acquisition of Xilinx) and features a Samsung NVMe SSD with an embedded Xilinx FPGA for acceleration. Current drive capacity is 4TB raw per drive.
- The Neuromorphic Processing Unit search tool (NPUsearch™), invented by Lewis Rhodes Labs, enables data to remain on the SmartSSDs to be searched in place, which dramatically enhances performance – often by orders of magnitude.
- Extreme Search is hosted on industry-standard, high-capacity HPE ProLiant Gen10 Plus v2 servers, each featuring dual AMD Milan processors and 24 factory-integrated SmartSSD drives.
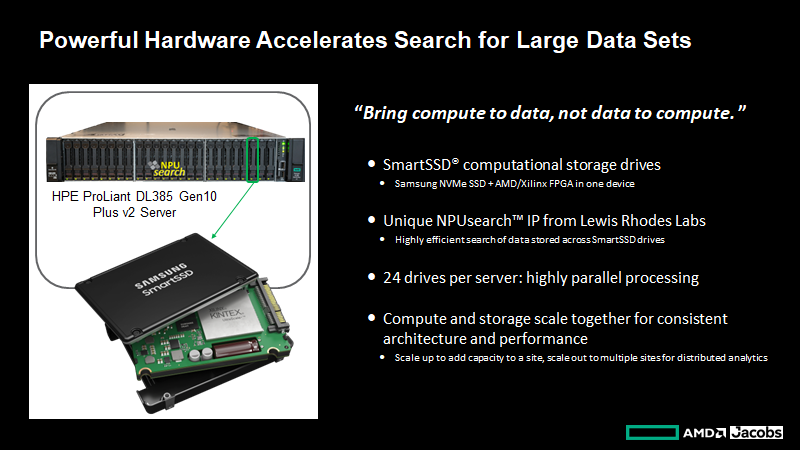
What sets Extreme Search apart?
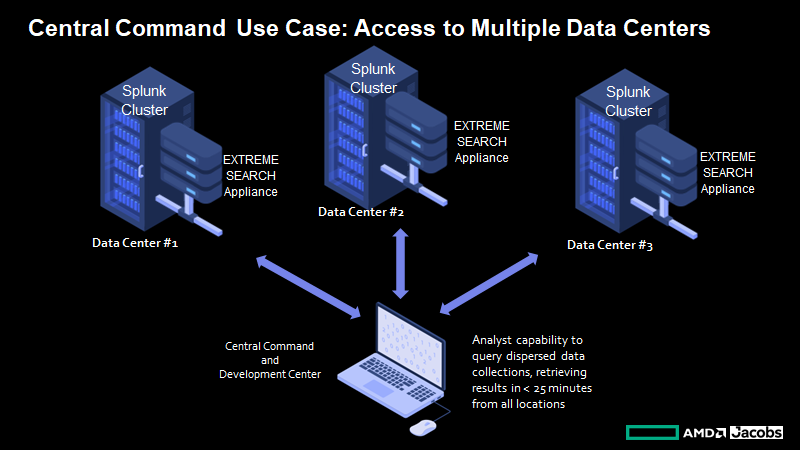
- Distributed, Multi-site Analytics – With Extreme Search, gain complete visibility and searchability of all cybersecurity data, network traffic statistics, and log data. Raw data is searchable across sites without indexing or extraction, transformation, and loading (ETL). Log data does not have to be copied and aggregated centrally to have enterprise-wide visibility. Data are searched even before ingestion into Splunk. Extreme Search sits alongside Splunk infrastructure as an accelerator – not a new interface. There’s no new software for operators and analysts to learn, and the transition to Extreme Search is seamless with zero risk to the enterprise.
- Accelerated Performance, Regardless of Scale – Extreme Search server appliances are installed at each site based on the size of that site’s environment. Because of the architecture design, query results may be returned on any amount of data in less than 25 minutes, guaranteed. As sites grow and new sites are added, compute resources are added site-by-site, which sustains the guaranteed performance of the entire solution.
- Lower Total Cost to Implement and Operate – The architecture recommended today by Splunk and other SIEM tools requires large, expensive index servers to achieve acceptable performance. Because the Extreme Search solution avoids aggregation and expensive indexing/re-indexing, and deploys resources to the sites where logs are created, it is less expensive overall – even when accounting for all necessary software, deployment services, and ongoing operation.
For more information about Extreme Search for Splunk from HPE and AMD, please contact your HPE Account Manager.
(For now, because this is a "private" part number requiring direct HPE sales involvement, it is available in the U.S.A. only. International customers, please let your local representative know of any interest in this technology so you may be notified when it is generally available outside of the U.S.A. Thank you.)
Sources
Sheridan, Kelly. 77% of Businesses Lack Proper Incident Response Plans. Dark Reading. March 14, 2018. https://www.darkreading.com/attacks-breaches/77-of-businesses-lack-proper-incident-response-plans
Lee, Robert. 2021 SANS Cyber Threat Intelligence Survey Results. SANS. January 19, 2021. https://www.sans.org/webcasts/2021-cyber-threat-intelligence-cti-survey-results-116475/
IBM, Cost of a Data Breach Report 2021, https://www.ibm.com/security/data-breach
Red Canary, “The State of Incident Response, 2021.” https://redcanary.com/resources/guides/the-state-of-incident-response-2021/
IBM, X-Force Threat Intelligence Index 2021. https://www.ibm.com/downloads/cas/M1X3B7QG
IBM, Cost of a Data Breach Report 2021, https://www.ibm.com/security/data-breach
- Back to Blog
- Newer Article
- Older Article
- mhardi01 on: The time is now for Microsoft Exchange SE on HPE h...
- JoeV_The_CT on: Streamline AI Workloads with HPE & NVIDIA
- iVAN LINARES on: Curious about Windows Server 2022 downgrade rights...
- HPEML350_22 on: Windows Server 2022 is here: how to implement it o...
- testingis on: How are you going to license that new server? A st...
- wowu on: Pick up the pace
- nice345 on: Don’t let the time slip away
- vmigliacc on: Frequently asked questions about HPE solutions for...
- MassimilianoG on: What are downgrade and Down-edition rights for Win...
- harithachinni on: Coffee Coaching's "Must See" Discover Virtual Expe...
-
Accenture
1 -
Citrix
13 -
Coffee Coaching
345 -
Event
71 -
Microsoft
210 -
Red Hat
7 -
SAP
40 -
Strategic Alliances
103 -
Veeam
8 -
VMware
34
